1. What is a Proxy?
- Definition: A proxy acts as an intermediary between clients on a network and the internet, essentially serving as a middleman for data exchange.
- Function: It retrieves data on behalf of clients, enhancing security and performance by controlling and optimizing traffic flow.
- Use case: Consider a corporate network with multiple computers accessing the internet. A proxy server sits between these computers and the internet, intercepting requests and fetching data on their behalf.
-
Benefits:
- Enhanced security through traffic regulation and blocking of harmful websites.
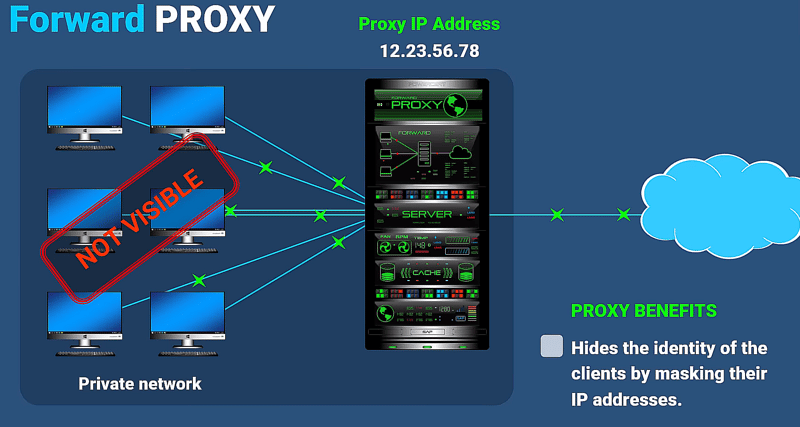
- Anonymity for clients by masking their IP addresses.
- Activity logging for organizational monitoring. Some organizations would like to know what websites their clients are visiting and for how long, using proxy they can keep track of those.
- Bypassing restricted content. Some organizations like schools and governments, may restrict access to certain websites. But by using a proxy you may be able to bypass those restrictions and access those restricted websites. Just like we do, in our college 😏.
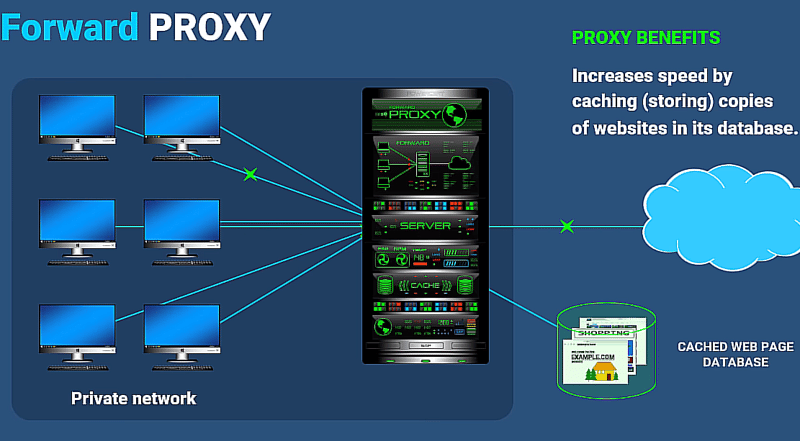
- Speed optimization through caching frequently accessed websites. Because a proxy can cache or store copies of websites that are frequently used by their clients. So instead of the proxy server fetching the same websites out on the internet over and over again, those websites can be stored in the proxies cache database instead.
2. Understanding Forward Proxies:
- Role: Positioned within a private network to regulate outgoing traffic, serving as a gatekeeper between internal clients and the internet.
- Function: Acts as the guardian of the network, intercepting outbound requests from clients and fetching data from the internet on their behalf.
- Example: In a corporate environment, a forward proxy ensures that all outgoing web requests from internal users are routed through the proxy server. This helps enforce security policies and access controls.
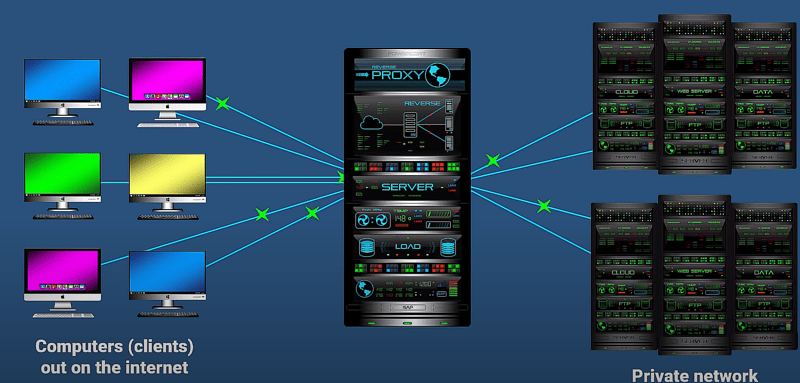
3. What is a Reverse Proxy?
- Definition: A reverse proxy manages incoming traffic to servers within a private network, serving as a buffer between external clients and internal servers.
- Purpose: Provides a single entry point for external communication, enhancing security and performance by shielding servers from direct exposure to the internet.
- Use case: Imagine a web server hosting an e-commerce website. A reverse proxy sits in front of this server, intercepting incoming requests from clients and distributing them to the appropriate backend servers.
So for example -
here we have a private network with servers. And servers are just powerful computers that clients connect to if they want to access certain data such as retrieving a website, or access a database, and so on.
These servers will accept incoming connections from clients outside its network from the internet. So when a client on the internet wants to access certain data on these servers, they will directly connect to one of these servers.
But having direct access to a server, can be a security risk and open the door for hackers to create problems on these servers.
So this is where a reverse proxy can help. By using a reverse proxy on this network it creates a single point of entry that can regulate incoming traffic.
So now when computers from the internet want to access data on these servers, they no longer directly communicate with the servers, they only communicate with the reverse proxy server and then the reverse proxy will fetch the data from the server and then direct it back to the computer.
-
Benefits:
- Enhanced security by hiding server IP addresses. So when a computer on the internet wants to access a website for example, on one of these servers, they will not see the IP address of the server, they will only see the IP address of the reverse proxy.
- Protection against malicious traffic, including DDoS attacks. A DDOS attack is a simultaneous attack from a bunch of computers over the internet targeting a specific server by its IP address. And a reverse proxy is an effective defense against this type of attack because it will sit between the client and the server, acting like a buffer to stop the attack from ever reaching the server and it will also hide the server's IP address.
- Load balancing to distribute traffic evenly across multiple servers. The reverse proxy can act like a traffic cop that is used to evenly distribute traffic to multiple servers so that certain servers don't get overloaded with traffic.
*So in short, a forward proxy is there to protect clients, while a reverse proxy is there to protect servers. *
4. Differentiating Forward and Reverse Proxies:
- Forward Proxy: Safeguards clients by managing outbound traffic, typically implemented within a private network to control and monitor internet access.
- Reverse Proxy: Protects servers by regulating incoming traffic, acting as a shield against potential security threats, and optimizing server performance.
- Example: A forward proxy protects internal users from accessing malicious websites or content by filtering outgoing traffic. Conversely, a reverse proxy safeguards web servers from direct exposure to the internet, preventing attacks and ensuring efficient resource utilization.
Here's a list of both forward and reverse proxies commonly used for various purposes:
Forward Proxies:
- Squid
- Apache HTTP Server (mod_proxy)
- Nginx
- HAProxy
- Varnish
- Polipo
- Tinyproxy
- Privoxy
- Dante
- CCProxy (Windows-based)
Reverse Proxies:
- Nginx
- Apache HTTP Server (mod_proxy)
- HAProxy
- Pound
- Traefik
- Envoy
- Caddy
- Varnish
- Squid (can be configured as a reverse proxy as well)
- Microsoft Application Request Routing (ARR)
Each of these proxies has its own strengths and weaknesses, so the choice depends on factors such as performance requirements, features needed, ease of configuration, and compatibility with your existing infrastructure.
Conclusion:
Proxies and reverse proxies are indispensable tools for securing and optimizing network traffic in today's digital landscape. Whether safeguarding client privacy or protecting server resources, these solutions play critical roles in maintaining a secure and efficient network environment.