Mastodon, the free open source self-hosted federated social network platform, has been witnessing a surge of interest and new users due to the recent developments on Twitter — specifically that of verifying accounts.
One of the interest areas driving users to Mastodon has been the ability to verify their account identity and convey a sense of authenticity for the account. This provides a way to help prevent spam accounts, bots, and other issues related to fake news.
How to verify your Mastodon account
With Twitter, the process of identifying accounts and granting a blue checkmark to convey the meaning of a verified account, has been left solely to the discretion of the platform itself.
The entire process and its requirements were unknown to anyone outside of the company. Mastodon, however, simplifies account verification by empowering the account owner to accomplish it.
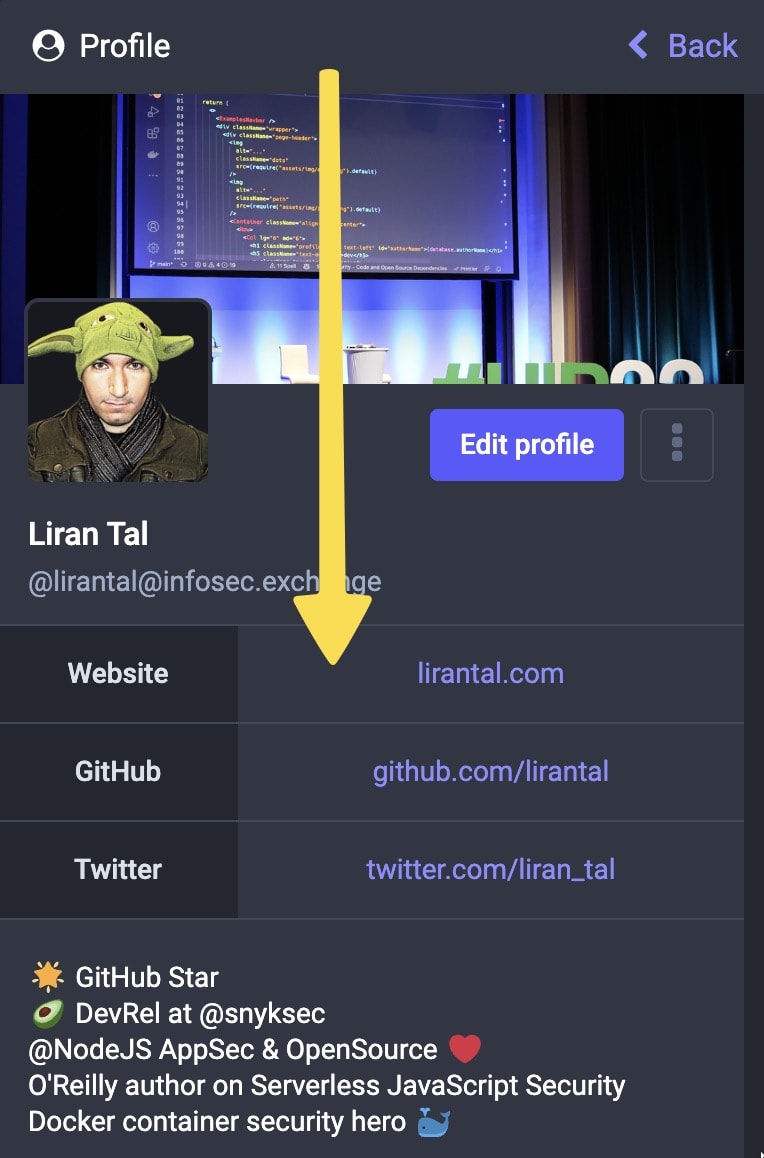
Step 1: What does a verified Mastodon account look like?
In the following screenshots, you can see my own unverified Mastodon account (Liran Tal) next to my friend Matteo Collina’s account, which showcases the verified badge next to their website.
In this tutorial, we’ll use my profile to walk through the process of verifying a Mastodon account, in order to gain a verification check mark and provide some legitimacy to the account. Let’s get started.
Step 2: Find your Mastodon account verification link
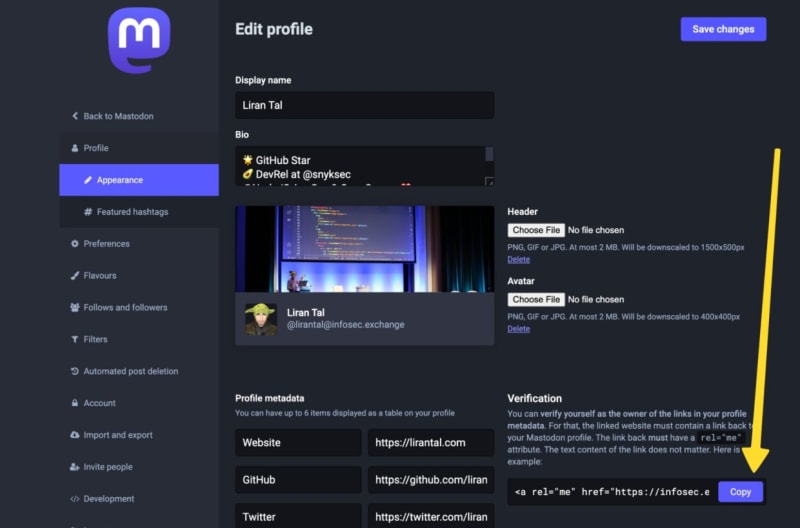
If you go to the Edit profile pages and scroll down, you’ll see a list of key and value input boxes under Profile metadata. These allow you to customize the links that appear in your profile.
Next to these, you’ll see a Verification section — which provides you with a line of text to copy and then paste into one of the website links you added.
Step 3: Add verification information to your website
If you are in control of the website that you linked in the Profile metadata section, then changing the website’s content will be used as proof of ownership.
The process then depends on how your website is built. The method of updating its content will vary depending on whether it is a WordPress blog, a Next.js powered website, or a completely static website.
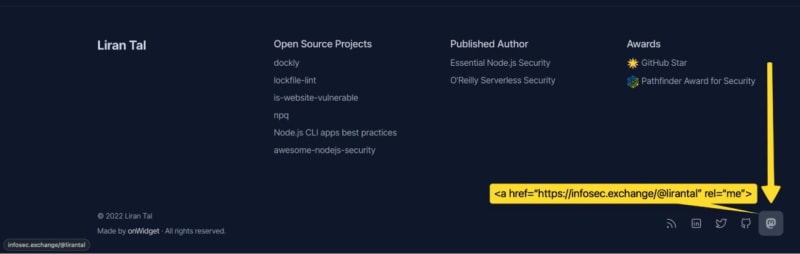
What’s important is that the website’s returned HTML has an anchor tag with the rel attribute that equals to me, and includes an href value that links back to your Mastodon profile page.
For me, that anchor HTML link is as follows. I’ve also added it to the footer of my website, as you can see in the screenshot below:
html
<a rel="me" href="https://infosec.exchange/@lirantal">Mastodon</a>
Step 4: Trigger a profile update and wait for the verification to kick in
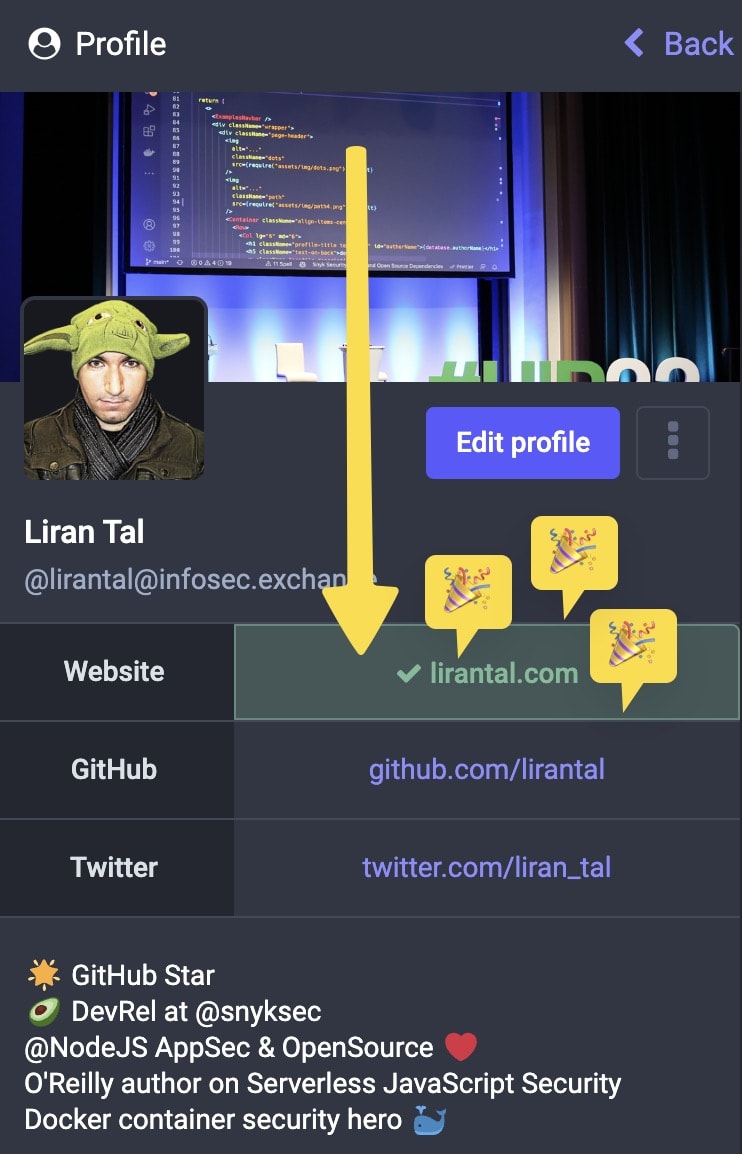
Once added, make sure that a new website version, featuring your verification link, has successfully deployed. Then, edit your Mastodon account profile, and hit the Save button in order to trigger the verification action.
It might take up to hours, but in most cases, you should immediately see the verified status:
The security aspects of being verified on Mastodon
Many articles on the topic of verifying Mastodon accounts stop at the point of taking you through the process, neglecting to weigh in on what exactly was verified and its security implications.
1. On Mastodon you verify links ownership, not identity
The official Mastodon documentation has a page on account setup, which appropriately describes what others refer to as “verified Mastodon accounts”.
Though nuanced, these details are important to capture nonetheless. In the process outlined here, we haven’t actually verified the Mastodon account, but rather verified a link on our profile page that is tied to a website we were able to modify.
In fact, this is very similar to how ownership of a domain happens with the help of domain name servers — which require you to create a new temporary DNS record such as TXT, hold a specific value, and query to verify it.
This begs the following question…
2. What if someone takes control of a verified website?
What if someone was able to exploit a security vulnerability in your website and, through a sort of cross-site scripting (XSS) method, dynamically add or modify these links? They could introduce confusion in terms of whether an account is genuine, or convey a “verified” account status on their own fake account.
Other information security concerns about Mastodon
Mastodon, like every other software, is prone to security bugs — and those can be quite severe too when the impact is social media, fake news, and violation of privacy in our current information revolution.
One concrete example is a recent security disclosure by researcher Gareth Heyes, who reported a security vulnerability that allowed malicious users to steal passwords on the infosec.exchange Mastodon instance. The HTML filter bypass was reported to the Mastodon project on November 8th, 2022, and was fixed within a week by the 15th of November, 2022.
With Mastodon growing in popularity, it only makes sense that more security researchers will lend their expertise to review the open source project and instances’ configuration to assess security vulnerabilities. We can only hope they will handle their security findings in an ethical way without putting users at risk.
As a final note of recommendation for those who are actively seeking refuge on Mastodon for their social media interactions — Direct Messages, often abbreviated as DMs, are not encrypted by default on instances. This means that the messages you send and receive privately are exposed to Mastodon instance administrators. A long standing GitHub issue dating back to 2018 has brought up this concern, and we hope it gets resolved soon with end-to-end encryption being the default.