To read this full article, click here.
Amidst the ever-evolving landscape of cybersecurity, the recent revelation of a zero-day vulnerability in Fortinet's FortiOS serves as a stark reminder of the constant cat-and-mouse game between defenders and attackers.
Staying ahead of potential security threats isn’t just a best practice; it's a necessity. For developers, the challenge lies not only in identifying vulnerabilities but in doing so proactively, especially when it comes to zero-day exploits. In this blog post, we'll explore how New Relic application performance monitoring (APM) empowers developers to create zero-day vulnerability alerts, offering a robust solution to enhance security postures without the need for extensive scanning.
Developers are often tasked with managing the delicate balance between agility and security. New Relic recognizes this challenge and provides a comprehensive set of tools to streamline the process. Today, we'll delve into two key capabilities—alert conditions and policies within the New Relic platform and the integration with Vulnerability Management—that enable developers to create targeted alert rules and effortlessly control their security posture.
Let's embark on a journey through these capabilities, exploring how they equip developers to receive timely notifications on specific common vulnerabilities and exposures (CVEs) and maintain an up-to-date understanding of their application's security status. Additionally, we'll unravel the magic of the New Relic Database (NRDB) and the Environment Snapshot tab, where all changes, including library modifications, are meticulously recorded. Join us as we navigate the realm of zero-day vulnerability alerts, unlocking the full potential of New Relic APM for developers.
What exactly are zero-day vulnerability alerts?
Before we dive deeper into the advantages of zero-day alerts, let's understand what zero-day alerts are.
Zero-day alerts are crucial in software development. Picture this: You're in the midst of coding, and suddenly, an alert pops up—a zero-day vulnerability is detected. It's not just any vulnerability; it's one that nobody knew about until now. Zero-day alerts are like unexpected guests—they demand immediate attention.
These alerts signal the emergence of previously unknown vulnerabilities or security threats. Unlike known issues with patches, zero-day vulnerabilities are wild cards, demanding swift action and vigilance.
Some developers may think that once their source code has been scanned for vulnerabilities at build time, their job is done. However, once the application or service is in production, on average up to three years later, a vulnerability exposure will be disclosed that was not known when the source code was originally scanned. Finding and fixing these vulnerabilities is often a crisis moment for many organizations.
Zero-day alerts aren't just notifications; they're urgent calls to action. They remind us of the ever-changing digital landscape, urging us to stay vigilant and responsive in our defenses. They're about staying ahead, anticipating the unexpected, and protecting our digital realms from the unknown. In software development, they're the plot twists that keep us on our toes, ready to tackle surprises head-on.
Unveiling the developer advantages
As developers, embracing a proactive security posture is not just a choice; it's a strategic advantage. New Relic APM and Vulnerability Management provide a dynamic duo that equips development teams with an array of benefits, revolutionizing the way we approach security in the software development lifecycle.
Here are some benefits of this approach:
Real-time alerts on zero-day events:
Traditional scanners operate on scheduled scans, often missing the critical moment when a zero-day library event occurs. With APM and Vulnerability Management, developers receive real-time alerts, ensuring swift responses to potential vulnerabilities. This capability surpasses the limitations of scanners, providing a level of immediacy crucial in today's fast-paced development landscape.Broad visibility across your entire environment:
The APM agent acts as a vigilant sentinel, offering broad visibility across your entire environment. It goes beyond individual applications, providing insights into what's running, where it's running, and the security status across thousands of applications. This holistic perspective empowers developers with a comprehensive understanding of their application landscape, surpassing the capabilities of traditional scanning tools.Instant impact assessment:
Imagine having immediate answers to critical questions: Where are we affected? What is the impact? How do I fix it? APM and Vulnerability Management not only provide alerts but also enable developers to assess the impact instantly. Automation further streamlines the process, allowing for quick decision-making and efficient remediation. Developers can stay informed about the status of remediation efforts assigned to specific problems, fostering a culture of accountability and transparency.Continuous zero-day analysis:
While scanners offer point-in-time snapshots that may become outdated with changes to code bases or environments, APM and Vulnerability Management provide continuous analysis. Every change in your environment is captured and assessed in real time. This ensures that your security posture isn’t just a momentary snapshot but an ongoing, adaptive process that evolves with your application.Proactive prevention and collaboration:
APM and Vulnerability Management go beyond mere detection; they empower developers to proactively prevent issues. Receive notifications to avoid calling a specific library due to the need for an upgrade, preventing the creation of a stack of baseline library vulnerabilities associated with multiple entities. This proactive approach not only mitigates risks but also minimizes the high cost of addressing vulnerabilities down the road.Automatic detection and fixing of new dependencies:
Stay ahead of the curve by automatically detecting and fixing vulnerabilities in new dependencies. APM and Vulnerability Management enable developers to address issues before they propagate, often resolving vulnerabilities before the security team is even aware of the issue. This level of automation not only enhances security but also optimizes development workflows, allowing teams to focus on innovation rather than firefighting.
Now, armed with the knowledge of these substantial benefits, let's explore the practical steps to harness these capabilities and create zero-day vulnerability alerts using New Relic APM, alerts and applied intelligence.
Creating targeted alert rules with New Relic
As developers, vigilance is key when it comes to security, and New Relic APM provides a powerful ally in this pursuit. With the alerts and applied intelligence capabilities, developers can seamlessly create tailored alert rules to receive timely notifications on specific CVEs.
Imagine a scenario where a critical CVE is identified, and swift action is necessary. New Relic APM allows you to navigate to the Alert Conditions tab, where you can set up customized conditions based on specific parameters such as error rates, response times, or throughput. By integrating Vulnerability Management into this process, you can extend your alert rules to cover vulnerabilities, making your security response not just rapid but also finely tuned to the unique characteristics of your application.
Let's break it down:
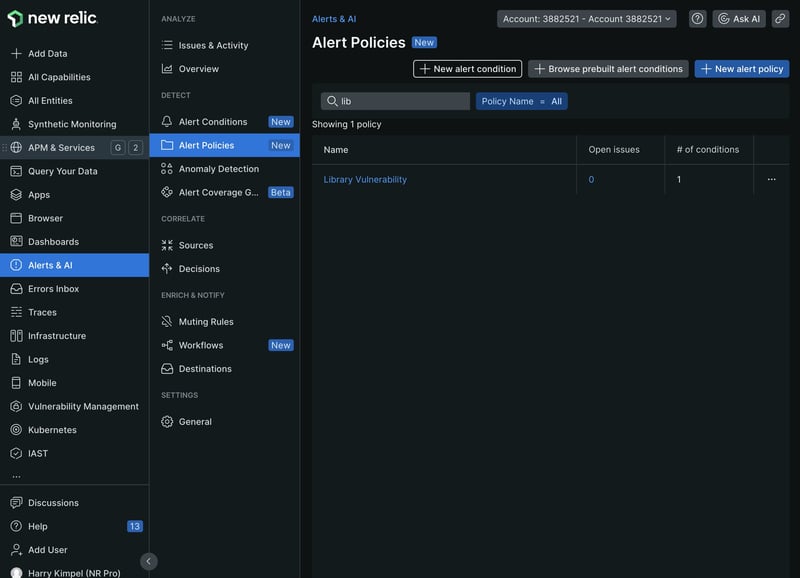
- Navigate to Alerts & AI in the New Relic platform:
-
Locate the Alert Policies section to access the powerful alerting capabilities of the New Relic platform.
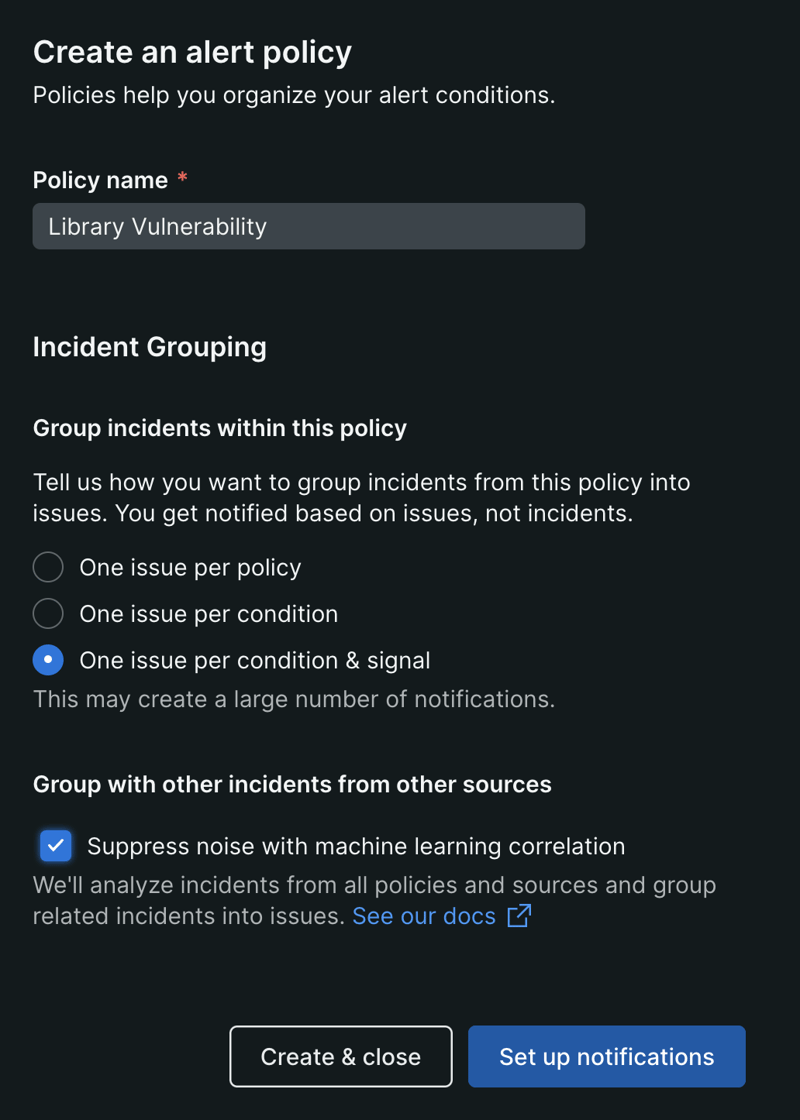
- Create a New Alert policy:
-
Define a new alert policy tailored to your application's needs. This policy will serve as the foundation for your customized alert rules.
- Create an alert condition
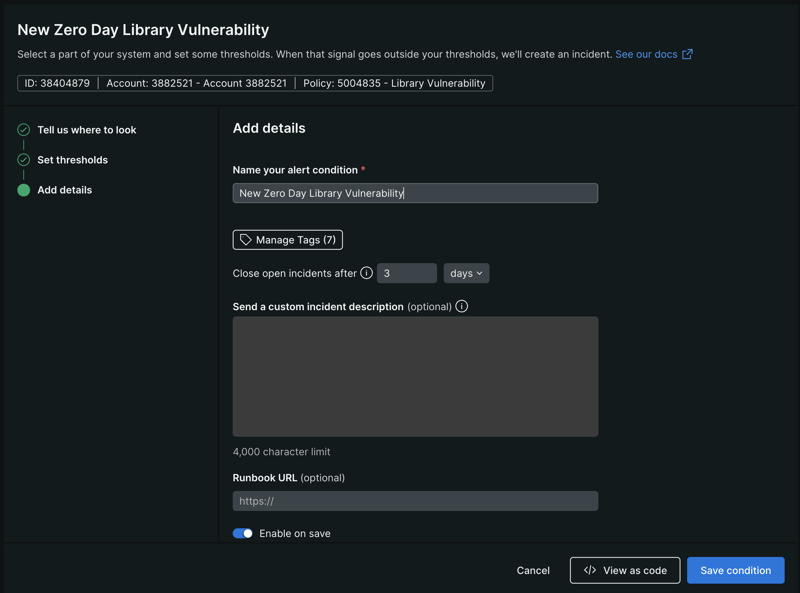
Provide a name “New Zero Day Library Vulnerability”
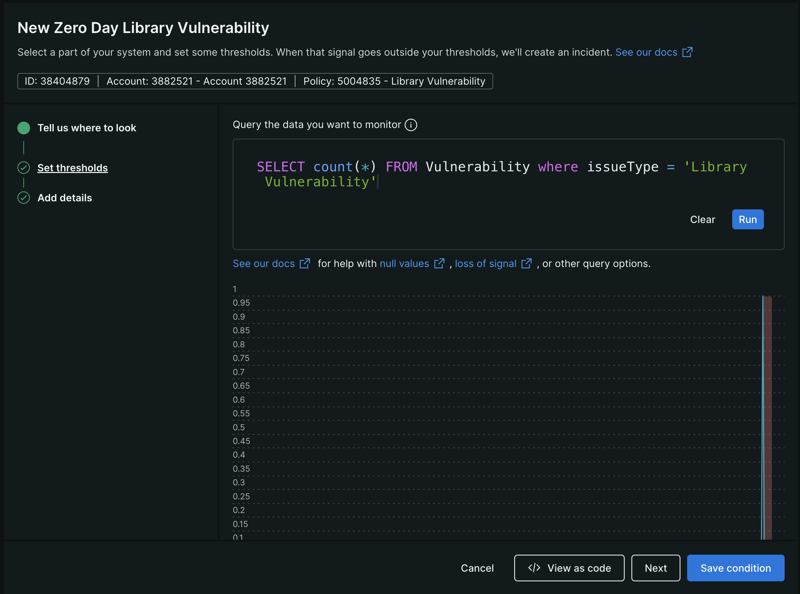
-
Enter the New Relic Query Language (NRQL) query
SELECT count(*) FROM Vulnerability where issueType = 'Library Vulnerability'
-
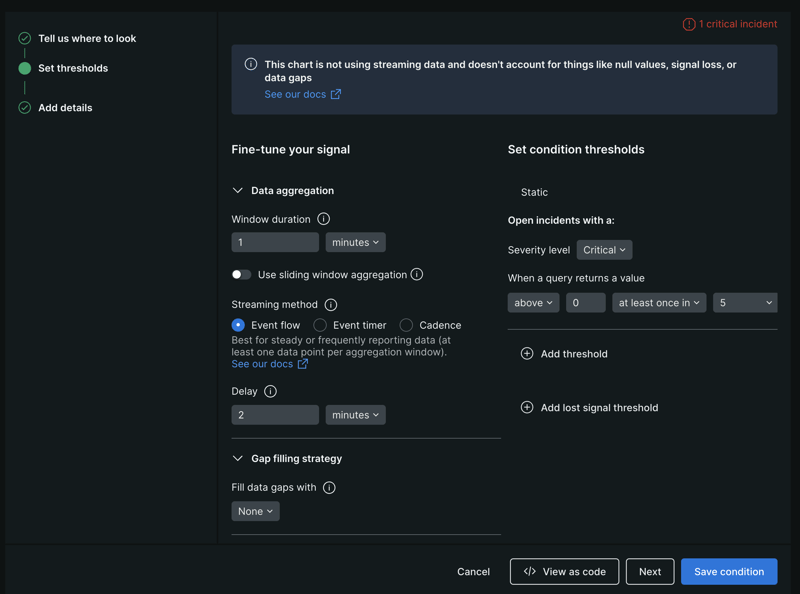
Define thresholds. The important aspect in this section is “Open incidents with a:”. Here you’ll specify when to trigger a critical incident. Of course, we want to get alerted as soon as the query returns a value above 0 at least once in the given time window.
-
Add details. Provide a name for your alert condition and adjust the other settings as you see fit.
By following these steps, you empower your development team with a proactive stance against vulnerabilities, receiving notifications that are not just timely but also precisely aligned with your application's unique security requirements.
Next steps
Next, let's explore how New Relic goes beyond alerting by providing a comprehensive record of all changes, ensuring a thorough understanding of your application's security landscape.
To make it even easier for you to get started, I’ve created a GitHub repository that contains a Terraform script to create a sample alert policy and condition using the above concept. Alternatively, it also contains a NerdGraph query (New Relic's GraphQL API) that you can use along with New Relic’s New Relic's Graphiql Explorer.
Get started with your free New Relic account today.