With the Mojave update to macOS, Apple has introduced a couple of restrictions on what your apps are allowed to do. If you are the developer of apps that are downloadable outside of the Apple App Store you need to be wary of these restrictions.
The two new restrictions I will be talking about in this article is the Automation and Full Disk Access restrictions. The new restrictions on Automation will prevent apps from scripting other apps through AppleScript and the Full Disk Access will prevent apps from manipulating files owned by other apps.
In these scary times of the World Wide Web it is probably a very good idea for Apple to add these restrictions to the OS. But I do think that Apple has done it in a not very user friendly way, especially when it comes to Full Disk Access.
Full Disk Access
Unless the user has specifically given Full Disk Access to your app, it is not allowed to change files not owned by itself. If you try you will get an error telling you that it is not allowed.
That is a good thing! You should not be allowed to mess up things for everybody else.
The problem is that Apple has not given us an API to prompt the user to give access. There is not even an API for checking if we have access to a file.
The user is in for a bad experience because they have to manually give Full Disk Access to our app in the Security & Privacy panel.
That is absolutely terrible! Most users I have met have no clue on how and where to find the .app file or the security center. You have to write a thorough user guide to help the users and who reads user guides these days?
Fortunately, Apple has done a better job when it comes to Automation.
Automation
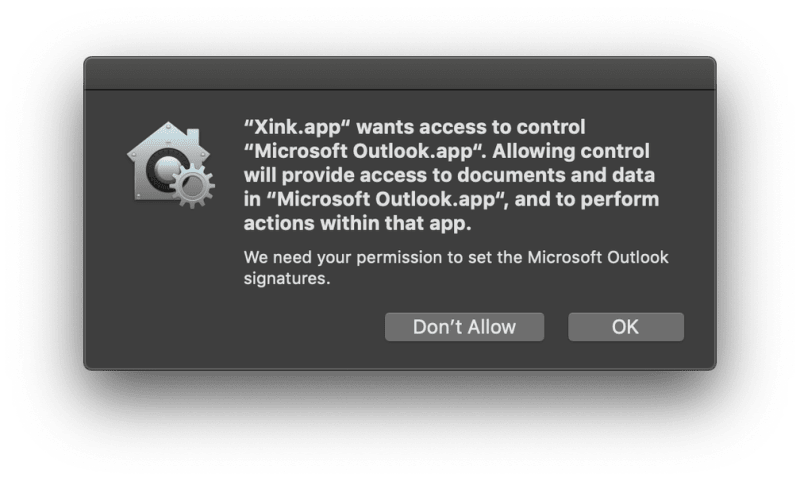
Mojave will stop you if your app tries to access another app through AppleScript. This too is a good thing. Imagine the mess a malicious app could do!
Fortunately, Apple has done better when it comes to usability than they did with Full Disk Access. All you as a developer need to do is add the key NSAppleEventsUsageDescription to your app’s plist.info file with a description.
The first time the app tries to script another application, the runtime will automatically prompt the user for permissions.
Of course, you have to make sure that your app gracefully fails if the user denies permissions.
If the user grants the permission your app is added to the Automation tab under Privacy & Security settings.
Note how there is no way to add an app manually to the Automation tab. Shame on you, Apple!
You can clear the entire list from the Terminal:
tccutil reset AppleEvents
Hardened build
Beware that if you need a hardened build for notarisation, the good people of Apple have in all their glory decided to completely ignore the NSAppleEventsUsageDescription property unless you also specifically enable Apple Events in the Capabilities tab in Xcode.
Conclusion
While I think it is a good idea to restrict permissions for macOS apps installed outside of the App Store, I do believe that the user experience is terrible. How many users know the consequences of granting permissions to full disk access or to Apple Events? Nobody knows what those terms mean. Apple is also making it very hard for developers to properly instruct the app users.