With APIs responsible for sending or receiving any sort of information over the internet—from a simple phone call to your bank transactions—today’s increase in internet usage and data sharing means APIs must be aligned with security.
When APIs exchange data over an insecure network, there is a greater chance of that data getting manipulated by a malicious third party. So to make the internet safer and to avoid unnecessary data theft, it is always better to encrypt every piece of information before pushing it to a network.
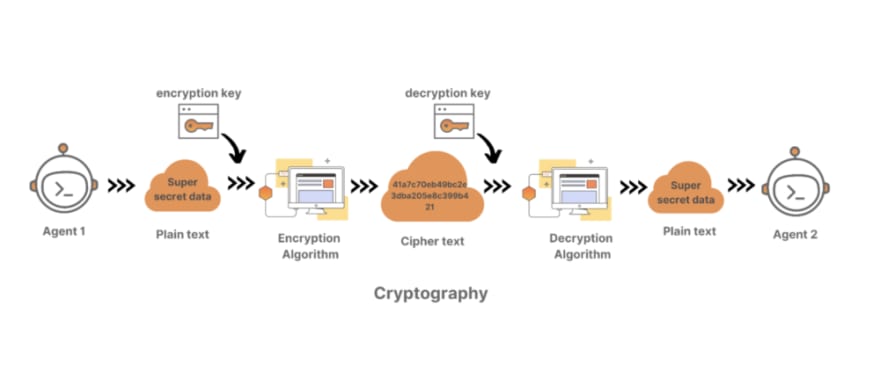
This is where the concept of cryptography comes in. Cryptography is one of the ways we can keep information secured over an insecure public network. Let’s dive deeper into cryptography, how it works, and how to use crypto encryption with the Postman API Platform.
What is cryptography?
In simple terms, “cryptography” refers to the art of securing sensitive information using mathematical algorithms. These algorithms stop third parties, commonly known as adversaries or hackers, to peep into your data. To avoid unauthorized access to information communicated between authorized parties, cryptography uses encryption and decryption methods. According to American cryptographer and computer security expert Bruce Schneier, cryptography is “the art and science of keeping messages secure.”The cryptography method transforms plain text into encrypted text (aka ciphertext) using the encryption key, and the target receiver can decrypt it using a unique decryption key. This decryption key depends on what type of cryptography algorithm is used by the sender. It’s important to note that encryption algorithms keep the data secure only if the attackers are unaware of your method of encryption or anything else about the key.
3 types of cryptography
- Hash function: Hash functions are the most commonly used cryptography algorithms, in which there is no involvement of any key. In hash functions, plain text is transformed into a fixed-length of value, which is never recovered to its original form.
- Symmetric key encryption: In symmetric cryptography, both sender and receiver share a single key, which they use to encrypt and decrypt. This system is faster and simpler as compared to other encryption types. The only limitation is sharing the key with the recipient over an insecure network. Symmetric encryption is brilliant when data is stored and accessed centrally.
- Asymmetric key encryption: Asymmetric cryptography uses different keys for encryption and decryption of information. It uses a public key for encryption, but also a private key for decryption of data.
How to encrypt data in Postman?
Postman allows you to perform different tasks on API requests and test scripts where you might apply encryption—for comparing within the test or authenticating headers—and there are many other possibilities when encryption can be used. To help users work with different options, Postman supports a list ofexternal libraries.
Crypto.js is one of the most requested libraries for encryption and decryption. You can find a list of examples in this crypto.jscollection, which you can start working with by forking to your workspace:
Postman Collections for cryptography algorithms
- AES (Advanced Encryption Standard): AES is symmetric cryptography that uses a block cipher. It is used in both software and hardware across the world for encrypting sensitive data. AES uses three block ciphers, which include 128-bits, 192-bites, and 256-bits which are used to encrypt and decrypt data. Code sample for AES encryption:
const Message **=** pm.variables.replaceIn('{{$randomCatchPhrase}}')
const SecretPassphrase **=** pm.variables.replaceIn('{{$randomPassword}}')
var superSecretEncrypted **=** CryptoJS.AES.encrypt(Message, SecretPassphrase);
var noMoreSuperSecret **=** CryptoJS.AES.decrypt(superSecretEncrypted,
console. **log** ("superSecretEncrypted :: " **+** superSecretEncrypted **+**"\n" **+**
"superSecretDecrypted :: " **+** noMoreSuperSecret);SecretPassphrase);
- DES (Data Encryption Standard): DES is also symmetric cryptography, which uses the same key to encrypt and decrypt data. It is considered less secure for powerful attacks, due to which the popularity among others has slightly declined. DES encrypts data in 64-bits, which means that 64-bits plain text input is sent and 64-bits ciphertext output is produced. Similarly, Triple DES can also be used, where the DES encryption is applied three times to each block to increase the key size. Code sample for DES encryption:
const Message **=** pm.variables.replaceIn('{{$randomCatchPhrase}}')
const SecretPassphrase **=** pm.variables.replaceIn('{{$randomPassword}}')
var superSecretEncrypted **=** CryptoJS.DES.encrypt(Message, SecretPassphrase);
var noMoreSuperSecret **=** CryptoJS.DES.decrypt(superSecretEncrypted, SecretPassphrase);
console. **log** ("superSecretEncrypted :: " **+** superSecretEncrypted **+**"\n" **+**
"superSecretDecrypted :: " **+** noMoreSuperSecret);
- MD5 (Message-Digest Algorithm): MD5 is a protocol used for authorizing messages, content, and digital signature verification. It generates a hash that can be used to verification of data or files by sender and receiver. Previously, MD5 was majorly used for encryption of data, but now it’s primarily used for authentication. The algorithm converts data into a string of 32 characters, irrespective of file size. Code sample for MD5 hash:
const Message **=** pm.variables.replaceIn('{{$randomCatchPhrase}}')
//setting up collection variable as MD5hash
var MD5hash **=** CryptoJS.MD5(Message). **toString** ();
console. **log** ("MD5hash :: " **+** MD5hash)
- SHA-256 (Secure Hashing Algorithm): SHA-256 is a patented algorithm that is a part of the SHA-2 family. This is a hash function that produces 256-bits long ciphertext. It was a successor for SHA-1 which was losing strength against brute force attacks. Code sample for SHA-256:
var sha256Hash **=** CryptoJS.SHA256(Message). **toString** ();
console. **log** ("sha256Hash :: " **+** sha256Hash)
const Message **=** pm.variables.replaceIn('{{$randomCatchPhrase}}')
Conclusion
After walking through the cryptography algorithms above, we can see that cryptography is an essential tool for encryption that makes data secure and safe. Ultimately, data stored or transmitted with encryption is much safer than data left unencrypted. There are a lot more cryptography algorithms that can be used for different purposes depending on the use cases, so be sure to explore the complete Encrypt Parameters Using CryptoJS collection to learn more.
The post What Is Cryptography? And How to Encrypt Data in Postman appeared first on Postman Blog.