Identity management is the easiest when you can manage identities in one place and use them across accounts and applications. AWS IAM Identity Center streamlines identity management by enabling you to connect to your identity provider (IdP), such as Active Directory, and use the IdP's identity information for access and collaboration within applications. You can do this, for example, by using an AD Connector and connecting it to your on-premises or Azure AD. An AD Connector is a directory gateway that allows you to route directory requests to your on-premises Microsoft Active Directory without storing information in the cloud cache.
If you have a large Active Directory with several thousand groups and users, you may not want to explicitly select the identities you want to synchronise with AWS Identity Center.
In this blog post, we will show you a solution that allows you to specify different prefixes for Active Directory groups that will be automatically synced to your AWS Identity Center.
The solution workflow includes the following steps:
- Synchronization of Active Directory Groups
- Automated Documentation & Notification
Prerequisite:
- Identity Center must be enabled in your Organization
- Connection to local or Azure Active Directory
- Active Directory User who has read access
Solution overview
The following architecture shows the solution of the automated sync of Active Directory Groups to AWS Identity Center .
🔗 Here you can find the Solution on Github
In our CDK based project several resources will be provisioned due deployment.
The Stack contains:
- Amazon EventBridge rule that runs on a schedule
- CDK Sops Secrets Construct
- Secret which holds the Active Directory Credentials
- Lambda Function to create the Synchronisation Filter in AWS IAM Identity Center
- all necessary IAM Roles and Permissions for the Lambda Function
Synchronization of Active Directory Groups
With Active Directory group synchronisation, you use IAM Identity Center to assign users and groups from Active Directory access to AWS accounts and to AWS-managed or customer-managed applications. All Active Directory Groups with specified prefixes will be automatically synchronised to your AWS IAM Identity Center.
How the automation with the lambda function works
The Sync LambdaFunction is triggered by Eventbridge Scheduled event to ensure that the Groups you want sync from your active directory are always uptodate in your AWS Identity Center.
The workflow of our Sync LambdaFunction is the following:
- Retrieve Active Directory credentials from AWS Secrets Manager
- Log on to Active Directory using LDAP(s) using the credentials just retrieved
- Search and retrieve Active Directory group names based on specified prefixes
- Retrieve current Filters of Groups which are sync scope from AWS Identity Center
-
Add missing Active Directory groups as synchronisation filters in AWS Identity Center
- ℹ Synchronisation to AWS Identity Center will start after a short amount of time.
Generating of automated documentation
Sending notification to MS Teams
Deployment
The deployment of the solution is done via a cdk stack which is part of the solution's repository. All the required Parameters will be configured in a typescript file - an example file is also included in the repository.
What you have to configure:
| Property | Description |
|---|---|
| Produkt | will be used to generate StackName |
| Stage | will be used to generate StackName |
| Prefix | will be used to generate StackName |
| s3_DOKUBUCKET | Name of the S3 Bucket for the generated documentation |
| WebhookUrlTeams | URL of your MS Teams Webhook |
| DocuWebsite | Link to the Website where the generated HTML snippet has been published used for a button in the Team Nofitication |
| LambdaSchedule | Duration how often your Lambda should be trigger from Eventbridge. Rates may be defined with any unit of time, but when converted into minutes, the duration must be a positive whole number of minutes. |
| rootCaCertificateString* | the Root CA Certificate in PEM format which issues the server certificates Active Directory |
| vpcId | Id of your VPC where the lambda will be deployed to |
| subnetIds | Ids of subnets where the lambda will be deployed to |
| ad_DomainName | Name of your Active Directory |
| BasePath | Path in your Active Directory where the Lambda can find the Users you want to Sync |
| GroupPrefixes | Array of prefixes of groups you want to synchronise into your AWS Identity Center |
| SecretFile | Path to your Sops secrets file, which should contain the Active Directory user credentials. |
| Url | LDAP Url to your Active Directory. The LDAP URL format is ldap:// hostname |
| Port | Port of your LDAP - LDAP default is 389, LDAPs = 636 |
| IdentityStoreId | Identity Store Id of your AWS Identity Center |
| Endpoint | AWS hidden API Endpoint- should be identity-sync..amazonaws.com |
Automated Documentation & Notification
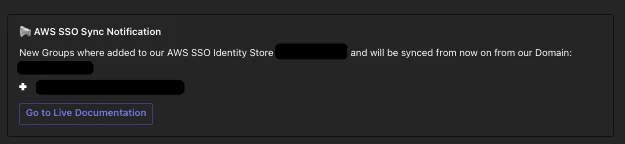
After each execution of the Synchronisation Lambda, we aim to notify our team about the actions taken during the previous run. Therefore, we have implemented a Teams notification that includes a status update and a link to an automatically generated dashboard.
ℹ️ Notifications are only sent when groups are added or deleted, or when an automation error occurs, to avoid a flood of notifications.
The following screenshot illustrates an example of a Teams notification.
Documentation
Our Active Directory Synchronization Status Dashboard is a simple HTML file which will be generated trough a Lambda Function, saved in S3 and will be distributed trough a CloudFront. You can integrate this Dashboards in your Confluence or any other internal Wiki. This Dashboard is secured via CloudFormation Function - additionally you can also add a Firewall to restrict the access to an specific CIDR or Geographic region and prevent access from third parties. The screenshot below provides an example of a dashboard.
Conclusion
In this blog post, we showed you how to improve your security posture by automatically and regularly synchronising Active Directory groups that match a specific pattern with AWS Identity Center. This simplifies access management and increases security by automatically revoking access in AWS Identity Center when group objects are deleted or created in Active Directory. Furthermore, the automatically generated documentation facilitates an overview of the synchronised group objects.