If you've read my previous writeup where I covered Logging and Hardcoding Issues (1 & 2) on the DIVA APK, then get ready for the next one. I hope you have your tools open, because today we are going to find all the Insecure Data Storage vulnerabilities in the DIVA APK!😁
So the DIVA APK has four sections to test for Insecure Data Storage. Insecure Data Storage vulnerabilities occur when programmers assume that users, malware, or attackers will not have access to a mobile device’s filesystems and sensitive information that is stored on the device or APK. The problem arises when filesystems are easily accessible. Attackers, or us in this case, can root or jailbreak mobile devices or APK's and view application data - ultimately, sensitive application data.
Without any further lollygagging, let's jump into it!

Insecure Data Storage - Part 1
When we open the Insecure Data Storage - Part 1 section we are met with the following objective: find out where/how the credentials are being stored and the vulnerable code. So, we are expected to find where the credentials are being stored, how it is stored, and the vulnerable code.
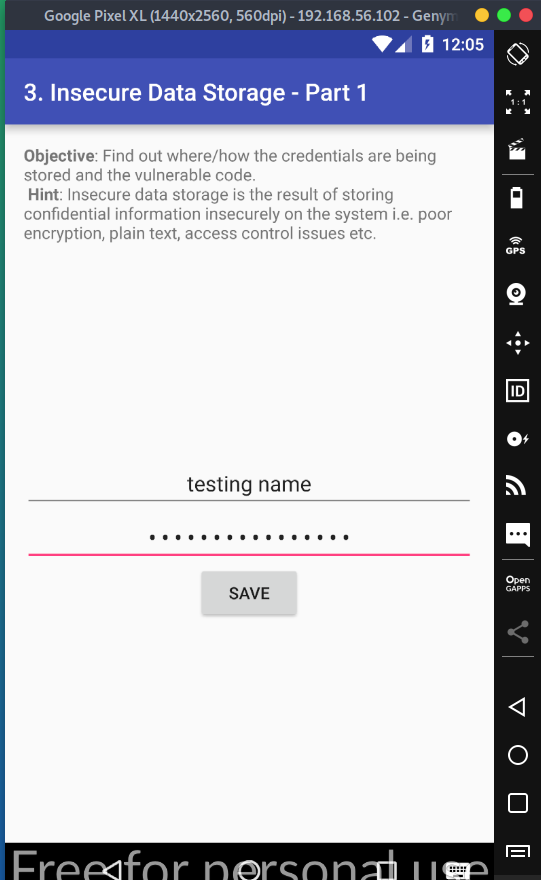
Let's first start with inserting information into the form. We get a popup saying that our credentials has been saved,and that's about it. Not much to it, so let's see if we can find where it saved our credentials.
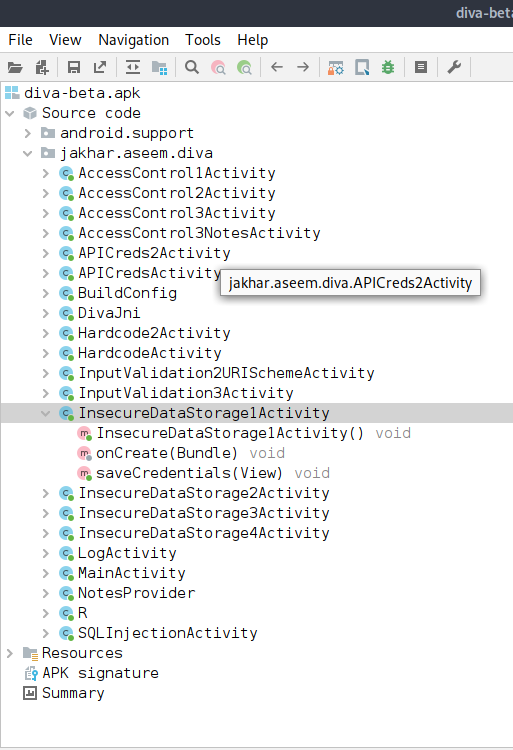
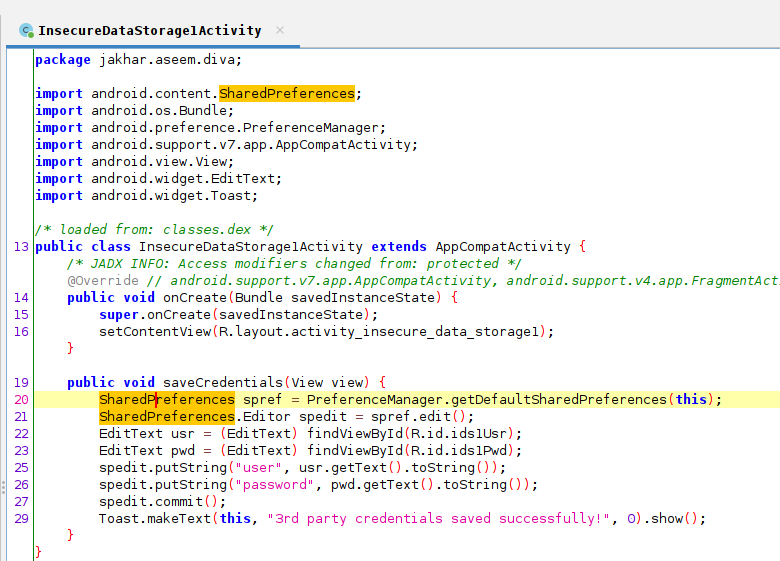
Let's go ahead and pen up JADX-GUI and navigate over to the InsecureDataStorage1Activity. From here we can see that our data is being stored in a SharedPreferences object. A SharedPreferences object points to a file that contains key-value pairs and provides simple methods to read and write them. Each SharedPreferences file is managed by the framework and can be private or shared. A simple example of using a SharedPreference object is saving the user's preferred background color for the application.
Usually, the SharedPreference file will be saved under ../data/data/name.company.com/shared_prefs/.. and to access or view this SharedPreference file I will show you two methods: how to access it in Android Studio, and how to access it via the terminal.
Method One: Android Studio
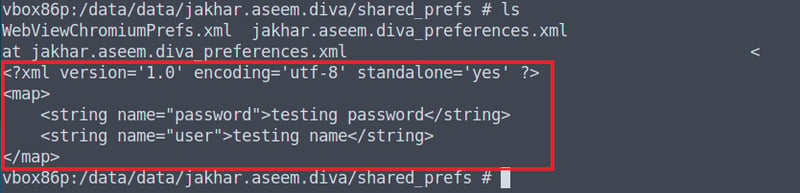
Open up Android Studio and select the Device Manager bar on the right-side of your window. Then head into the File Explorer and navigate to the following file (data > data > jakhar.aseem.diva > shared_prefs > jakhar.aseem.diva_preferences.xml)

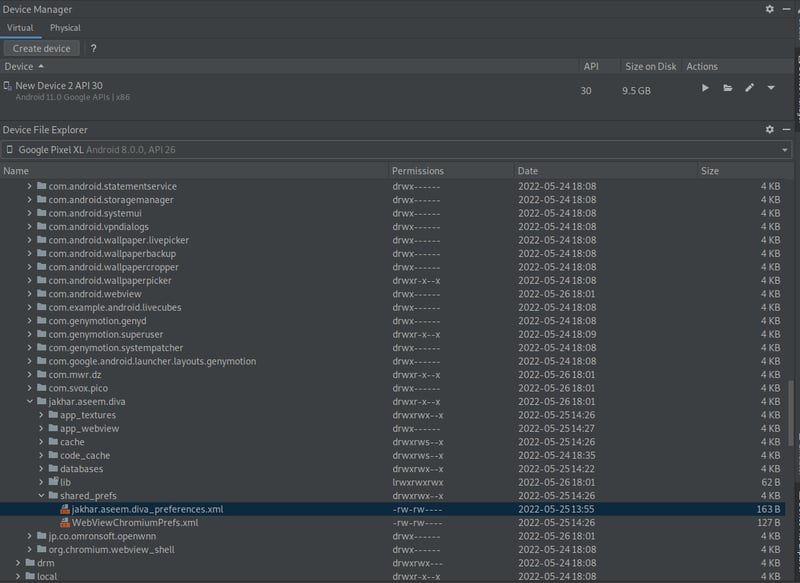
Double click on jakhar.aseem.diva_preferences.xml, and voila, we have access to the data via Android Studio!
Method Two: Terminal
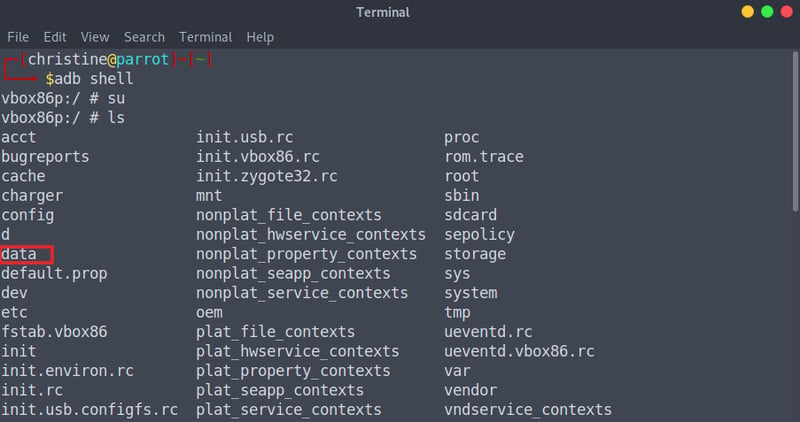
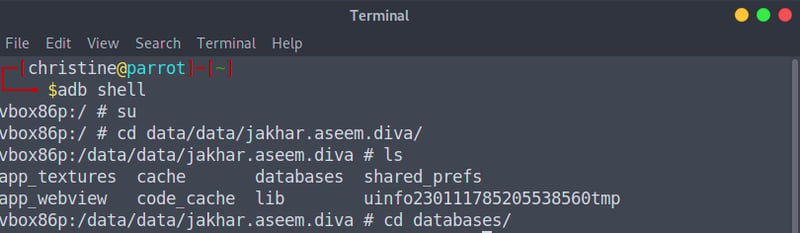
Open up your terminal via CTRL + ALT + T and start a adb shell via the adb shell command. ADB Shell will allow us to access the device's files and manipulate the device via the terminal. We need to get super-user access, which is ultimate Darth Vader access, by entering to su command.
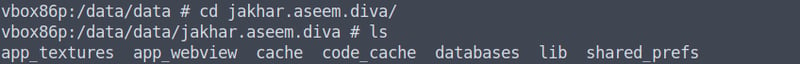
Let's go ahead and list our files on the device via the ls command, and from here on we can navigate to the directory as we did in Android Studio:
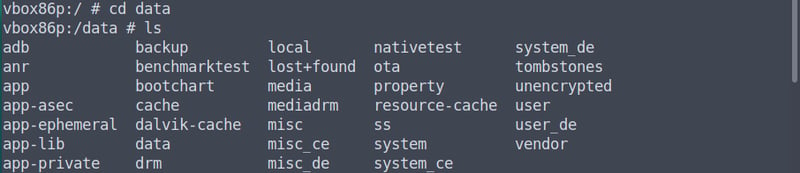
cd data
cd data
cd jakhar.aseem.diva
cd shared_prefs
Finally, we can read the data by entering the cat jakhar.aseem.diva_preferences.xml command. And we're done!
So, in summary, we were able to find the following:
- Where: shared_prefs > jakhar.aseem.diva_preferences.xml
- How: SharedPreferences() object
Insecure Data Storage - Part 2
When we open the Insecure Data Storage - Part 2 section we are met with the following objective: find out where/how the credentials are being stored and the vulnerable code. So, we are expected to find where the credentials are being stored, how it is stored, and the vulnerable code.
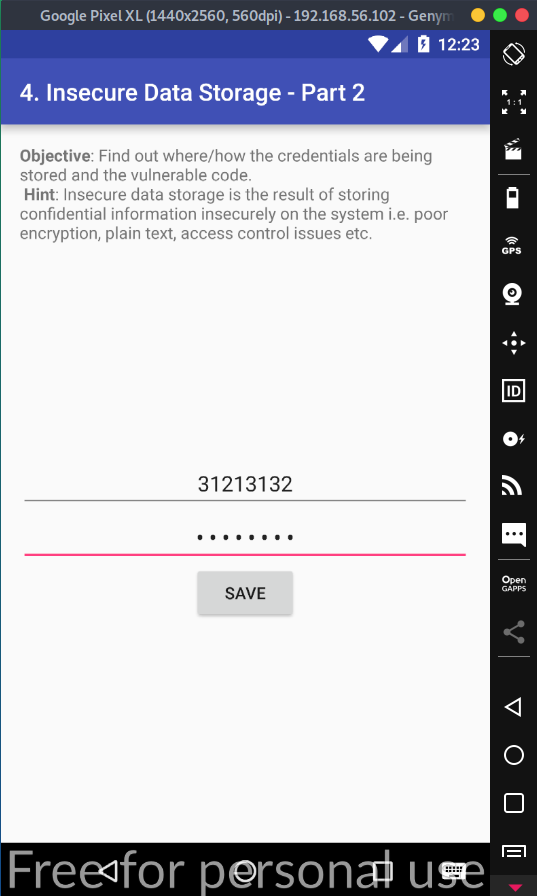
Let's first start with inserting information into the form. We get a popup saying that our credentials has been saved,and that's about it. Again, not much to it, so let's see if we can find where it saved our credentials.
Open up JADX-GUI and navigate over to the InsecureDataStorage2Activity. From here we can see that our data is being stored in a SQLiteDatabase object - so we will be looking for a database file!
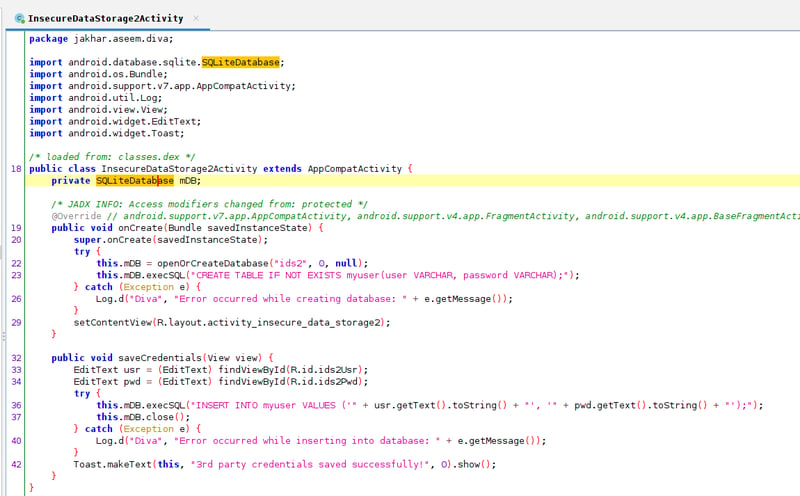
Usually, the SQLiteDatabase database files will be saved under ../data/data/name.company.com/databases/.. and to access or view this database file I will show you two methods: how to access it in Android Studio, and how to access it via the terminal.
Method One: Android Studio
Open up Android Studio and select the Device Manager bar on the right-side of your window. Then head into the File Explorer and navigate to the following file (data > data > jakhar.aseem.diva > databases). From here we can see numerous database files, but just looking at the name we can deduce that "ids2" (id) will be more valuable to look at than "diva notes". So, let's have a look at ids2.
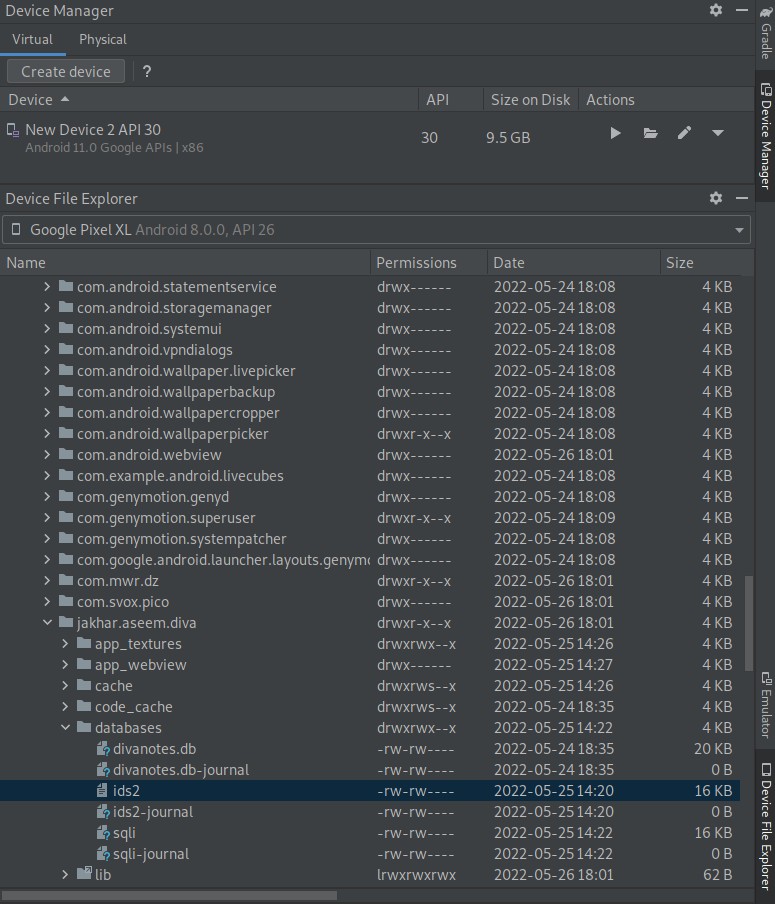
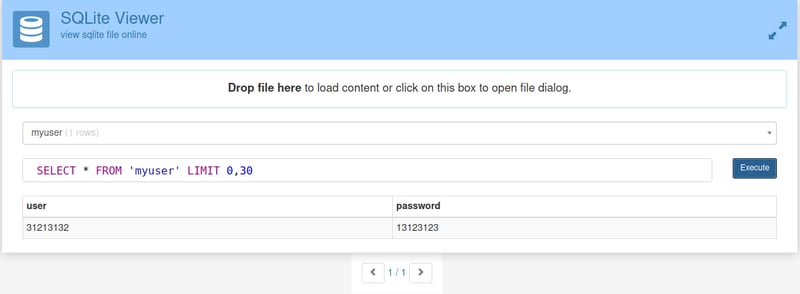
Right click and save ids2 to a place on your desktop that you feel comfortable with. Once saved, open up your browser and head over to SQLite Viewer so that we can view the contents of our database. Pop in your ids2 file. We can see that there are two tables.
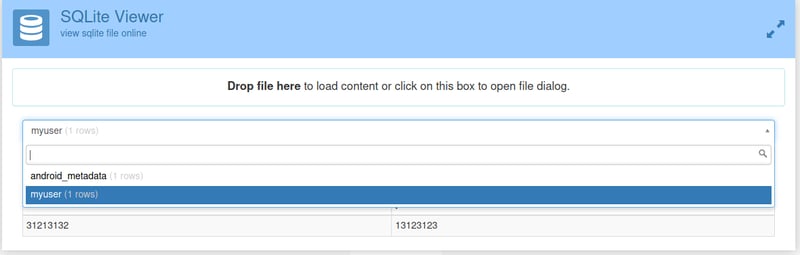
Let's open the myuser table. We can now see our credentials!
Method Two: Terminal
Open up your terminal via CTRL + ALT + T and start a adb shell via the adb shell command. From there on we can go:
su
cd data
cd data
cd jakhar.aseem.diva
cd databases
When we list the files in our databases directory, we can see that the ids2 file is there. To read it, we need to first enter the qlite3 command (enter it by typing sql and hit TAB and enter).
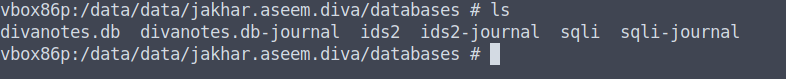
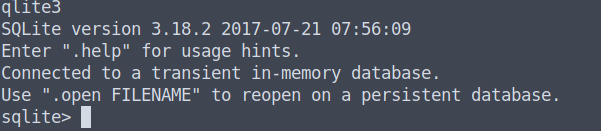
From there on we need to open up the ids2 database file via the .open ids2 command. If we list all the tables via the .tables command we can see that myuser is one of them. We can then "cd" into the myuser tables via the .tables myuser command.

To read the contents of the myuser table, we can simply say .dump myuser, and congrats, you've successfully cracked that bad boy open! 😎
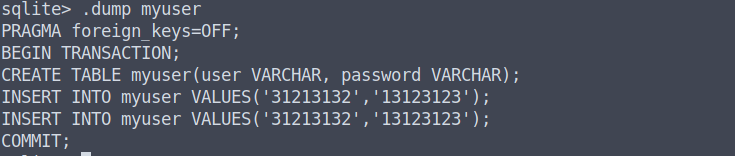
So, in summary, we were able to find the following:
- Where: databases > ids2
- How: SQLiteDatabase mDB
Insecure Data Storage - Part 3
When we open the Insecure Data Storage - Part 3 section we are met with the following objective: find out where/how the credentials are being stored and the vulnerable code. So, we are expected to find where the credentials are being stored, how it is stored, and the vulnerable code.
Let's first start with inserting information into the form. We get a popup saying that our credentials has been saved,and that's about it. Again, not much to it, so let's see if we can find where it saved our credentials.
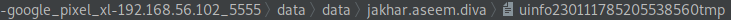
Open up JADX-GUI and navigate over to the InsecureDataStorage3Activity. From here we can see that our data is being stored in a FileWriter object that is being stored as uinfotmp - so we are looking for a file with a (tmp) ending.
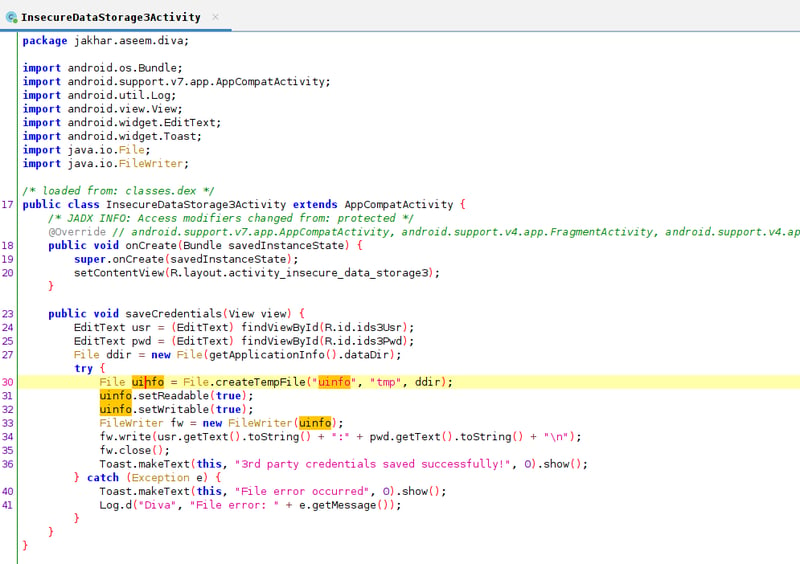
The FileWriter tmp file will be saved under ../data/data/name.company.com/.. and to access or view this uinfo file I will show you two methods: how to access it in Android Studio, and how to access it via the terminal.
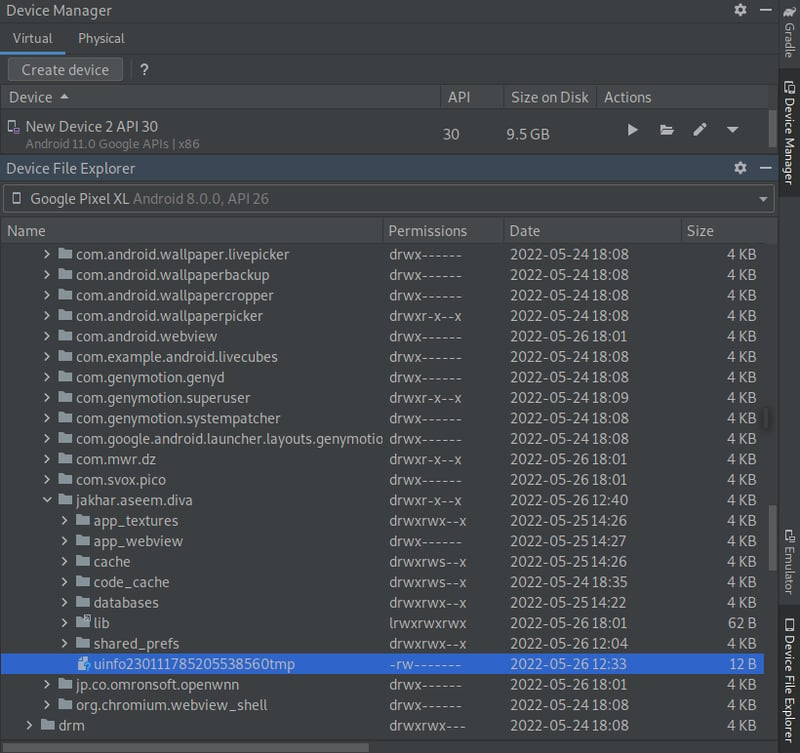
Method One: Android Studio
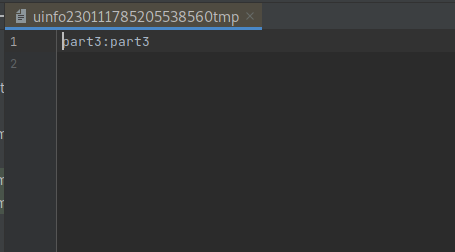
Open up Android Studio and select the Device Manager bar on the right-side of your window. Then head into the File Explorer and navigate to the following file (data > data > jakhar.aseem.diva. From here we can see that our file is there, labeled as something similar to uinfoxxxxxxxxxxxxtmp.
Double click your uinfotmp file. You can now read the data!
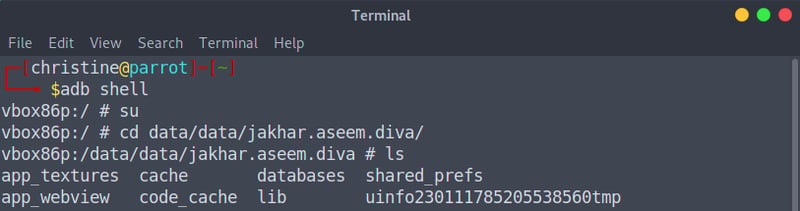
Method Two: Terminal
Open up your terminal via CTRL + ALT + T and start a adb shell via the adb shell command. From there on we can go:
su
cd data
cd data
cd jakhar.aseem.diva
When we list the files we can see our uinfotmp file. To read the contents of the uinfotmp file, we can simply say cat uinfoxxxxxxxxxxxxtmp (replace uinfoxxxxxxxxxxxxtmp with your filename), and you are set!
So, in summary, we were able to find the following:
- Where: jakhar.aseem.diva > uinfotmp
- How: FileWriter(File)
Insecure Data Storage - Part 4
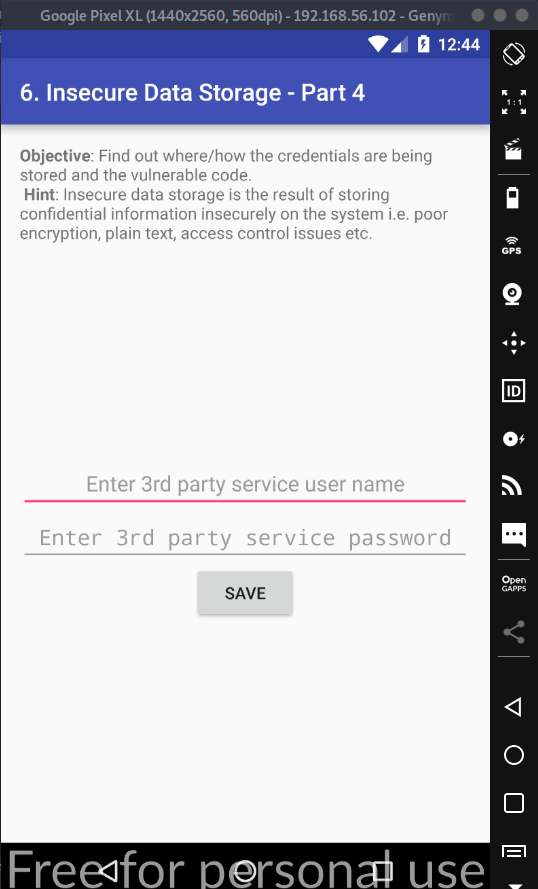
When we open the Insecure Data Storage - Part 4 section we are met with the following objective: find out where/how the credentials are being stored and the vulnerable code. So, we are expected to find where the credentials are being stored, how it is stored, and the vulnerable code.
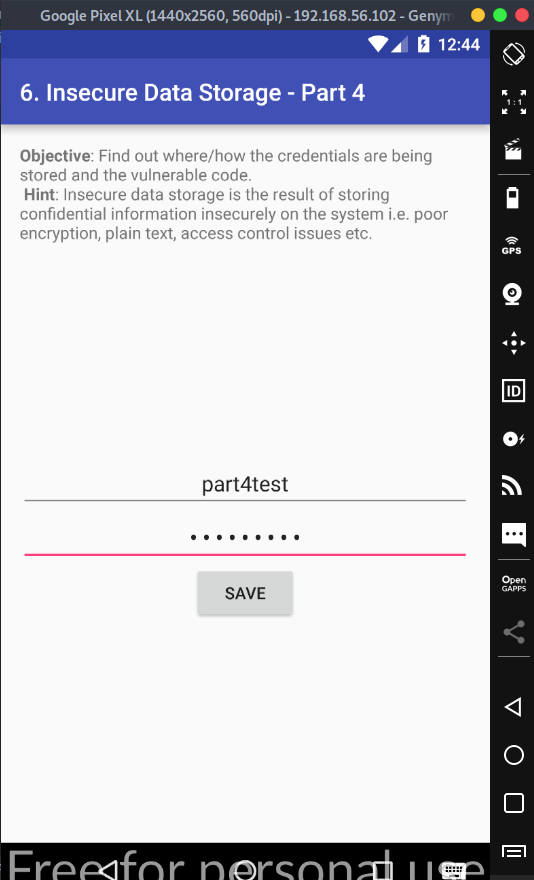
Let's first start with inserting information into the form. We get a popup saying that our credentials has been saved,and that's about it. Again, not much to it, so let's see if we can find where it saved our credentials.
Open up JADX-GUI and navigate over to the InsecureDataStorage4Activity.
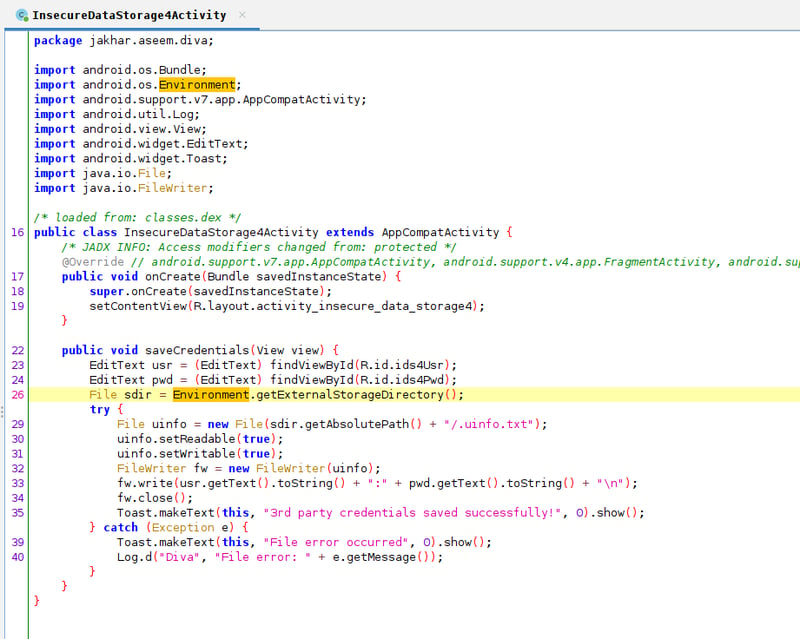
From here we can see that our data is being stored in something called Environment.getExternalStorageDirectory(). No worries, this only means that it is saving our file as .uinfo.txt to our devices' SDCard.
The SDCard will be saved under our root directory. I will show you how to access this file I via two methods: how to access it in Android Studio, and how to access it via the terminal.
Method One: Android Studio
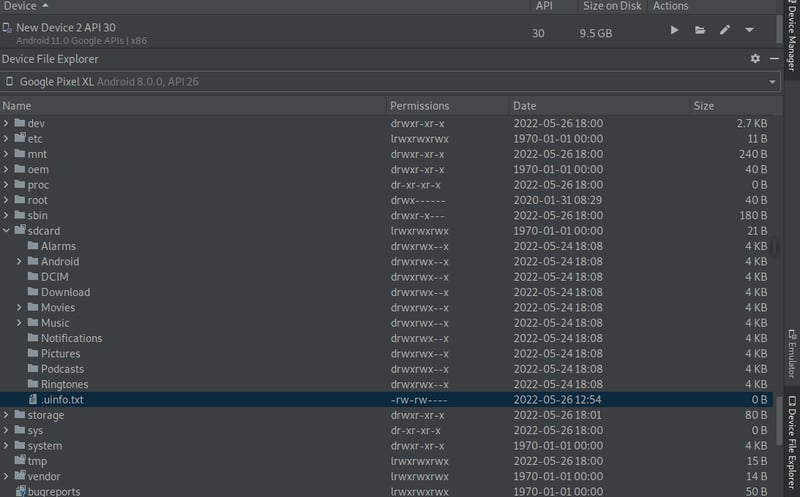
Open up Android Studio and select the Device Manager bar on the right-side of your window. Then head into the File Explorer and navigate to the following directory: sdcard. From here we can see that our file is there, labeled as .uinfo.txt.
Double click your .uinfo.txt file. You can now read the data!
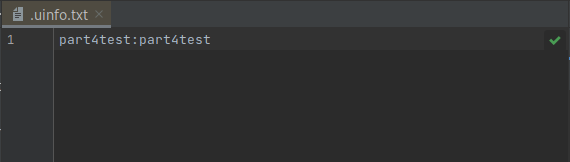
Method Two: Terminal
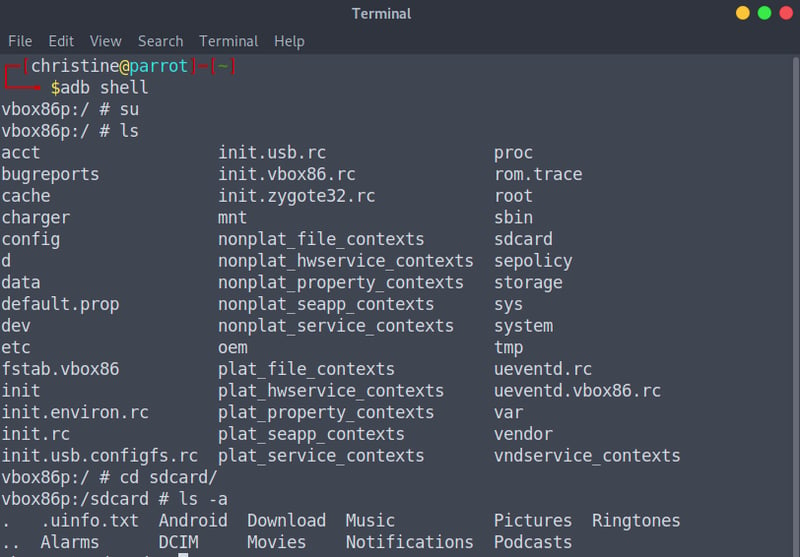
Open up your terminal via CTRL + ALT + T and start a adb shell via the adb shell command. From there on we can go:
su
cd sdcard
When we list the files we can see our .uinfo.txt file. To read the contents of the .uinfo.txt file, we can simply say cat .uinfo.txt. Now we know all it's dirty little secrets!
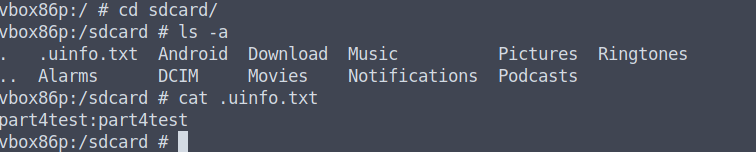
So, in summary, we were able to find the following:
- Where: sdcard > .uinfo.txt
- How: FileWriter(File)
Congrats, we have finished the third section of the DIVA APK! I hope this was easy enough to follow/understand. I'll see you next time with Section 4: Input Validation Issues.😊
If you have recommendations on any cool tools, techniques, or tutorials that I too can follow feel free to leave them below and I'll check it out!
(Pull this on my GitHub for future reference)