I'm not going to lie to you, sometimes I feel like the Try Hack Me labs are poorly written. Not in the way that I can't understand anything, but to the point where I feel like the author of the lab assumed that every student doing the lab will be on their level. That's where write-ups and walk-through videos make things easier. It helps beginners like me understand the fundamentals, and navigate my way through my hacker journey without getting frustrated, or giving up.
Today I thought to write my own write-up on a lab that I found pretty challenging: Windows PrivEsc on the Jr Penetration Tester learning path. Let's get started! 😊
I will be skipping over the following tasks since it is read-only to complete:
- Task 1: Introduction
- Task 3: Tools of the trade
- Task 7: Token Impersonation
- Task 8: Quick Wins
Task 3: Information Gathering
To read the instructions/general information for this section please go to the task dedicated to it. I will not be copying and pasting all the information since it will make the write-up bloated and honestly, if you're following along, it's unnecessary to repeat what you've already read! 😁
Launch the target machine.
We will need to use Attackbox for this, or our own Windows Machine. For this writeup, I will be working on Attackbox.

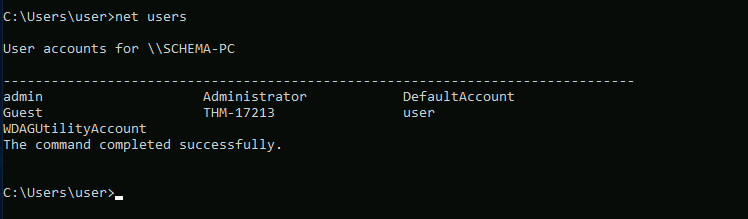
List users on the target system. One of them resembles a flag.
Open up your cmd on your Windows machine and enter in the net users command. We can see the flag clear as day!
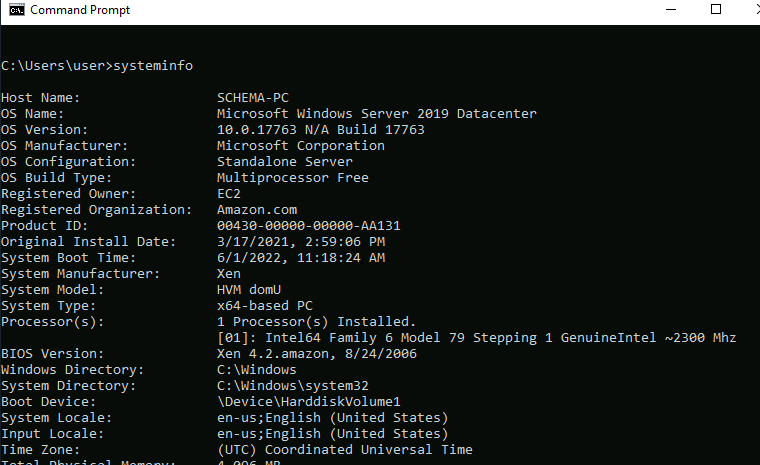
What is the OS version of the target machine?
In your cmd enter the systeminfo. You will find the OS version next to OS Version. 👀
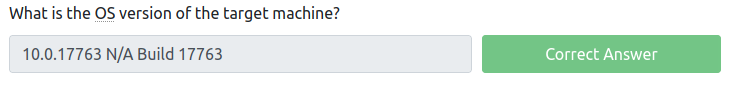
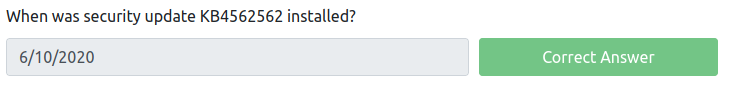
When was security update KB4562562 installed?
You can use thewmic qfe get Caption,Description,HotFixID,InstalledOn command in cmd, but an easier method to find the date for this is to open up PowerShell on your Windows Machine and enter the Get-Hotfix command.
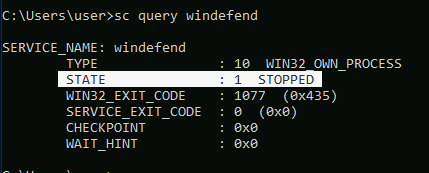
What is the state of Windows Defender?
Go back into your normal cmd and enter the sc query windefend command. (This answer was in the sections' tutorial)
Task 4: Information Gathering
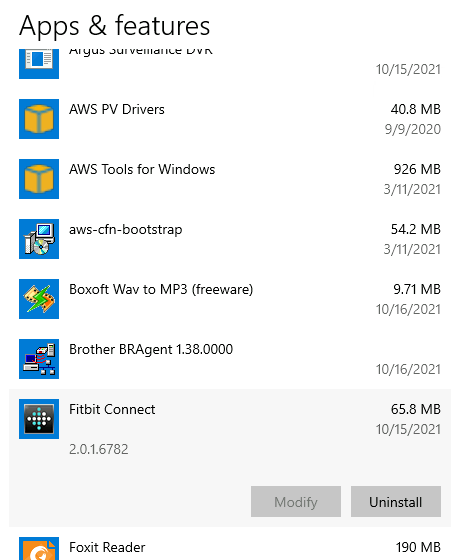
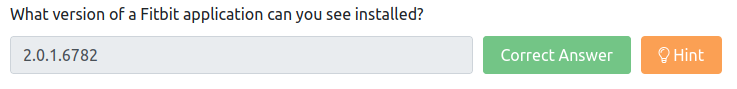
What version of a Fitbit application can you see installed?
Go into your cmd and enter the following command wmic product where "Vendor like %Fitbit%'" get name,version.

You can also just go into your add/remove programs on your Windows Machine to reveal the same information.
What kind of vulnerability seems to affect the Fitbit application?
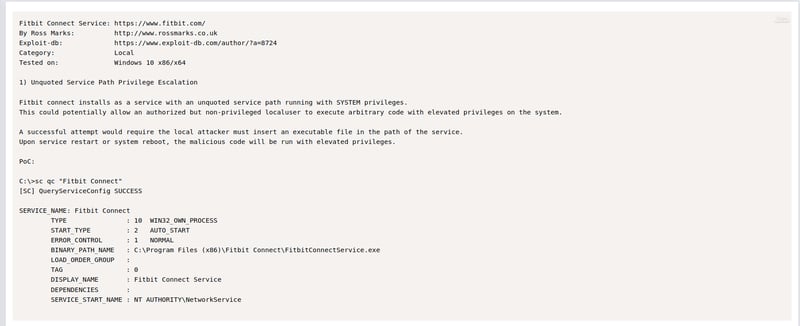
This requires us to google a little bit. With a quick search on Exploit-DB we can see that it is affected by a Unquoted Service Path vulnerability.

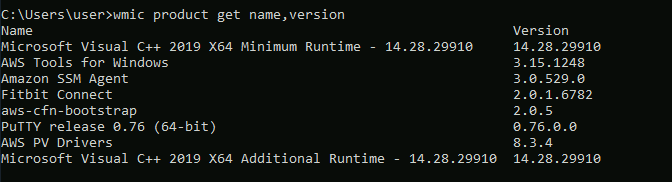
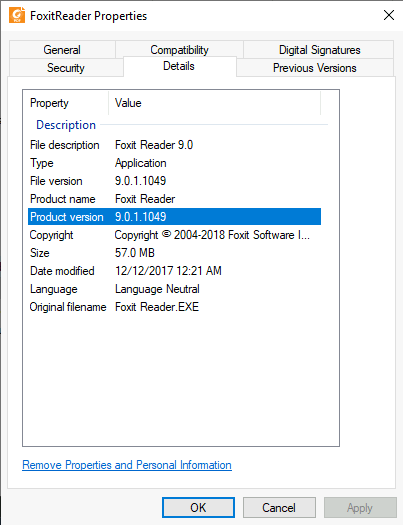
What version of FoxitReader is installed on the target system?
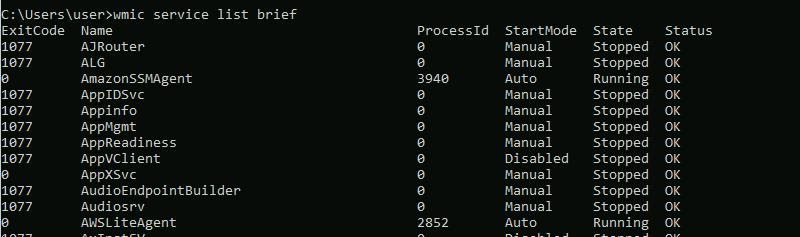
If we try to use the wmic get product name,version command we can see that it does not return the FoxitReader service.
We will need to do something different. Go back to your cmd and enter the wmic service list brief command. You will see it listed below without it's version.

We know it's on the system, so we can go find it in our Program Files (x86) and read its properties to see which product version it's running.
Task 5: DLL Hijacking
I'm going to be honest with you, this was way too much effort for the result received. If you want a detailed walk-through on this, let me know, but for now, I'm just going to go ahead and give you the answers. 😊
You can do this easily by just following the steps above and by making use of the hints provided. (The video that helped me with this task can be found here).
Login with Jack's account (the new password you have set). What is the content of the flagdll.txt file?
Task 6: Unquoted Service Path
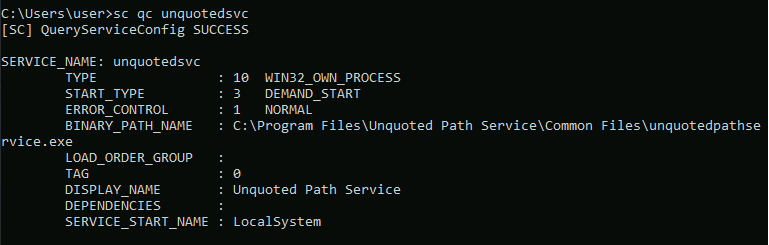
What is the full unquoted path of unquotedsvc
Open up your cmd and enter the sc qc unquotedsvc command to find the full unquoted path of unquotedsvs.
Go through subfolders in the unquotedsvc binary path. Which folder does the user have read and write privileges on? (Please write the whole path)
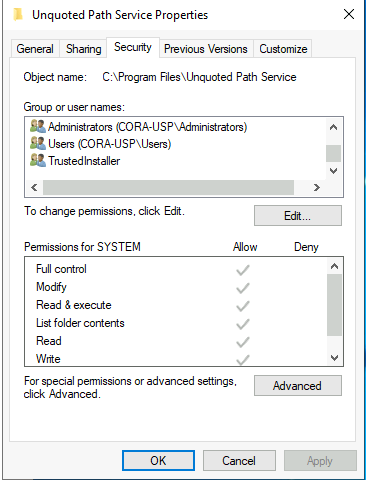
Go to the C:\Program Files\Unquoted Path Service\ directory and read the properties of the folder. Stop before you go into Common Files.
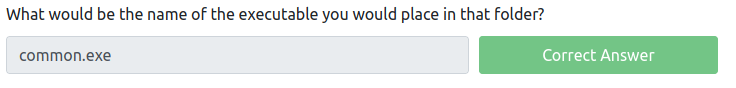
What would be the name of the executable you would place in that folder?
We can assume since it has a folder Common Files, the executable will be common.exe.
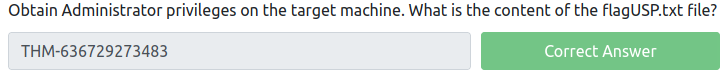
Obtain Administrator privileges on the target machine. What is the content of the flagUSP.txt file?
Since this is another section where we need to set up a remote desktop client, I'm going to skip over that and just give the answer. If you want a detailed walk-through on this, let me know and I will add it in.
The video listed above really helped me with this.
Conclusion
I hope this helped somewhat as this lab really tested me. I found it hard, and setting up the remote desktop was so much effort. The instructions (in my opinion) was also not as clear as I wished it would be, especially for task 5 and 6. Anyway, I got through it and now, so have you! 😀
Check out my GitHub for more.