86% of developers don't see security as a top priority when writing code. If your team is part of this stat - we can't blame you. Pressing deadlines, time constraints, and lack of training are severe problems within dev teams. And, of course, they make security seem like a painful and strenuous chore that can be avoided amid all the chaos.
You already know that securing web applications is essential, but it can be daunting. Still, there are ways to make security work for your team (really!). So, in this article, we will cover the different types of web application security testing and ten critical steps in securing your web applications.
Overview of Web Application Security Testing
Web application security testing, or WAST, is a process used to ensure your web applications are secure. It is a continuous effort and requires multiple security tests, which we will explain later in this article.
While it focuses mainly on the application layer (you may have heard the concept of Web AppSec), it aims to find vulnerabilities across the application and all its functionalities. Some features reviewed during WAST include server configuration, input and output handling, and authorization and authentication credentials.
Why should you consider Web Application Security Testing?
Cyber threats are a never-ending storm, constantly changing and evolving, leaving businesses vulnerable to attack. It's not just about finding vulnerabilities. It's about understanding the potential impact of those vulnerabilities and taking the appropriate measures to mitigate them. For example, an exposure that allows an attacker to steal sensitive data requires other migitation actions than a vulnerability that allows an attacker to execute arbitrary code.
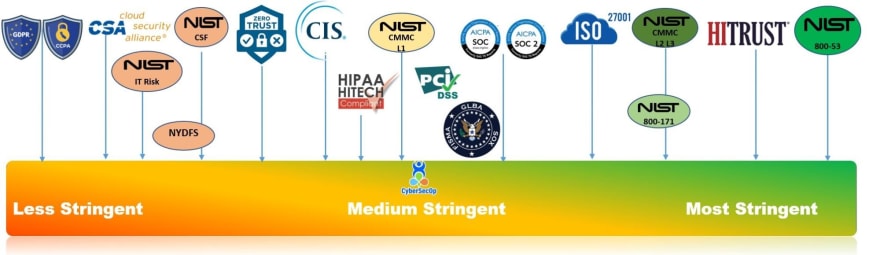
And WAST isn't just about protecting your business. It's about compliance too. Regulations like PCI-DSS, HIPAA, and SOC 2 require organizations to protect sensitive data and demonstrate that they have implemented adequate security controls. WAST can be used as a guide to ensure you meet all the regulatory requirements.
4 Types of Web Application Testing
Every kind of WAST addresses specific security concerns and can be executed at various stages of the software development life cycle (SDLC). Some of the most commonly used types of WAST include:
1. SAST
SAST, or Static Application Security Testing, comes early in the development process before the application's deployment. It can be integrated into the development process and run automatically as part of the build process, making it easy to ensure security is built-in from the start.
SAST tools analyze the application's code and identify potential vulnerabilities without the need for the application to be running. They look for vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
2. DAST
DAST (Dynamic Application Security Testing) tools simulate real-world attacks by sending requests to the application, analyzing the responses, and identifying potential vulnerabilities. This type of testing is often performed during the testing stage of the SDLC to identify any security flaws that may have gone unnoticed during development.
One of the advantages of DAST is that it can identify vulnerabilities that may not be present in the source code but are present in how the application is configured. DAST can also identify vulnerabilities that only appear when the application runs, such as vulnerabilities caused by misconfigured servers or other runtime issues.
3. Penetration Testing
Penetration testing is like a thrilling game of cat and mouse between ethical hackers and your web application's defenses. Expert ethical hackers, known for their mastery in uncovering vulnerabilities in a target system, typically conduct penetration testing on the application to ensure its security.
By simulating a real-world attack, penetration testing can help identify vulnerabilities that other methods may miss. It can also help organizations understand how an attacker might exploit a vulnerability and take steps to mitigate the risk.
4. RASP
Runtime Application Self-Protection (RASP) constantly monitors the runtime environment of a web application to identify and prevent security threats.
RASP can identify vulnerabilities that may not be present in the source code but are present in how the application is configured and only appear when the application runs. It's the last line of defense that can help ensure the security of your web application.
10 Essential Steps for Web Application Security Testing
To properly perform web application security testing, these are ten essential steps that you should follow:
1. Understand your security testing scope
Understanding your security testing scope includes identifying the web applications for testing, the types of testing required, and the necessary resources.
Having a clear and defined scope for your testing is essential to ensure that all critical areas are covered and that you are not wasting resources on unnecessary testing. A well-defined scope will also help you set realistic metrics for the testing process and prioritize vulnerabilities that the security testing scope must address.
2. Implement each tool on all resources
As we have seen earlier, many tools are available. It's essential to choose the right tools for your specific needs and to ensure that they are up-to-date and compatible with your environment.
But the process goes beyond selecting the right tools: you also have to configure and monitor each tool, and ensure that it integrates seamlessly into your pipeline. This is often complicated and exhausting, as each tool requires different implementation, configuration and management, on top of the fact that they don't communicate with each other. Jit simplifies this experience by enabling you to easily integrate security tools throughout each stage of your CI/CD pipeline, and to monitor them from one platform.
3. Implement SSDLC
SSDLC (Secure Software Development Lifecycle) is a methodology that emphasizes security throughout the entire software development process, from requirements gathering to deployment. Secure software includes incorporating security requirements into the development process, performing regular security testing, and implementing security controls.
4. Perform a risk assessment
Performing a risk assessment includes gathering information about potential vulnerabilities and threats, how often they may appear, and their impacts. The tester can then use this information to prioritize vulnerabilities that need to be addressed and develop a plan to mitigate those vulnerabilities.
5. Provide security training for developers
Unsurprisingly or not, 30% of developers feel like their in-house security training could be improved. Developers play a critical role in the security of web applications- whether they see it or not.
They must understand how to write secure code and identify and address potential vulnerabilities. But to do this, they must be adequately trained through educational resources and hands-on exercises. If you want to make it even easier for them, Jit offers a native dev experience, so your developers don't have to learn or log into any other platform. Jit runs on their PRs, and only runs on the changes. It only highlights in-context vulnerabilities, and it also provides remediation suggestions so they can fix it just in time.
6. Use various security layers
Security testing doesn't just come up in the testing stage. It's essential to use a variety of security measures throughout all phases of the SDLC, such as the ones we mentioned earlier, to ensure that all potential vulnerabilities are identified and addressed. The more, the better.
7. Automate security tasks
Automating vulnerability scanning, penetration testing, and security compliance checks can help ensure that these tasks are completed regularly and promptly. Additionally, automating these tasks can reduce the workload for security and engineering teams, allowing them to focus on more critical tasks. Jit offers an orchestration layer that makes it easy to automate security tasks and integrate security tools into the software development process, like a command center that controls all the security functions.
8. Patch and update regularly
Regularly patching and updating web applications ensures that known vulnerabilities are addressed and that the web application is up-to-date with the latest security features. It may seem like a primary step (and it is!), but the most basic measures often need to be more recognized and remembered. Make sure you plan for each update to prevent incompatibility issues between APIs.
9. Adopt a Continuous Security Monitoring tool
Traditional security controls, like firewalls and antivirus software, are not enough anymore. To detect real-time threats, you need real-time visibility 24/7. While it's humanly impossible to be looking at code 24/7, the software can do it for you. Continuous Security Monitoring tools help identify potential security threats and vulnerabilities in real-time, allowing organizations to take proactive measures to address these issues. Plus, they take some of the pressure off developers by automating most of the processes.
10. Document your results
Documentation includes reporting the identified vulnerabilities, the actions taken to address those vulnerabilities, and the consequences of any testing performed. The business can use this information to track the progress of security efforts and identify trends in vulnerabilities, like an after-action report to improve future strategies. This documentation also serves as evidence of a company's commitment to security and can be used to demonstrate compliance with industry regulations.
Measuring and benchmarking security (and documenting these) are also key steps in gaining a deeper understanding of your DevSecOps processes. Sure, you may be aware of best security practices and implement these in your team. But without measuring security in quantifiable terms, do you really know what needs to be changed? DORA Metrics like Change Failure Rate (CFR) and Mean Time to Recovery (MTTR), which are traditionally used in DevOps, can be applied to security in addition to Mean Time to Resolve, Detection Rate, Exposure Window and more. Metrics should be tracked on an ongoing basis to keep up with the fast-paced engineering processes.
Don't leave Web Application Security to chance
While security experts may have different ways of protecting web applications, some measures are non-negotiable. It may be overwhelming at first, but it will undoubtedly get easier once you have implemented all the basic security measures and your team has access to the right tools. Producing secure software is a win for everyone. Learn how Jit can help you master your application security toolchain, and get started for free.