Every asset in your cyber-physical systems (CPS) environment can also be a vulnerability. Without having complete asset visibility, companies are operating in the dark, leaving potential security gaps unattended and significantly increasing exposure to cyber-attacks and data breaches.
43% of companies plan to invest in exposure management this year, so organizations are already working toward becoming more proactive in detecting, monitoring, and mitigating risks within their systems.
However, this preventative approach can't be successfully implemented without a clear first step: ensuring you have complete visibility into each asset, its potential security gaps, and how it is being used.
What is asset visibility?
Asset visibility encompasses several methods to detect all devices on your network and develop a comprehensive inventory of all cyber-physical assets. It helps businesses track the entire lifecycle of their devices, including their location, status, how they are utilized, and how they interact with each other.
Not all visibility methods offer the same level of information to secure IoT assets and OT specifically. The optimal level of visibility reveals key identifying attributes such as the asset's model, firmware version, and configuration information. You need this in-depth information to detect all hidden vulnerabilities across your network.
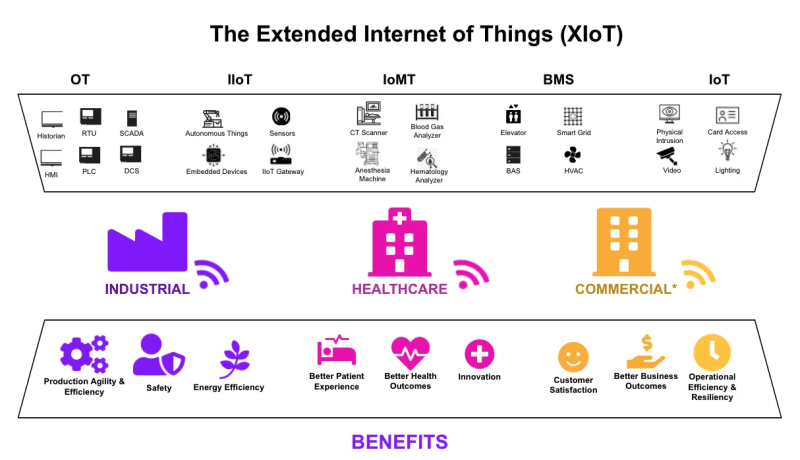
To achieve complete asset visibility, you should be able to detect and monitor a wide range of devices, including IT, OT IoT, IoMT, and the full spectrum of XIoT devices. Visibility also plays a significant role in uncovering unknown and end-of-life assets, which are typically outdated and may have security gaps. These gaps can have many concerning consequences, impacting everything from data privacy to physical safety.
In addition to asset detection, visibility improves overall cyber security hygiene. It strengthens your security posture, enabling you to respond to threats promptly before they escalate into full-scale attacks. Without asset visibility, it's impossible to fully know which devices need protection, making it easy for attackers to slip through the gaps or exploit vulnerabilities on devices you weren't aware even existed.
Asset Visibility vs Asset Management
Asset visibility refers to discovering every asset on your network to offer protection from cyber threats. Gathering information about these devices allows you to better understand how to protect them.
On the other hand, asset management is the logical next step after visibility, which includes acting on the information gleaned from discovery to secure the device, from proper exposure management to essential steps like risk scoring.
The Benefits of Asset Visibility
Better threat detection - to stay on top of potential threats or vulnerabilities in the devices on your network, you must be able to monitor your assets continuously. Visibility is the first step in enabling total asset management.
Operational efficiency - asset visibility leads to a higher level of protection, meaning fewer viruses or malware that could lead to downtime. When all devices are detected on the network, you can remain more confident in your security posture and overall efficiency.
Compliance - monitoring and managing all devices on your network is critical to meeting all industry regulations to avoid penalties or fines. For example, compliance with HIPAA requires all healthcare organizations to securely manage and dispose of assets that contain patient health information (PHI).
Exposure management - By mapping communication paths and protocol usage, you can monitor threats and generate unique risk scores based on the exploitability of your devices, ensuring you can identify, assess, and address exposures.
Asset visibility is especially important when you consider that organizations in the healthcare industry are more reactive than proactive when identifying asset and supply chain risk, as determined in a KLAS survey that identified asset visibility as a weak spot across the healthcare industry.
Why do you need asset visibility now?
From proactively managing cyber risks, optimizing operational efficiency, adhering to regulations, and protecting your brand reputation, it has never been more critical for enterprises to have asset visibility. Every industry needs to fully implement asset visibility to secure its CPS.
The challenges we face from cyber security threats are only increasing in sophistication as the complexity of CPS environments grows. With more remote work comes greater network connectivity and a more significant number of entry points for adversaries to gain access to the network.
Taking measures to prevent cyber-attacks means preventing operational failures, like supply chain threats and other disruptions to critical workflows. This is also key to preserving reputation management and fulfilling your organization's mission.
6 Ways to Improve Asset Visibility
1. Establish network visibility
To have visibility of every asset on your network, it's vital to ensure you have complete network visibility first. Deep packet inspection and network monitoring tools help you understand how data flows between your devices and gather relevant insights into what is happening within your systems.
However, there isn't a one-solution-fits-all solution available, and some tools may not be advanced enough to monitor complex industrial control systems (ICS) and operational technology (OT) systems. Using specialized network monitoring tools and methods will enable you to capture the proper protocols, avoid data transmission latency, and continue operating efficiently.
2. Deploy network traffic analysis tools
Your network traffic includes signals from every device on your network. Some devices will contribute more traffic than others, but that doesn't mean they are more or less critical. By analyzing network traffic, organizations can detect abnormal behavior like unauthorized access attempts and unusual data transfers and spot security misconfiguration vulnerabilities that could be exploited.
Analysis tools must be able to understand every protocol coming through your network. Deploying tools that can accurately detect the hundreds of proprietary protocols, spanning all of your OT, BMS, IoT, and other XIoT assets, is imperative to maintaining complete visibility and taking the next step to manage your assets.
Source: https://www.spiceworks.com/tech/networking/articles/network-traffic-analysis/
You should also monitor user activity logs to understand how your assets are being used and identify potential threats. You can then add the relevant access control measures to your broader IT security policy, ensuring that users have only the privileges they need to perform their tasks and avoiding privilege escalation.
3. Implement endpoint detection and response (EDR)
Network security focuses on protecting the network infrastructure via specialized monitoring tools, firewalls, and encryption protocols. These tools primarily analyze the data flow within the network to detect suspicious activity. On the other hand, endpoint security solutions aim to protect specific devices or endpoints, such as IoT devices and servers.
You should combine both approaches and employ endpoint detection and response (EDR) tools to protect the IoT. An EDR, like the CrowdStrike Falcon platform, responds to cyber threats by continuously monitoring end-user devices. You can improve your security posture by pairing it with other continuous threat detection methods (CTD).
4. Regularly conduct asset discovery and classification
Networks and devices aren't static, so OT asset discovery should be continuous. You should systematically scan your network to identify all connected devices and ensure they are protected. Ensure you leverage various asset discovery methods such as segmentation, active and passive discovery, Claroty's proprietary AppDB, and OT-specific techniques.
Regarding classification, knowing exactly what type of devices are active on your network, their model, and other identifying details can help determine the proper protocols to use with them. It also helps improve resource efficiency, as you'll know what devices to prioritize.
5. Consider segmentation
Network segmentation involves dividing the network into separate, isolated segments based on factors such as asset criticality, function, or security requirements. Segmenting different assets can make it easier to track which devices can communicate with one another, track the number of devices on your network, and control overall traffic. To better manage your network, Claroty xDome supports segmentation to define and enforce policies.
Source: https://www.getapp.com/resources/internet-of-things-security/
6. Utilize passive asset discovery methods
Passive scanning is a way to take data from your industrial network and process it in a passive, one-way transfer that offers visibility without any chance of disruption. Downtime or disruption caused by improperly deployed active methods poses a risk to your network, whereas passive methods ensure complete visibility without risk of harm.
7. Consider visibility orchestration tools
The unique nature and often complex communications of CPS render them challenging to discover and profile through passive-only means. Visibility orchestration serves as an additional tool to ensure organizations are deploying the right visibility techniques for their unique environment. With this tailor-made nature of discovery paired with continuous, automated enhancement to visibility, organizations can more quickly operationalize their asset inventory and an overall faster time-to-value.
Gain Optimal Asset Visibility
Improving asset visibility is critical to proactively detecting threats across IT and OT assets. The steps suggested in this article are the first of many to secure your assets fully. They should be done in tandem with a comprehensive plan to protect devices beyond initial detection and discovery.
A trusted CPS security partner like Claroty's xDome platform helps you gain asset visibility and immediately take the necessary steps to secure those assets. With a full-service platform, you can identify the assets needing protection and offer that protection all in one. Request a free demo to learn more.