Only 43% of companies evaluate new products' data security and privacy before launch. And security is just one chapter of the story: how do companies optimize for security, reliability, performance, and costs all at the same time? FTR can help AWS Partners (those part of the AWS Partner Network) to review processes and tools to improve their solutions' quality. Plus, they get a shiny "AWS - Qualified Software" badge at the end.
While AWS Foundational Technical Review is free price-wise, it doesn't come for free. You must follow a long list of criteria to earn the certification, which involves thoroughly auditing your systems. This article explores how to approach FTR and some steps to get FTR-ready.
What is an AWS Foundational Technical Review (FTR)?
The AWS Foundational Technical Review (FTR) is a structured self-assessment process that evaluates the architecture of your software solutions. There are several versions of the FTR, one for solutions hosted in AWS and one for those hosted outside. The FTR process will take you through self-evaluation, a review process, and a remediation timeframe of up to six months at its conclusion. However, it doesn't end there - you must file for a renewed review every two years and adhere to any updated requirements.
The FTR has some overlap with the popular AWS Well-Architected Framework, which consists of six key pillars: Operational Excellence, Security, Reliability, Performance Efficiency, Cost Optimization, and Sustainability. While the AWS Well-Architected Framework is recommended for every business, FTR is a smaller version, targeting AWS Partners. These guiding principles help ensure the quality and security of your software applications and reduce cloud costs.
Getting Started with Your Foundational Technical Review
The process for getting FTR approved is straightforward:
- Join the AWS Partner Network (APN): If you still need to register your company with the APN, join at no cost by creating your AWS Partner Central Account.
- Enroll in the software path: The FTR is part of the software path.
- Perform a self-review: Time to get busy. Establish a systematic review process and evaluate your architecture against the FTR Guide. If you find any shortcomings, take the necessary steps to remediate any issues before proceeding.
- Request an FTR review: Upon receiving your request, a Partner Solution Architect (PSA) will contact you and provide you with a checklist to complete upon receiving your request. He will review the submitted documentation and give you the all-clear or a list of required improvements.
You can (and should) take advantage of AWS's well-architectured tools, which will ask you questions and offer insights into potential issues you may encounter. Naturally, the tools will give you an overview of the Well-Architected Framework, but it can also provide insights into what needs improvement or fixing. You may also create custom lenses for your specific needs.
While the process may seem straightforward, things get more cumbersome once you reach step 3. Reviewing the official FTR checklist requires you to review each item individually to review compliance. You must check off every item to pass your assessment and provide notes describing how you pass the requirements, so detail is of the essence here. Optionally, AWS recommends you to enable the CIS benchmark in SecurityHub and upload a CSV with the results of the automated checks as evidence. Lastly, you have to upload your architecture diagram.
As you can tell, this task is highly manual and can take weeks, months or up to a year, depending on how secure your system is and the resources you have available. Jit can make this process more seamless and help you pass your FTR assessment without headaches. The AWS FTR security plan on your Jit account automatically maps the gaps related to the security requirements, thanks to various tools which scan your AWS environment and code and provide you with remediation as code and detailed guidelines. After following the recommendations or applying the remediation as code, your environment will be scanned again to ensure all the gaps have been covered.
Critical areas of the AWS FTR (Foundational Technical Review)
Reliability
A reliable system is a system that has safeguards and recovery plans in place in case of disruptions, as well as the ability to adjust computing resources based on demand.
- Monitoring Activity: Monitoring and logging help you track and identify reliability issues. AWS provides services like Amazon CloudWatch and AWS X-Ray for this purpose.
- Testing and Mitigation: Performing regular stress tests will help identify bottlenecks or weak points in your system that could impact reliability.
- Backup and Restore: Regular backups and fast restoration strategies are crucial for maintaining data integrity. You can use AWS services such as Amazon S3 and AWS Backup.
- Disaster Recovery Plan: You must have a detailed plan for critical failure. Outline the program, and ensure your staff is aware of the procedures.
Security
Cyber attacks are an ever-present threat to connected resources, particularly cloud-based applications.
- Identity and Access Management (IAM): Create and manage AWS users and groups and use permissions to allow and deny their access to AWS resources. Follow the principle of least privilege when assigning roles to increase security.
- Logging and Monitoring: AWS offers services such as AWS CloudTrail for API logging and activity monitoring, Amazon CloudWatch for monitoring resources and applications in real-time, and AWS Security Hub for managing security alerts and automating compliance checks. Having robust logging and monitoring helps identify problems and fix them faster.
- Shifting Security Left: Security testing should be performed early in the SD/LC to prevent vulnerabilities from making it into the late stages of development and save time and money on remediation. You can use many security tools here, in particular looking for hard-coded secrets which are tied to one of the FTR requirements, which Jit can orchestrate into your CI/CD.
- Data Protection: Especially important for personal information, data encryption in storage and transit is essential for FTR and any other compliance regulations you must adhere to.
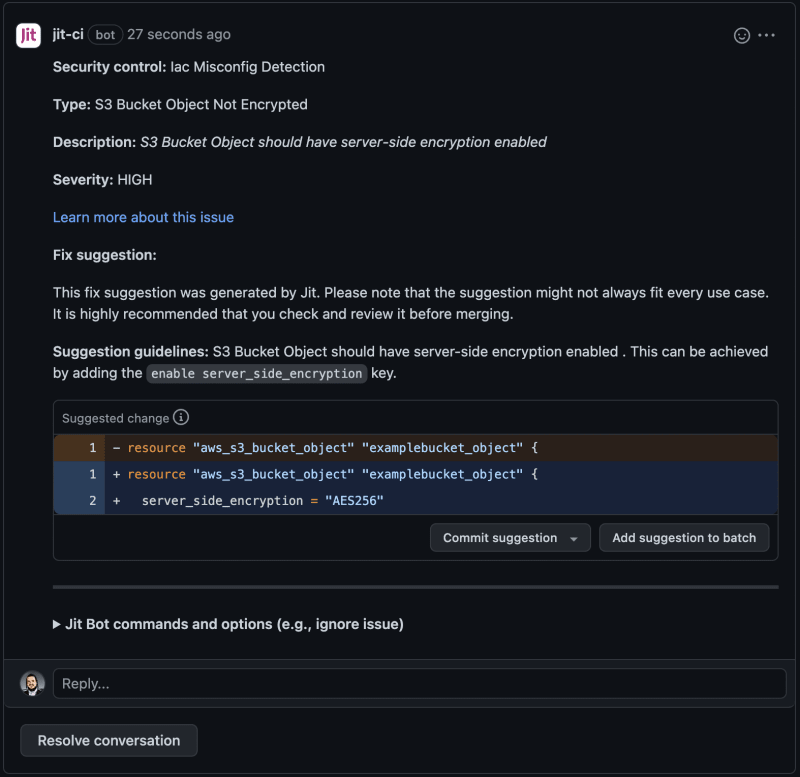
- Security Assessments: Perform regular security assessments and testing. You can use cloud security tools like KICS and Kubescape if you're cloud-native or hybrid. Jit can integrate with these and many other tools, enabling you to automate and manage various security tests from a single location. Plus, you get enhanced findings with insights from other tools and real-time fix suggestions - as shown in the example below.
FTR is a win-win situation
A well-architectured solution is the way to go, and the FTR is an excellent way of ensuring your application meets those guidelines. Following this checklist of critical points you must address will prepare you to undergo the official FTR process and get your well-deserved badge (with the added perk of having a fully secure and stable system). However, this process is still highly detailed, manual, and time-consuming.
Jit's AWS FTR Security Plan lets you automate the process of meeting FTR security requirements. It offers better visibility into your architecture's security gaps directly related to the AWS FTR application process, making it easier for you to remediate these and pass your FTR assessment. Get started for free.
One ticket to AWS first class, please! That's not actually the official designation, but an Amazon Foundational Technical Review (FTR) certification can fast-track you into many currently locked perks and allow your organization to boost stakeholder and customer trust, thanks to the Amazon Partner Network (APN).