Developers, heads of security, and product teams are noticing significant changes. Similar to how quality assurance (QA) became part of the Software Development Life Cycle, security is also becoming part of the SDLC.
However, despite this step in the right direction, a lack of processes and standardization, broken code, and bugs still pose huge hurdles for software teams on the journey from planning to launch.
The amount of risk involved before new software is launched means that SDLC is one of the most active research areas in the industry. A recent article from the Journal of Computer Science Research emphasized the importance of designing SDLC procedures to reduce risk and protect against cyber attacks. Their conclusion? SDLC security should be the number one priority for every software development team.
In this article, we will explore new trends in SDLC security and how you can choose the right methodology for your business to ensure that your software is safe and secure.
What is a Software Development Life Cycle?
The software development life cycle first appeared on the scene back in the 1960s as a way to process large amounts of data. Since then, methodologies such as Scrum (1993), Rational Unified Process (2003), and the Agile Unified Process (2005) have emerged.
The SDLC is a well-planned-out set of steps, or framework, that enables a business to produce advanced software that has been thoroughly tested and is fully functional. These steps change depending on the industry, size, team, time frame, and budget.
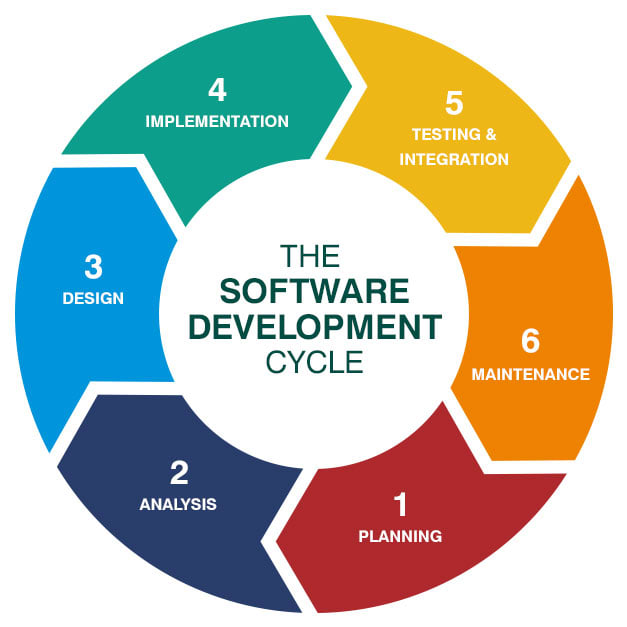
What are the Stages in a Software Development Life Cycle?
An SDLC generally consists of seven distinct steps.
Step 1: Planning and Requirements
At the planning stage, team members such as stakeholders, business partners, engineers, and clients set out goals for the software's usage, resources required, output, audience, time frame, cost, and more.
Step 2: Analysis
A business analyst prepares the SRS (Software Requirements Specification) document after the requirements and planning stage is complete. This document will be the guiding light for your developers, and they should read, understand and review it regularly.
Step 3: System Designing
At this stage, you are ready to implement your requirements into your architecture. System designing defines the overall software architecture and helps to describe hardware and system requirements.
Step 4: Development
Now that your design documentation is clear, it's time for the development stage. The entire development program is divided into working units between the software engineers.
Development is the most critical step, so it should be close to perfect. You could appoint a Security Champion to promote security awareness, culture, and competence throughout the entire SDLC. Security Champions encourage developers to think about application security constantly, which results in better code, accessible reviews, and secure releases.
Step 5: Testing
Testing encompasses non-functional and functional testing, such as acceptance, integration, system, and unit testing. By examining the software's coding quality, your Quality Assurance team can check to see if the initial business requirements have been satisfied.
Step 6: Implementation
Also called the 'deployment phase', implementation starts after testing is complete. This step often involves installing or delivering the program to the client. When the project is handed over, the work is not finished yet: beta testing starts immediately, and development staff is informed of any issues and improvements. After the changes have been completed, the final deployment happens.
Step 7: Maintenance
Maintenance happens over time after the program has been launched. Performance can be assessed and improved throughout this stage, and the product may also get updated with new features.
How to Choose the Right SDLC Methodology for Your Company?
The SDLC approach you choose will depend on several factors, including the requirements of the stakeholders, the project's business goals, the technical team's skills, and technical and budgetary restrictions.
Here are some of the primary SDLC methodologies you need to know.
Waterfall
The waterfall model is one of the oldest approaches, dating from the 1970s. However, it still has relevance in the modern-day business world.
This methodology's stages are straightforward, making it simple for all team members to follow them without any prior training.
However, there is not much opportunity for adjustments once each stage is finished because, in the waterfall model, problems can't be solved until the project reaches the maintenance stage. Hence why this strategy doesn't perform effectively if flexibility is required.
Iterative
The iterative model is all about repetition. Project teams execute a set of software requirements, test, assess, and identify further needs rather than beginning with fully known requirements. Each stage, or iteration, results in creating a new version of the program. This process is repeated until the entire system is ready.
5 Ways SDLC Security has Changed in 2022
1. Focus Group Studies
Focus groups are discussions designed to gather the group members' individual perspectives on a specific topic of study interest. An excellent focus group can produce honest, insightful data and be a quick and easy tool.
This strategy results from the growing UI/UX significance in recent years. By gaining insights from participants and users at the source, you can better understand the best and worst parts of your software's user experience.
The iterative model results in a workable version of the project early on and reduces the cost of making adjustments. But these repeated actions can quickly deplete resources.
2. Spiral
The spiral model runs through the four phases of planning, risk analysis, engineering, and assessment repeatedly until it is finished, allowing for several iterations of improvement.
The spiral model is the greatest development model since it incorporates risk analysis and risk management at each stage, which is one of its key features. But in contrast, it is not appropriate for minor projects due to its high cost and sophisticated process.
And why is user experience important? A recent State of the Connected Customer report discovered that 80% of respondents value customer experience as highly as a company's goods or services. One in three even cut ties with a brand after just one bad experience, according to PwC.
3. Go Agile
The agile software development life cycle is most frequently used to create complex solutions. It is a process for designing digital solutions that allow more flexibility in product development, cuts down on time to market, and makes it easier to incorporate changing customer demands.
4. Behavior-driven Models
Behavior-driven development (BDD) is like a test to show how the system behaves. It encourages everyone participating in the development process to utilize discussion and real examples to better understand the system's behavior.
A user's expected behavior when engaging with an application is documented and then designed into the application using BDD, which is an agile software development process.
4. Better Workflows for Better Visibility
Companies with distributed teams and engineers that work remotely need a tool to communicate, discuss, and exchange ideas. Examples of such a tool include Slack, Microsoft Teams, Zoom, or Jitsi Meet.
Programmers can optimize their workflow and guarantee greater quality output by streamlining their tasks and concentrating on one at a time.
You need to consider aspects like team size, client expectations, and company capacity when determining your Work in Progress (WIP) limit. Controlling and adjusting your WIP limit is crucial when external conditions change.
5. DevSecOps
While security teams continuously monitor all facets of the DevOps process, DevSecOps has incorporated security into every component of the software development process.
By making security a first-class priority in a software development life cycle, companies can make their software safer.
DevSecOps approaches will be used by 90% of software development projects in 2022, up from 40% in 2019. It's no surprise that DevSecOps will displace DevOps as the preferred method of operation for most development teams.
DevSecOps tasks include checking for security vulnerabilities such as cross-site scripting and Insecure Direct Object references, training engineers to write secure code, and carrying out risk and threat assessments.
Security is Always at the Core of the SDLC
Organizations used to wait until the testing stage to do security-related activities. But the later a bug is found, the more expensive and difficult it is to fix.
Integrating security testing across every stage of the SDLC is a better way to resolve the issue. Ox Security uses PBOM technology which sets a new standard for software supply chain security.
Our solution enables you to accelerate product development, deliver safe goods on schedule, and continuously monitor software supply chain security by automatically repairing vulnerabilities in post-product and avoiding them during development.
Book a demo or try it for free today.