Data breach attacks are as explosive as it gets. In 2020, Microsoft suffered a massive leak involving more than 250 million customer support data. While 250 million certainly sounds like a lot, Keepnet Labs makes the record for over 5 billion records exposed. Companies that experience a breach end up underperforming by more than 15% on average over three years.
Enough bad news for the day? Thankfully, there is a solution for every problem, and implementing appropriate security tools will go a long way in protecting your systems. This article will guide you through the ten best Continuous Security Monitoring tools for 2023.
What is Continuous Security Monitoring (CSM)?
Continuous security monitoring (CSM) is a security practice that continuously assesses an organization's security posture and identifies security risks in real-time. CSM is a proactive approach to security that can help organizations identify and respond to security threats before they cause damage.
The perks of CSM are that it supplements other security practices, such as vulnerability management and incident response. When implemented correctly, CSM can help organizations reduce their overall security risk. CSM can also help organizations improve their security posture by identifying security risks early and taking steps to mitigate them.
Continuous Security Monitoring benefits
Organizations are under constant attack from sophisticated cybercriminals. Active monitoring is required to defend your organization against malicious activity.
Here are the significant benefits of CSM:
- It helps identify potential security risks and vulnerabilities early before they can be exploited.
- It can reduce the impact of a security breach or attack by providing timely detection and response.
- It improves an organization's security posture by providing visibility into potential risks and vulnerabilities.
- Can save time and resources by automating the monitoring process.
- Can improve compliance with security-related regulations and standards.
How do Continuous Security Monitoring tools work?
Continuous Security Monitoring (CSM) tools enable developers to detect and respond to security threats in real-time.
CSM tools collect data from various sources, including network traffic, system event logs, and user activity. These tools then analyze the data for signs of suspicious or abnormal activity. If a potential security threat is detected, the CSM tool will generate an alert to take appropriate action.
To be effective, CSM tools must be constantly updated with the latest security intelligence. They must also integrate with other security tools, such as intrusion detection systems (IDS) and firewalls. This allows for a more comprehensive view of an organization's security posture and helps to ensure that potential threats are not missed.
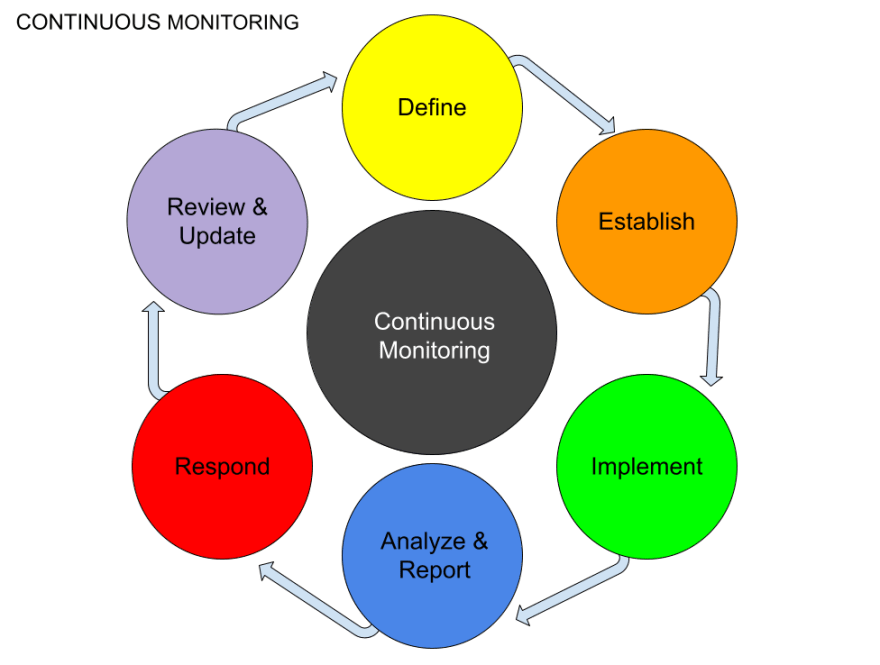
Types of Continuous Monitoring
Continuous Monitoring is the process of monitoring and assessing security controls on an ongoing basis. It is an integral part of an organization's security program, as it helps identify and resolve issues promptly.
There are three main types of continuous monitoring: infrastructure, application, and network.
Infrastructure monitoring
Infrastructure monitoring is the process of monitoring the physical components of a system, such as servers, storage, and networking equipment. The main benefit of infrastructure monitoring is that it can help identify problems with hardware or other physical components of the system. For example, a server constantly running at a high temperature may indicate a hardware issue.
Application monitoring
Application monitoring is the process of monitoring the software components of a system. These components include the application code, the application server, and the database. Application monitoring can help identify problems with the application code, such as slow performance or memory leaks.
Network monitoring
Network monitoring is the process of monitoring a system's network traffic, including the router, switches, and other networking equipment. Network monitoring can help identify problems with the network, such as high latency or packet loss.
Top 10 Continuous Security Monitoring (CSM) tools for 2023
To implement CSM properly, you will need robust tools. Here are the top ten Continuous Security Monitoring tools available:
1. Nagios
Nagios is a monitoring system that watches mission-crucial infrastructure and has multiple APIs allowing easy integration with in-house and third-party applications. Being open source, there are also thousands of community-driven add-ons and extensions for monitoring and native alerts.
Pros:
- Extendable architecture
- Offers Service-Level Agreement (SLA) reports
- It comes with a configuration wizard
Cons:
- Web UI can be confusing to navigate
- Can produce frequent false positive alerts
- There is no GUI-based config, and everything needs to be done through the command line
Customer review:
"Nagios does standard monitoring of servers and network devices very well. If you have an environment with many basic protocols to monitor, Nagios will work well out of the box for you. It also runs very reliably. Once it is set up, I have not had many problems with the service being available." - Chris Saenz, Lead System Engineer
2. Jit
Jit is a DevSecOps orchestration platform that simplifies integrations with open-source security tools. With Jit, developers can easily integrate security tools and controls into their CI/CD pipelines, and protect their application stacks from code to infrastructure, as well as the entire supply chain. By leveraging best-of-breed OSS security tools, such as Gitleaks and OWASP ZAP, it is possible to apply popular security plans as code like custom AppSec programs, compliance plans - such as SOC2, and even OWASP Top 10, through simple security controls. Jit also helps DevOps teams build an effective security plan and integrate continuous security into their workflows with minimum effort.
Pros:
- Dev-friendly - built for developers with a focus on dev experience across platforms
- Fix-first focused, making it easy to find the code to remediate and fix issues fast
- Orchestrates and unifies all tools, so developers don't need to learn each tool
Customer review:
"I love the notion of Jit providing as-code security plans, which are minimal and viable. The fact that Jit also automates the selection of relevant security tools and unifies the experience around them is super valuable." - Director of Engineering & CISO @ SaaS platform
3. Syxsense
Syxsense is a security vulnerability scanning tool that allows you to see and remediate endpoints. It comes with a drag-and-drop interface, the ability to see your security issues in real-time, and quarantine devices from further access.
Pros:
- Ability to remote into a system, create updates and patches
- Intuitive interface
Cons:
- Remote access can often freeze and locks up the system from reconnecting
- Admin portal can sometimes be slow
Customer review:
"Syxsense solves the issue of keeping our machines up to date without having to touch each machine manually. It is a great support tool. Also, I have had issues where a user is missing something critical on their machine. Building a package is rather easy as well. They also have support options available to assist." - Derek E.
4. Splunk
Splunk is a "unified security and observability platform." You can use Splunk to watch your endpoints, capture log files, and present them in a meaningful and analytical-based output.
Pros:
- Ability to make your security logs more mentally digestible
- Ability to create automated alerts and reports
Cons:
- Not very easy to use- steep learning curve
- Requires a good understanding of Linux and systems administration skills
- It can be resource-heavy for the host machine
Customer review:
"So simple for Splunk to capture all the data that runs on an enterprise's applications. Splunk acts as the repository to take this data and then allows us to slice and dice the data as we wish to generate reports, improve analysis, get a better handle on our business, improve productivity, improve business/market intelligence, react more quickly to trends, take decisions more proactively, etc." - Azhar C., IT Security & Compliance Analyst
5. Lightrun
Lightrun is an IDE-native observability and debugging platform that allows developers to add logs and metrics to create traces in a live environment. Tools like Lightrun can be handy for error management and bug tracing, as there's no need for redeployments or restarts when code is added through Lightrun.
Pros:
- It requires live production application access
- Cut down on logging costs because you can generate these on the live application during the debugging process
Cons:
- Lightrun is more a post-production assistance tool rather than a preventative tool
Customer review:
"Great tool for faster incident resolution and real-time debugging without needing to add new code" - Shir M, Software Engineering Intern at Google
6. Spectral
SpectralOps is a scanning tool that can be integrated within your CI/CD system to automatically identify security blindspots and sensitive assets like secret keys, unsecured API endpoints, credentials, and misconfigurations in real-time. It scans your entire codebase and sends instant notifications once an issue is detected, enabling your team to easily and quickly resolve it.
Pros:
- Ability to quickly identify, monitor, and classify your sensitive assets from potential secrets exposure
- Specializes in secrets discovery in codebases
- Minimal configuration is required to get started
- The tool is language-agnostic and supports more than 500 stacks
Cons:
- Specializes in code vulnerabilities
Customer review:
"One of the reasons we picked Spectral over the other products is Spectral has low false-positive results, which give us a high confidence factor and save us precious development time." - Nimrod Peretz, VP R&D, Wobi
7. Cloudflare Flow-Based Monitoring (Magic Transits)
Cloudflare is a cloud infrastructure platform with a network traffic monitoring system called flow-based monitoring (now called Magic Transits). It deals with keeping your cloud systems up by diverting DDoS-detected network traffic away from your main cloud infrastructure setups.
Pros:
- Stable and good with DDoS protection
- Easy to scale
Cons:
- It can become costly to maintain
- No clear live tracking is available
Customer review:
"Easy to use, good documentation, reasonably priced, and they have good support" - Andrii Prager, CTO at QROK GmbH
8. MemcyCo
MemcyCo is a Proof of Source Authenticity (PoSA) tool that enables companies to protect their digital assets from impostor attacks such as brand identity theft and phishing scams. MemcyCo surveils all communication touchpoints between the company and its customers, partners, or employees. If an attack is detected, this tool automatically notifies the company before the attack reaches the end user. MemcyCo also offers an authentication watermark that can be used on companies' websites or emails, which helps build customer trust.
Pros:
- Real-time tampering detection
- Secure and customizable watermark that can't be forged
- Can be easily installed with one line of code
Cons:
- Email and SMS authenticity verifications are additional tools, paid separately
IoT Monitoring
At the end of the cloud are the Internet of Things devices. These devices need to be monitored for power and data efficiency. Here are two of the best IoT monitoring platforms available.
9. FirstPoint
FirstPoint is a targeted cellular IoT monitoring platform that protects entire IoT networks and the data transmitted between IoT-connected devices. You can use FirstPoint to prevent new and emerging threats such as identity compromises, eavesdropping, unauthorized location tracking, malicious SMS, and data leakage. This tool is customizable to any use case and scalable to fit business needs.
Pros:
- Covers 2G to 5G range
- Available for both on-premise and in-cloud options
- Centralized online management platform
Cons:
- Limited to cellular IoT
Customer review:
"FirstPoint's unique and innovative solution provides an added layer of protection at the cellular signaling network level, a true industry first," Eric Williams, Founder, CEO & Innovator, iJura
10. Galooli
The power bill can quickly grow for businesses that manage their on-premise infrastructure if everything remains on all the time. Galooli is an IoT monitoring and management platform that ensures efficient energy management and operational savings.
Pros:
- Supports various industries, including data centers, telecommunications, mobility, utilities, and renewables
- It is easy to use and understand interfaces
Cons:
- Limited to Enterprises
- Focused on physical IoT assets and not cloud-based infrastructures
Customer review:
"Its easy access and user-friendly interface made me like the software; even a novice could make use of the software if you give them a simple explanation on how to use the software." - Arinze.
Whatever you choose, you still need a security plan
CSM tools are essential to respond to threats in real-time. However, to ensure maximum protection across your entire CI/CD system, you need to integrate with various tools and have a solid security plan in place. This can easily get overwhelming for your DevOps team. That's why Jit offers a Minimum Viable Security plan that makes it simpler to protect all stages of your software development. We also work as an orchestration layer to facilitate integrations with all the relevant security tools you need for each stage. Get started for free and continuously protect your product with minimum hassle.