From unmanaged quotas and rate limits to neglecting logging and monitoring, we're discussing Kubernetes multi-tenancy and what to avoid in your architecture.
Dubbed the operating system of the cloud, Kubernetes is one of the most loved technologies by developers and platform engineers today. Though it wasn't initially designed for multi-tenancy architectures, the efficient sharing of cloud resources for faster time to market and scalability is essential for cloud-native application development and SaaS business models.
According to a recent survey, 44% of organizations already use containers for nearly all applications and business segments. It's safe to assume that many of those applications will run on multi-tenant clusters orchestrated by service providers or teams of platform engineers.
But what is Kubernetes multi-tenancy? What are the benefits of sharing cluster resources between teams, projects, and (in some scenarios) clients? And what common mistakes should you avoid in your Kubernetes multi-tenancy architecture?
What is Kubernetes multi-tenancy?
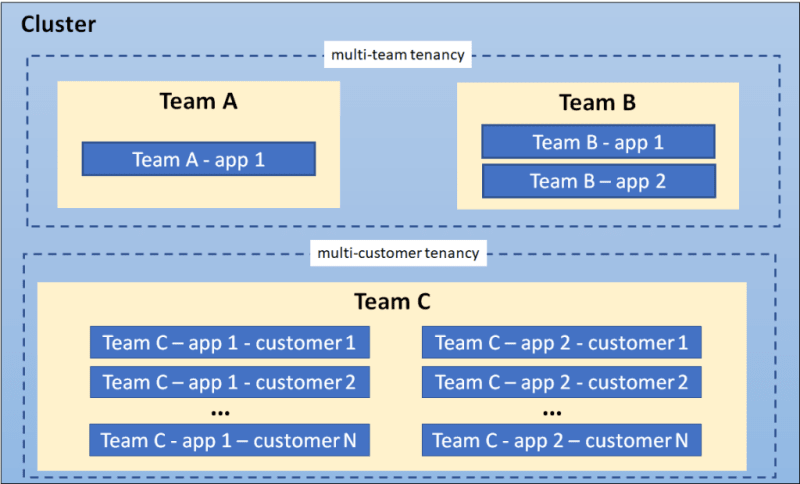
Multi-tenant Kubernetes architecture, often called Kubernetes multi-tenancy, is a container-based architecture that enables multiple clients (known as tenants) to share resources in one Kubernetes cluster to run various workloads. Creating virtual isolation between the tenants ensures that configuration and data are only accessible to the specific team or customer.
There are three primary approaches to running a multi-tenant Kubernetes cluster: namespaces, control planes, or offloading multi-tenancy's technical side to a managed Kubernetes service.
An example of multi-tenancy outside the cloud is co-working spaces. Individuals and businesses can rent a shared office and scale as organizational needs change. Different organizations share the same printers, bathrooms, conference rooms, and internet connectivity and avoid investing large sums of money into renting or buying an entire office building.
The benefits of Kubernetes multi-tenancy
Reduced Costs
The cost benefits of a multi-tenancy architecture model are pretty obvious -- using the same cloud resources for multiple teams or clients makes economic sense. But another advantage is especially important for SaaS startups -- the option to pay-as-you-go for the resources workloads consume.
This type of pricing implies a significant reduction in cloud infrastructure costs. Control Plane can reduce cloud costs by up to 70% due to its serverless mode that allows you to scale up and down as needed and only pay for the computing resources you use (your app usage is billed by millicores and megabytes of memory).
Security and Data Privacy
In efficiently sharing Kubernetes resources between users and workloads, multi-tenancy offers the most secure solution. That said, the data protection and isolation level depends highly on each cluster's configuration and the security tools used.
Scalability and Flexibility
Single-tenant architectures, where each tenant has their own Kubernetes cluster, demand much time and resources to maintain and scale. With multi-tenancy, scalability is baked into the service.
With Control Plane, scalability is seamless and automated, allowing you to accommodate existing and new tenants in near-real-time or scale down to zero. All without having to guess future demand and pay for unused cloud resources.
Ease of use and Customization
Maintaining and protecting Kubernetes is hard labor. Think software updates, patches, availability assurance, backups, performance optimization -- you get the gist. With multi-tenancy, it's all shared among the tenants and requires little to no maintenance on your behalf.
Control Plane provides a cloud vendor-agnostic interface you can use and customize to your needs without in-depth knowledge of Kubernetes and its associated technologies. You can orchestrate an unlimited number of security-isolated Kubernetes clusters in all the regions of the major clouds, ensuring impeccable availability and performance.
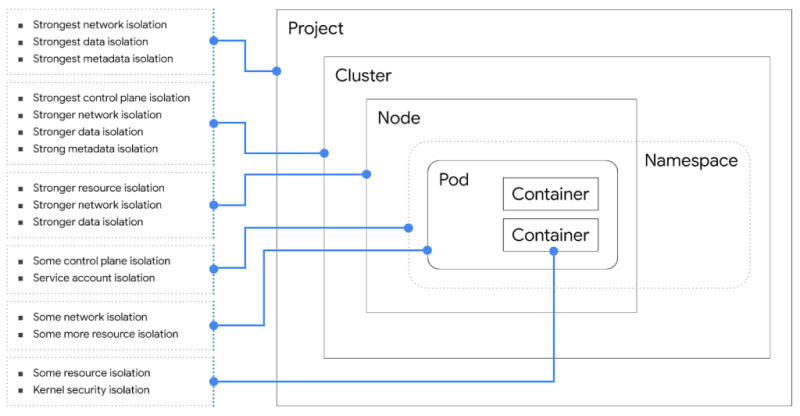
Types of Kubernetes multi-tenancy architectures
Multi-tenancy architectures for Kubernetes can be grouped into general categories according to the level of security isolation between tenants: trusted (soft) and untrusted (hard) isolation.
Before we define them, it's worth noting that "hardness" and "softness" exist on a broad use-case-specific spectrum, with several techniques and tools that enable different types and levels of tenant isolation.
Soft (trusted) isolation
Soft multi-tenancy is usually implemented to avoid accidental interference between trusted tenants. For example, different teams working on distinct features of an application won't need as much isolation within the cluster.
Hard (untrusted) isolation
Hard multi-tenancy stems from the principle that tenants cannot be fully trusted. It may require more security overhead but enforces strict data-plane isolation and restrictions to protect tenants from malicious interference, such as data exfiltration or DoS, or for compliance reasons.
5 things to avoid in your Kubernetes multi-tenancy architecture
Along with the many advantages of multi-tenant Kubernetes architectures, there are hurdles to overcome and common issues that may arise with day 2 operations.
1. Unmanaged quotas and rate limits
One of the fundamental challenges with Kubernetes multi-tenancy is called the "noisy neighbor" effect. With one tenant using up a lot of the cluster's resource pool, it can severely impact availability and performance for other tenants (and potentially their users if the tenants run workloads in production). To ensure that doesn't happen, you need to employ Kubernetes Resource Quotas to manage the resource consumption of tenant workloads.
Resources quotas apply to namespaces in Kubernetes, and when you use the quota, Kubernetes also requires that you specify the number of resource requests and limits for each container. Without automation of multi-tenant resource monitoring and allocation and adequately defined policies for scaling, it's easy for one tenant to monopolize resources at the expense of other tenants.
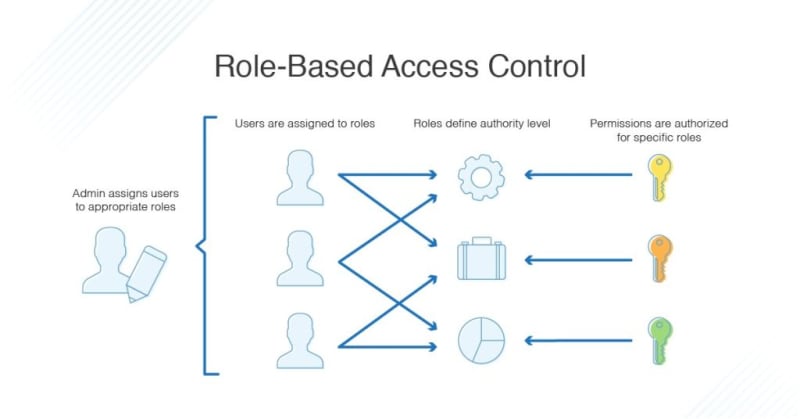
2. Loose or missing security controls
The importance of security and data isolation in multi-tenancy architectures cannot be understated. With tenants sharing resources, they may also share security events. What this means is that as a Kubernetes cluster administrator, you need to implement security policies and enforce best practices, including access control methods like robust role-based access control (RBAC), VPNs, and software-defined network zones, as well as strong encryption, and regular audits of your Kubernetes security posture.
3. Location-dependent performance
If the workloads running on your multi-tenant cluster cater to a global audience, you may find that some tenants are complaining about latency issues. It's essential to consider the target audience of the containerized applications in your Kubernetes multi-tenancy architecture.
One advantage of working with a cross-vendor Kubernetes PaaS provider like Control Plane is the ability to port containerized workloads across clusters and instances seamlessly, with automated geo-optimized performance for all tenants and their users. This ensures extremely low latency and 99.999% availability -- so your app's performance is untouchable.
4. Neglecting logging and monitoring
Observability is king when it comes to successfully a complex multi-tenancy cluster architecture. You must implement logging, tracing, analytics, and multi-cloud monitoring tools to allow administrators to collect critical information about the operations of the cluster and workloads running on it.
Moreover, it's essential to configure audit logs that ensure all the information needed to track user, tenant, control plane, and workload operations is readily available in case of malfunction, security event, or compliance audit.
5. Configuration and management overhead
Self-managed multi-tenant Kubernetes demands that you employ infrastructure engineers who are containerization experts. When you draw out your multi-tenancy architecture, weighing the pros and cons of self-managed Kubernetes versus PaaS vendors regarding personnel costs is essential. This is an especially critical decision for startups experiencing hyper-growth or large fluctuations in tenant resource demand.
Hassle-free Kubernetes multi-tenancy with Control Plane
While Kubernetes multi-tenancy offers many advantages like cost efficiency and reduced maintenance overhead (compared to multi-cluster Kubernetes architectures), it also introduces new challenges to organizations that don't have a dedicated team of Kubernetes experts in their platform engineering department.
Control Plane, a developer-first PaaS suite, offers unprecedented flexibility combined with ease-of-use and enterprise-grade security and tenant isolation baked-in. You don't need to be an experienced platform engineer to deploy your workloads onto your own cross-vendor global virtual cloud and deliver superb performance at a fraction of the cost. Want to learn more? Get in touch with our team.