Attacks on IoT devices can corrupt whole networks and lead to data theft, severe disruptions in operations, or even endanger human lives. According to Kaspersky, there were 1.5 billion IoT cyberattacks in the first half of 2021, 639 million more than in 2020. Despite technological advancements, attackers adapt to security updates, constantly bringing new vulnerabilities. While IoT security will always be a concern, there are practices and tools you can adopt to protect your company's IoT network. This article guides you through the most common cyber security vulnerabilities for 2022 and how to protect against them.
What is IoT?
The Internet of Things is a system that connects objects ranging from common, everyday physical devices to sophisticated industrial tools. These objects can be anything from smartwatches and smart security systems to cellular devices and sensors. The devices are embedded with software essential for connecting and exchanging data with each other. IoT can be applied to any industry, from healthcare to farming and transport. For instance, IoT is commonly used in healthcare to monitor patients remotely or keep track of their medical records through connected devices.
All IoT devices fall under two broad categories --- switches (that send commands) or sensors (that collect data and send it across to some other device). The sensor data is collected by connecting to an edge device or an IoT gateway. The gateway analyzes the data locally or sends it to the cloud. These devices can communicate and act on each other without human intervention.
Top 7 IoT Cyber Security Vulnerabilities for 2022
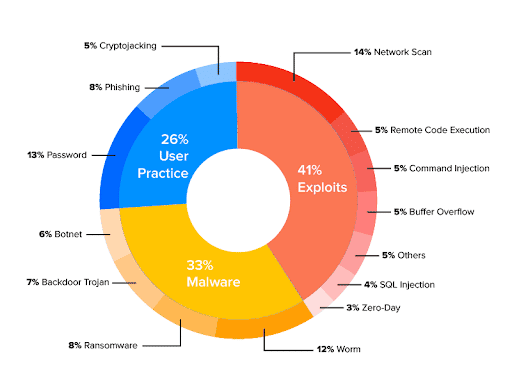
The various types of cyberattacks in 2022, according to a SonicWall report
IoT has brought a fundamental shift and benefits to how we interact with devices and how those devices interact with each other. However, it's important to be aware of IoT cyber security vulnerabilities. Addressing these vulnerabilities by implementing simple strategies and tools can help you secure your devices and detect attacks ahead of time.
1. Weak passwords, settings, and ID verification
Poor password security is one of enterprises' biggest IoT security challenges. We are repeatedly reminded while creating new online accounts how important it is to create a strong password. Unfortunately, not many IoT devices are password-protected. When they are, users generally tend to go with default passwords or options that are easy to guess, leaving these devices vulnerable to breaches. Additionally, many IoT devices, such as smartwatches, rely on ID verification using biometric systems. While these can be more secure than using passwords that are easy to guess, the verification data needs to be stored and managed more securely.
Like most personal devices, IoT devices are shipped with default settings hardcoded into them for simple setup. These settings become predictable over time and are highly insecure.
Solution
It's highly recommended that all IoT devices have at least 8-character long passwords using a combination of special characters, numbers, and upper and lowercase alphabets. Commonly used passwords like "12345", "password," etc., are discouraged. You must also install reliable firewalls in your IoT devices to protect data stored or transferred between devices.
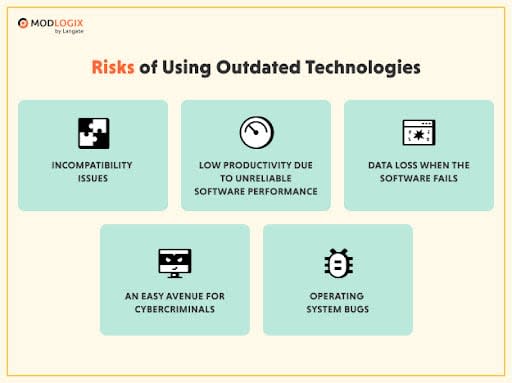
2. Outdated software
Using deprecated software is one of the most significant IoT security vulnerabilities, making the devices and the entire IoT ecosystem easy to get compromised. All combinations of OS platforms, third-party, and open-source software come under this and pose a significant threat to an organization's attack surface.
Software updates are necessary for general maintenance of the software, and when not installed, anything from human malice to system failure can wreak havoc on the whole IoT ecosystem security.
Solution
Using outdated software is a weak link in overall IoT security, and it's imperative to ensure that the IoT devices don't run on obsolete software and are regularly updated and upgraded (when necessary) to keep the data safe.
3. Mismanagement of IoT connectivity
The growth of IoT implies a continuous increase in the number of devices connected to the network. Statista predicts the total installed base of IoT-connected devices to reach 30.9 billion units by 2025. IoT enterprises do not always have a single view of all their connected devices for visualization, monitoring and operational control purposes, especially when devices are spread across multiple platforms. Also, IoT connectivity must be closely monitored to prevent attacks on the system, especially on such a large scale.
Without proper management and security protocols in place, mismanagement of IoT connectivity makes* the entire infrastructure prone to cyber attacks as DDoS attacks, issues related to personal data protection, authentication, device identity theft, and more.*
Solution
Off the mark, the simplest solution to the problem of IoT connectivity mismanagement would be using connectivity management platforms (CMPs) like FirstPoint Secure CMP, which brings cellular connectivity control and its best-in-class cellular cybersecurity to the hands of organizations by providing one central connectivity management platform to manage and protect all their cellular connected assets, in one place.
No matter how many devices are connected, it will give you cellular connectivity and full protection to all the IoT traffic, including Signaling, SMS, and Data, thus alleviating security risks in your hardware, software, and network. CMPs also support any IoT use case and make the whole project cost-effective.
4. Lack of IoT security knowledge and protocols
According to a survey by Forbes, more than 33% of respondents admitted to having a skill gap regarding IoT devices and their operations, and more than 80% of them felt they lacked complete operating knowledge of these devices. Lack of awareness and sufficient IoT security knowledge can greatly hinder securing IoT devices. IT admins may leave out IoT apps and software while running updates since they are largely invisible on the network. Sometimes these IoT devices don't even have an update mechanism, further preventing regular firmware updates.
Furthermore, security concerns vary from industry to industry. For instance, IoT for healthcare focuses on ensuring zero risk to human life, while smart cities need to be immune to hackers manipulating infrastructure and operations. This makes it all the more critical to establish IoT security protocols at the network level.
Solution
Businesses must follow the pre-established cybersecurity frameworks like ISO and NIST cybersecurity framework and refer to them as authentic sources of information. Training the employees on all security best practices is another great undertaking that can help secure the ecosystem in the long run. FirstPoint can bridge the knowledge gap since it's simple to use, so the configuration of security policies in the tool is easy. These policies can also be well-adjusted to the industry and IoT use case.
5. Blunders in the cloud
Most businesses have become overly reliant on the public cloud infrastructure to deploy scalable IoT systems. To that effect, vulnerabilities of the cloud have become vulnerabilities of IoT devices. For instance, hackers can use a misconfigured cloud service or IoT device for malicious activities by changing the logic between API gateways. Similarly, threat actors can exploit Identity and Access Management (IAM) misconfigurations to breach the server and control the cloud services. Not to mention, cloud storage is never as secure as an on-premise data storage system.
Solution
It is recommended to perform regular comprehensive risk assessments on top of having a system for inventory and device identification in place. Implementing monitoring and filtering tools at the beginning and inspecting the cloud infrastructure for control features can also support IoT-Cloud convergence.
6. Poor data protection
IoT devices thrive on data, and vast amounts of it include confidential and sensitive information. This data is collected and exchanged between devices at any given time and is often stored in the cloud. Sub-par encryption during data transfers and storage poses a significant threat to the security of managed, unmanaged, and shadow data collected by IoT devices. Failing to protect it can lead to the imposition of hefty fines, not to mention the loss of reputation.
Solution
The lack of appropriate controls can jeopardize the security of the data exchanged by IoT devices. Hence, it's required that all externally sourced components are built securely and follow industry-standard encryption paradigms. A connectivity management platform also helps protect and manage all cellular data from a single platform while being transferred to the network, making sure it reaches the right hands.
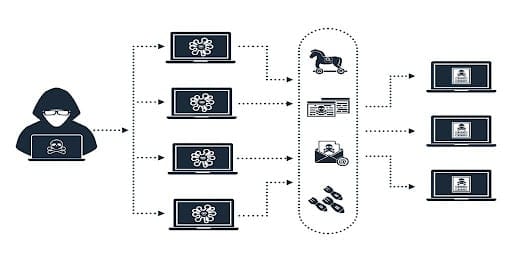
7. Rise of botnet attacks
Botnets are vast networks of small computer systems infected with malicious code, and unprotected IoT devices are vulnerable to such attacks and can be harnessed into large botnets. Botnet attacks on IoT devices typically target data theft, DDoS attacks, and exploiting sensitive information. A botnet attack back in 2016 even interrupted many US customers' connections to Amazon, Netflix, and Paypal.
Source: Reblaze
Solution
Prevention of botnet attacks can be done through advanced routers that know how to filter such traffic using threat intelligence. FirstPoint can protect devices from DDoS attacks in multiple ways, including preventing from receiving the malware originating the attack and blocking sending traffic to unexpected addresses.
How FirstPoint can help
With millions of devices communicating with each other, the same level of security measures needs to be applied across the spectrum. The right security tools coupled with the right approach can go a long way to fix vulnerabilities in IoT devices preemptively, and that's where FirstPoint comes in. FirstPoint is a complete IoT connectivity management platform that ensures maximum security at the network level. Request a demo to see how we can help you.