From financial records to employees' personal details, almost all information nowadays is highly sensitive -- and, therefore, highly valuable to attackers.
With 61% of data breaches involving credentials, it's unsurprising that Identity and Access Management (IAM) is showcasing such rapid growth as a protection method against bad actors. Projected to hit a staggering $24 billion by 2027, the identity governance industry has become critical to any organization's cyber security strategy.
An Identity Governance Framework acts as a roadmap for organizations to implement effective identity governance practices. Building an identity governance framework can be daunting, thanks to the complexity of the IT environment, the desire to balance security and usability, and the need to meet evolving regulations and standards. In this article, we will break it down for you.
What is an Identity Governance Framework?
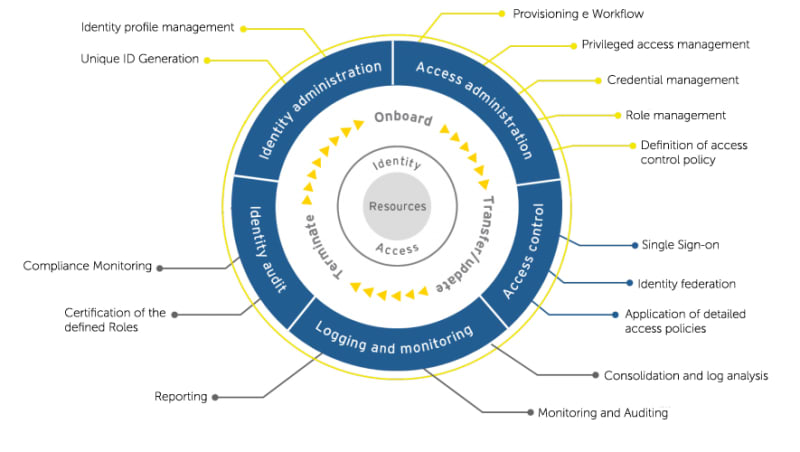
Identity governance comprises the processes and technologies used to manage and control your organization's user identities, roles, and entitlements. By implementing a strong identity governance framework, your organization can minimize the risk of data breaches, unauthorized access, and compliance violations.
Why You Need an Identity Governance Framework
By implementing identity governance, organizations can achieve several key benefits. Firstly, it allows for efficient access management, ensuring that users have the appropriate level of access required for their roles. In addition to improving productivity, effective access management reduces the risk of internal data breaches resulting from excessive privileges.
Secondly, identity governance enhances security by enforcing segregation of duties and minimizing the risk of fraudulent activities. By clearly defining roles and responsibilities and implementing proper access controls, organizations can prevent individuals from gaining unauthorized access to critical systems and sensitive data.
Furthermore, identity governance helps your organization achieve regulatory compliance by ensuring appropriate controls are in place to protect sensitive information. It is essential for finance, healthcare, and government industries, where compliance with GDPR and HIPAA requirements is essential.
Suppose you need more than regulatory requirements and potential fines to convince you of the importance of an identity governance framework. In that case, your organization can learn a lesson from these recent incidents and shocking statistics:
- Google Cloud's 2023 Threat Horizons Report found that 86% of breaches involve stolen credentials, and credential issues account for over 60% of compromise factors -- which could be addressed with stronger identity management guardrails in place at the organization level.
- According to the 2023 Verizon Data Breach Investigations Report, 74% of all breaches include the human element, involving people either via error, privilege misuse, use of stolen credentials, or social engineering. The report also found that web application attacks account for 25% of breaches, in which hackers leverage stolen credentials and vulnerabilities to gain access to your organization's assets.
- In 2023, the American Bar Association disclosed a hack affecting 1.5 million members whose login credentials, including encrypted password data, had been compromised.
- Video game publisher Activision suffered an alleged phishing attack where an employee's credentials were obtained and subsequently used to infiltrate their system.
5 Key Components of an Identity Governance Framework
Building an effective identity governance framework involves several key components that work together to ensure the integrity and security of your organization's data.
- Assessing Your Organization's Identity Governance Needs
The first step in building an identity governance framework is assessing your organization's needs. This stage involves understanding business processes, identifying critical systems and data, and determining the level of risk associated with user access. You should consider factors such as the size of your organization, the complexity of your IT infrastructure, the number of employees and contractors, and any compliance requirements.
By conducting a thorough assessment, you can identify the areas where identity governance controls need to be strengthened and develop a roadmap for implementation.
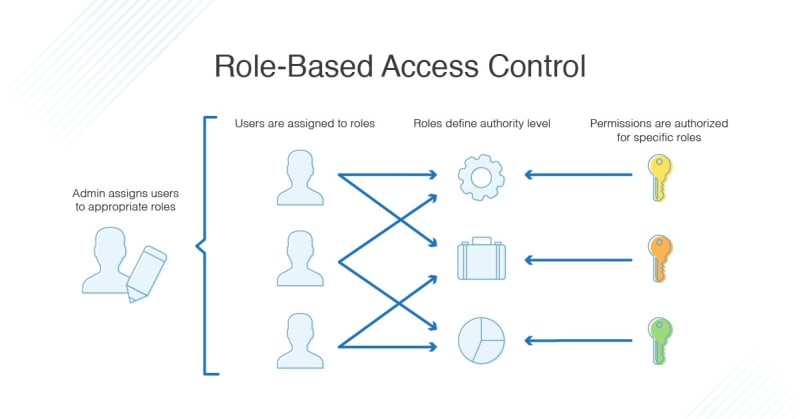
- Defining Roles and Responsibilities
To define roles and responsibilities, you should consider the different job functions within your organization and the level of access required for each role. You can do this using role-based access control (RBAC), where access permissions are assigned based on predefined roles and responsibilities. By implementing RBAC, you can simplify managing user access, improve security, and reduce the risk of unauthorized access.
- Implementing Identity Access Controls
Once you have defined roles and responsibilities, the next step is implementing identity access controls. Identity access controls are the mechanisms that enforce the defined roles and responsibilities and manage user access to critical systems and data.
There are several types of identity access controls, including:
- Authentication: This verifies the identity of users accessing the system, typically through usernames and passwords, biometrics, or multi-factor authentication.
- Authorization: This determines the level of access granted to authenticated users based on their roles and responsibilities.
- Privileged Access Management (PAM): This controls and monitors privileged accounts with elevated access rights to prevent misuse or unauthorized access.
- User Provisioning: This automates the process of creating, modifying, and disabling user accounts, ensuring that access rights are granted and revoked in a timely manner.
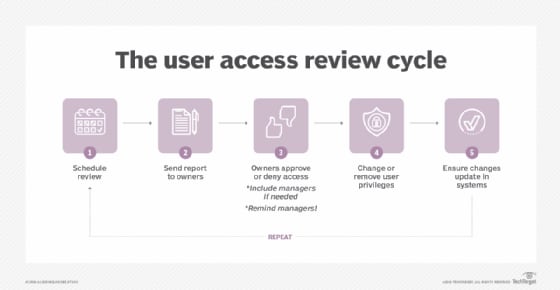
- Monitoring and Auditing Identity Activities
It's essential to regularly monitor user activities and conduct audits to detect and respond to suspicious or unauthorized behavior promptly. Monitoring can be achieved through the use of security information and event management (SIEM) systems, which collect and analyze logs from various systems to identify potential security incidents. Additionally, you can employ user behavior analytics (UBA) to detect anomalies in user behavior and identify potential insider threats.
You can conduct regular audits to review user access rights, identify any discrepancies or violations, and ensure compliance with regulatory requirements. Audits also provide an opportunity to assess the effectiveness of the identity governance framework and make necessary improvements.
- Continuously Improving Your Identity Governance Framework
Your organization must regularly review and update identity governance policies and controls to align with industry best practices and regulatory requirements. Identity governance also requires staying up-to-date with the latest trends and technologies to leverage new opportunities for enhancing security and efficiency.
By continuously improving the identity governance framework, you can stay one step ahead of cyber threats and ensure the long-term effectiveness of your security measures.
7 Best Practices for Implementing an Identity Governance Framework
When implementing identity governance, there are several best practices to consider:
- Executive Sponsorship: Obtain support and buy-in from executives to ensure that identity governance is prioritized and receives the necessary resources.
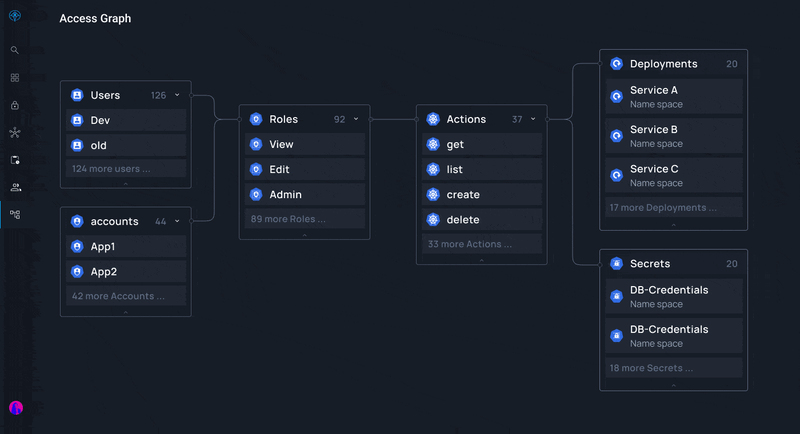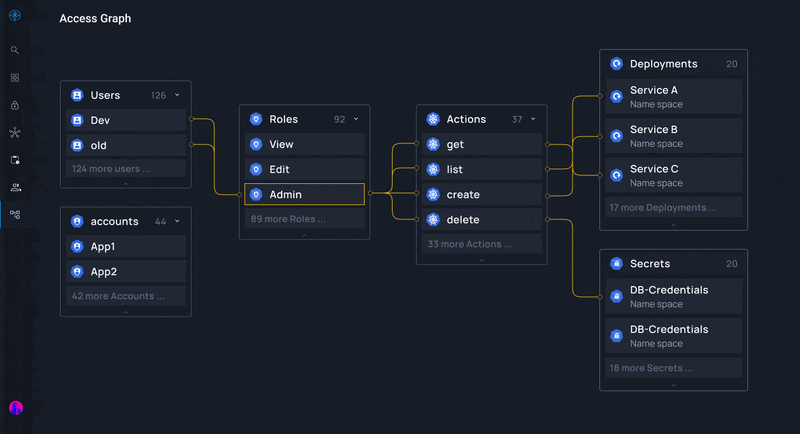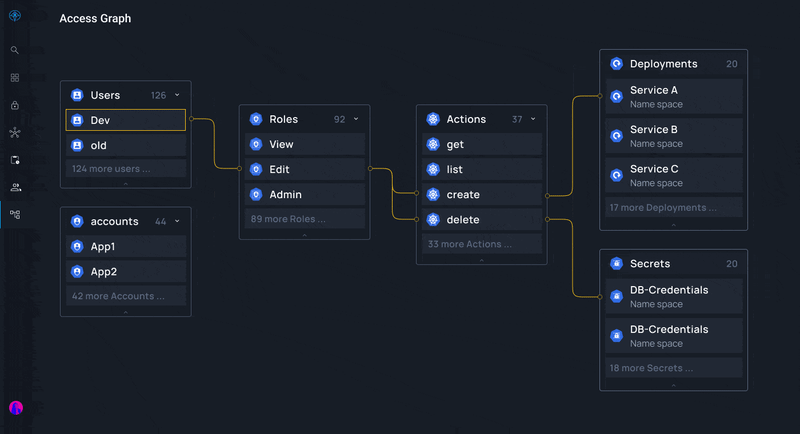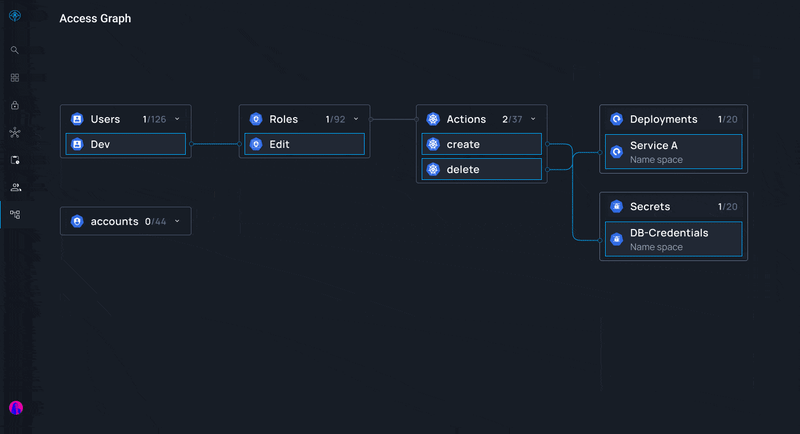
- Third-party Tools: Utilize tools such as Apono that make it easy to create, manage, provision, audit, and approve or deny access requests in one centralized location.
- Cross-functional collaboration: Involve stakeholders from various departments, such as IT, HR, and legal, to ensure a comprehensive and holistic approach to identity governance.
- User Education and Awareness: Provide training and awareness programs to educate users about the importance of identity governance and their role in maintaining security.
- Regular Assessments and Audits: Conduct regular assessments and audits to identify vulnerabilities and areas for improvement.
- Automation: Leverage identity governance tools such as Apono and automation to streamline processes and reduce manual errors.
- Regular Updates and Patching: Stay up-to-date with the latest security patches and updates for identity governance systems to address any vulnerabilities.
Leverage Apono For Identity Governance
Remember, identity governance is an ongoing process that requires continuous improvement and adaptation to changing circumstances. By staying proactive and implementing best practices, you can stay ahead of cyber threats and ensure the long-term effectiveness of your identity governance framework.
Apono's cloud-native access management solution helps you overcome compliance bottlenecks so you can meet HIPAA, SOC2, GDPR, and other identity governance requirements without investing time and labor. Apono is scalable and automated, enabling environment-level policies and tracking identities across numerous applications and cloud assets.
Get started with Apono for free.