The last ten years have seen a revolution in how enterprise software companies have rolled out their solutions. Previously, the default offering was to implement a Commercial Off-the-Shelf (COTS) software package running on a client's on-premise hardware infrastructure. But that's now old hat -- nobody is doing that anymore. Now, the popular solution is to store your data and the software "in the cloud." This innovative approach is called Software as a Service or SaaS.\
SaaS is projected to grow at an annual rate of 20%, bringing its market share to around one-third of all enterprise software sales. The following diagram shows those market sectors where SaaS adoption has become most prevalent.\
 \
\
SaaS may shrink your operating costs, lead to faster innovation, and reduce company expenses on obsolete technologies, but it is sadly not the golden goose. Well, not yet anyway. The trouble is that those mighty cloud service providers like Amazon Web Services, Microsoft Azure, and Google Cloud have failed to place enough emphasis on one specific element of their deliverables---security.\
Cyber breaches have resulted in annual financial losses of three billion USD. US computer giant IBM has assessed the average loss per breach at 4.24 million USD. And, the total damage estimate for such attacks is predicted to reach 10.5 trillion USD by 2025.
While SaaS is undoubtedly the "way to go," there is still much work to be done to protect SaaS customers, their clients, and the cloud vendors themselves from the clutches of the unscrupulous cyber criminal. Much still needs to be done to convince SaaS vendors and their customers that cloud vendors really can manage their security challenges. The following diagram shows the levels of mistrust shown by enterprises towards SaaS suppliers.\
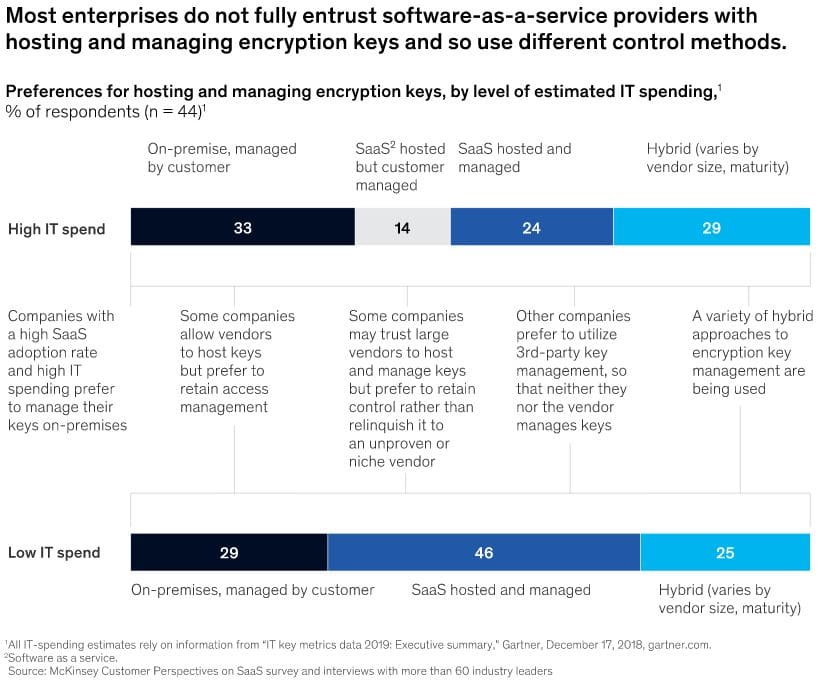 \
\
This article describes the best practices that SaaS manufacturers and their cloud vendors should follow to galvanize this rapidly expanding area of enterprise software delivery.\
What are the top Data Security Challenges of SaaS Applications?
The data security challenges faced by cloud vendors and their clients are varied. Primary among these is the fact that each SaaS producer is a unique entity with its own structure, priorities, and client base. This makes the job of plugging any security vulnerabilities a significant test for all the parties involved in the process. In addition to the end users, this also includes SaaS company developers, SecDevOps, and sales and marketing departments.\
Traditionally, these sectors have had limited interaction, but due to the essential requirement to address these security concerns, greater emphasis is now being placed on internal cooperation.\
SaaS functionality and business innovation have taken precedence over security, a direction that SaaS companies are now being forced to change.\
Another area affected by poor SaaS security provision is regulatory reporting, such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the System and Organization Controls (SOC) 2 Type II standard. These regulatory standards must also be managed by any cloud vendor/SaaS solution.\
Here are a few examples of other data security issues to look out for:
\
Security Misconfiguration
If a computer application component is configured incorrectly, it can become vulnerable to cyberattack. These misconfigurations can result from human error or be created externally by cybercriminals piggybacking into the system via legitimate pathways and corrupting critical elements to enable illegitimate access.\
Poor Monitoring and Logging
Logging and monitoring are regularly performed by a SaaS company's Security Operations Center (SOC) using Security Incident and Event Management (SIEM). Weakness in these two focal points will result in increased cyberattack vulnerability. SaaS applications have increasingly moved to the Cloud. As a result, the way they store data has become distributed, making monitoring data streams in real-time a real challenge. This is even more so the case for organizations handling personal data that needs to comply with privacy regulations.\
Limited Cloud Usage Visibility
Serious cyberattacks can occur when a SaaS company lacks the ability to determine whether its cloud service usage and capabilities are robust.\
Account Hijacking
The hijacking of a cloud computing account is one of the most common forms of cyber breach, normally called a Ransomware attack. Having gained access to a target network, the cybercriminal is then in a position to extort funds out of a company. Failure to do so can result in data and intellectual property damage and loss.\
Lack of Cloud Security Architecture
A company with a compromised cloud security architecture opens itself up to significant damage from cyber threat actors. All companies working in the SaaS space must construct a bottom-up security design that can be integrated with their cloud services supplier.\
8 data security best practices for SaaS applications
1. Discover and map your SaaS data
The first priorities for the SaaS security professional are the secure discovery, classification through tagging, mapping, and monitoring of all data in transit, in use, or at rest. SaaS developers must see, follow, and protect their cloud shadow and unmanaged data. The data navigation process is critical in knowing where your data is at all times and providing it with the maximum level of protection. This is more easily achieved with the Polar Security solution which detects and follows your sensitive known and shadow data and then automates data labeling to continuously highlight valuable and sensitive data stores at scale.\
2. Data Encryption
Cloud apps are not protected by traditional methods such as firewalls, so they must rely on data encryption and key management. Many customers are not comfortable leaving this vital task to data vendors and prefer to manage their own keys through a local hardware facility. Data "in motion" can be protected using Transport Data Encryption (TDE). Still, other data transfer via HTTP or FTP can be risky, so it should be protected using methods such as Transport Layer Security (TLS).\
3. Matching Controls to your Risk Level
Security controls can be defined according to the acceptable levels of risk of the SaaS vendor. Any control over data access, processing, and monitoring will inevitably impact on system performance, and SaaS providers will have to match one against the other. In the past, this balance was skewed to business performance, but due to high-profile security breaches, the pendulum has swung back and a more balanced approach is now being defined.\
4. Effective Identity and Access Management Controls
Identity and Access Management (IAM) tools prove that users are who they are supposed to be. There is a critical requirement for SaaS users to be able to integrate with IAM tools. Enterprise users do not want a different password whenever they access another part of an enterprise-wide platform. Sophisticated access control determining who accessed what and when is an essential element in any IAM system.\
5. Logging and Monitoring
It is vital to log all access attempts into the SaaS system, both failed and successful. The same is true of any data amendments. Such activity is essential in mitigating data breaches and for establishing future security plan arrangements.\
6. Use a Key Vault Service
Key vault services, such as Norton's Norton Password Manager, provide a service where any authentication credentials generated by a user can be securely stored and activated when required. Such services also offer a facility to automatically generate random usernames and passwords.\
7. Use a Security-first Software Development Life Cycle
Using a safe security-prioritized Software Development Life Cycle (SDLC) brings a security focus into the software development process. In addition, the use of threat modeling and penetration testing can raise the security profile of the SDLC even further.\
8. SaaS Security Posture Management (SSPM)
SSPM is designed to block unintentional vulnerabilities that occur in the SDLC. SSPM provides a unified level of transparency across an entire cloud environment. It avoids the necessity to check multiple discrete endpoints from a range of vendors. This process reduces misconfigurations while increasing time-to-market delivery. SSPM regulates and automates SaaS data security.\
Keep your SaaS application data secure with Polar Security
There is no doubt about it, SaaS enterprise software is here to stay. It provides many benefits to software vendors, including lowered costs, reduced time to market, the avoidance of hardware obsolescence, and enhanced scalability. However, this improvement does not come without a cost; all too often, that cost is security.\
Fortunately, this issue is not insurmountable, and solutions exist to manage this risk. Polar Security's automated data store inventory and data flow audits provide a method of preventing the loss of exposed SaaS data and mitigating the risk of ransomware attack. In addition, the Company provides a solid means of avoiding compliance violations.


















