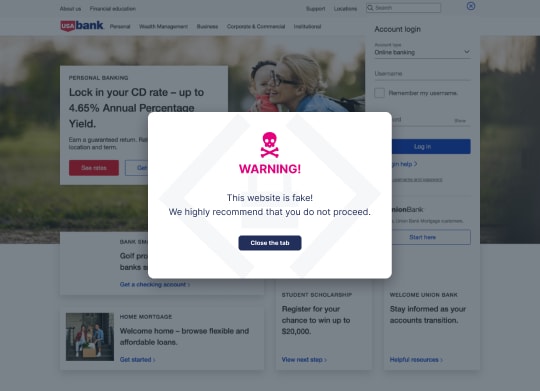
The thriving online marketplace holds boundless opportunities for businesses and consumers. But lurking beneath the surface of convenient digital transactions is a persistent threat: ecommerce fraud. Consider the unsuspecting customer who stumbles upon what looks like your online store, snags a coveted deal, and enters their payment details---only to find out later that a fraudster has stolen their financial data from a spoofed website.
Fraudsters employ an ever-evolving arsenal to exploit vulnerabilities and siphon off profits---and it's working. In 2023, ecommerce fraud losses are predicted to reach a staggering $38 billion and rise to $91 billion by 2028, highlighting the urgent need for robust countermeasures.
Aside from the financial losses to merchants and shoppers, ecommerce fraud undermines consumer trust in online shopping, which is crucial for the digital economy. Fortunately, you can protect your ecommerce business by implementing these twenty-one fraud prevention policies now.
Why Ecommerce Fraud Is Rising
Before learning how to prevent ecommerce fraud, it's essential to understand why it has become such a widespread threat. Ecommerce fraud thrives among cybercriminals due to the allure of:
- Low Barrier to Entry -- The anonymity and relative ease of online activity make it a tempting playground for perpetrators with minimal technical expertise.
- High Potential Gains -- A single successful attack can yield significant financial rewards, especially with high-value transactions or targeted vulnerabilities.
- Global Reach -- The internet's borderless nature allows fraudsters to operate across geographical boundaries, further increasing their potential gains and complicating law enforcement efforts.
Common Types of Ecommerce Fraud
Businesses and consumers encounter ecommerce fraud in diverse forms, each demanding a tailored defense strategy:
Account Takeover (ATO)
Hackers compromise user accounts, gaining access to sensitive information and wreaking havoc on shopping sprees.
Chargeback Abuse
Fraudsters exploit chargeback policies by claiming fraudulent transactions or disputes to receive undeserved refunds.
Payment Fraud
Stolen credit card details or forged identities enable unauthorized transactions, draining funds from businesses and customers.
Phishing Attacks
Deceptive emails masquerading as your brand trick customers into divulging sensitive information like passwords, credit card details, or social security numbers.
Refund Scams
Deceptive tactics like returning stolen goods or claiming fake damage are employed to secure illegitimate refunds.
Website Spoofing
Website spoofing thrives on exploiting human trust and security gaps. Hackers mimic your brand website's look-and-feel, lure customers with irresistible deals, and steal their sensitive information like credit card details and login credentials.
21 Ecommerce Fraud Protection Policies to Implement Now
Now that we know why ecommerce fraud is rising and how fraudsters accomplish it, let's review fraud protection policies you can implement now to bolster your defenses.
Deploy the Digital Guard Dogs
1. Real-Time Transaction Monitoring
Track every transaction in real-time, analyzing factors like location, velocity, and spending patterns. This allows for immediate flagging of suspicious activity, like a sudden surge of purchases from an unusual location, before it leads to financial loss.
2. Velocity Checks
Set limits on transaction frequency and spending amounts based on customer profiles and historical data. Exceeding these limits triggers alerts for further investigation, preventing fraudsters from exploiting stolen credentials for a shopping spree.
3. IP Verification
Identify and validate the location of each transaction. Inconsistencies between billing and shipping addresses or suspicious IP addresses associated with known fraud hubs can pinpoint potential threats.
4. Device Fingerprinting
Analyze unique hardware and software characteristics of the device used for transactions. This helps identify attempts to use stolen credentials or shared devices for unauthorized access.
5. Guard Your Authentic Website with Memcyco
Go beyond traditional security measures to deploy Memcyco's dedicated website spoofing prevention solution. It guards your digital assets with real-time brand impersonation monitoring, alerting, and protection.
Most importantly, Memcyco prevents your customers from becoming victims of brand impersonation scams through an impostor site alert that appears when users access spoofed or cloned versions of your ecommerce website---ensuring your brand remains untarnished and transactions stay secure.
Lock Down the Gates
6. Strong Password Policies
Enforce minimum password length, complexity requirements, and regular password changes to make it harder for hackers to crack user accounts. Consider implementing password managers and multi-factor authentication for additional security.
7. PCI Compliance
Adhere to PCI (Payment Card Industry) Data Security Standards to ensure secure storage, transmission, and handling of customer payment information. PCI compliance demonstrates your commitment to data protection and minimizes the risk of costly penalties.
8. Regular Software Updates
Install security patches and software updates promptly to address vulnerabilities exploited by hackers. This applies to your ecommerce platform, plugins, and any third-party integrations.
9. Scan for Vulnerabilities, Viruses and Malware
Conduct regular vulnerability scans to identify and patch weaknesses in your website and server infrastructure before cybercriminals can exploit them. Employ an up-to-date antivirus solution to scan your system for lurking viruses and malware like banking trojans.
Arm Your Customers with Knowledge
10. Phishing Awareness Training
A worthwhile investment is customer education on identifying phishing emails and suspicious websites. Train them to avoid clicking on unknown links, opening suspicious attachments, and sharing personal information through unverified channels.
11. Secure Payment Practices
Encourage customers to use strong passwords, avoid public Wi-Fi for online transactions, and be cautious about sharing payment information over the phone or email. Provide clear instructions on secure payment methods and dispute resolution procedures.
Embrace Dynamic Defense and AI Tools
12. Risk-Based Authentication
Implement tiered authentication based on transaction risk. Low-risk transactions may require simple password verification, while high-risk transactions, like large purchases or those originating from unusual locations, may require additional steps like multi-factor authentication or manual review.
13. Behavioral Analytics
Employ AI-powered tools to analyze customer behavior patterns and identify anomalies that suggest potentially fraudulent activity. This can help detect emerging threats that traditional rule-based systems might miss.
14. Machine Learning Fraud Detection
Analyze historical data with machine learning algorithms to identify patterns indicative of fraudulent activity. This allows for proactive detection and prevention of emerging cyber threats before they can cause damage.
15. Adaptive Fraud Scoring
Utilize AI-powered solutions that dynamically adjust fraud risk scores based on real-time data and evolving fraud patterns. This helps focus resources on the most likely threats and minimize false positives.
Adapt to the Evolving Threat Landscape
16. Security Trend Monitoring
Stay informed about emerging fraud trends and cybercrime tactics. Utilize industry resources and threat intelligence reports to keep your defenses updated and address new vulnerabilities proactively.
17. Regular Review and Audits
Conduct periodic security reviews and audits to identify potential weaknesses and ensure your fraud prevention policies remain effective. Adapt your strategies as needed to match the evolving threat landscape.
Partner with Experts
18. Fraud Prevention Services
Consider collaborating with specialized fraud prevention companies for comprehensive protection and access to advanced expertise. These companies can provide advanced fraud detection tools, threat intelligence, incident response support, and third-party audits.
19. Penetration Testing
Engage professional penetration testers to simulate cyberattacks and identify vulnerabilities in your defenses. This allows you to address weaknesses before real attackers exploit them.
Build Awareness and Transparency
20. Clear Security Policies
Publish clear and easily accessible security policies that outline your data protection practices, customer authentication procedures, and fraud prevention measures. This builds digital trust and confidence with your customers.
21. Transparency in the Event of Fraud
If a fraud incident occurs, communicate openly and transparently with your customers. Explain what happened, the steps you are taking to address the issue, and the measures you are implementing to prevent future occurrences.
Proactive Protection Is Your Best Weapon
Ecommerce fraud is a cunning adversary, but you hold the power to prevent it. Implementing these ecommerce fraud prevention policies will help your organization build a robust defense while creating a secure, trustworthy online shopping experience for customers. Proactive protection is your best weapon in the fight against fraudsters.
To proactively defend your website against spoofing and brandjacking attacks, consider Memcyco's innovative agentless solution---the only one offering real-time defense during the critical "window of exposure" from when a fake site goes live until it's taken down. With a forge-proof authenticity mark identifying your genuine site, Memcyco offers ecommerce businesses and their shoppers safety from brand impersonation fraud.
Request a free Memcyco demo today to experience the transformative power of proactive website spoofing prevention.