Most enterprises recognize IAM strategies as an effective way to mitigate security challenges, but turning intention into action is another story. Why do some businesses still allow their employees to use '12345' as a password despite knowing the financial and reputational implications of a data breach?
61% of all breaches involve credentials, and while it's hard to believe, '12345' and 'password1' continue to top the list of most-used passwords. Creating a strong password isn't a silver bullet, but it does represent a critical and often overlooked aspect of IAM and the importance of robust best practices.
In this article, we'll delve into what IAM is, its benefits, and its components, and we'll lay out essential best practices for 2023.
What Is IAM?
IAM (Identity and Access Management) is a cybersecurity practice that controls user identities and access permissions in computer networks. IAM ensures that the right users and devices can access the right resources at the right time by automating identity management and enhancing security through tools like MFA (multi-factor authentication) and SSO (single sign-on).
Some other authentication methods are:
- Multi-factor authentication (MFA): Requires users to provide two or more verification factors, such as codes, biometrics, or passwords, to gain access to a resource.
- Biometric verification: Uses unique physical characteristics like fingerprints or facial features for identity confirmation.
- Token-based authentication: Employs physical or digital tokens to generate temporary access codes.
IAM in On-premises Vs. Cloud Environments
IAM differs in on-premises and cloud environments. In on-premises setups, IAM controls access to internal systems and physical resources. IAM in cloud environments extends to cloud-based applications and services, accommodating remote access and scalability.
Why Is IAM Important?
By ensuring proper user authentication, authorization, and audit, IAM has several advantages for organizations.
Enhanced Security and Compliance
IAM ensures that access privileges are granted based on policies, guaranteeing proper authentication, authorization, and audit of individuals and services. This helps companies adhere to regulatory standards like GDPR and PCI-DSS, reducing the risk of data breaches and demonstrating compliance during audits.
Efficiency and Cost Savings
Automating IAM streamlines user access management, decreasing manual effort, time, and expenses. This efficiency allows businesses to operate more smoothly and focus resources on core activities rather than access management.
Reduced Data Breach Risk
IAM is an effective strategy for data loss prevention caused by both internal and external threats. It adds layers of authentication beyond passwords and enforces policies that limit unauthorized lateral movement, thwarting potential threats.
Facilitates Digital Transformation
With the evolving landscape of remote work, multi-cloud environments, and IoT devices, IAM centralizes access management for various user types and resources. This enables secure access without compromising user experience, supporting digital transformation efforts.
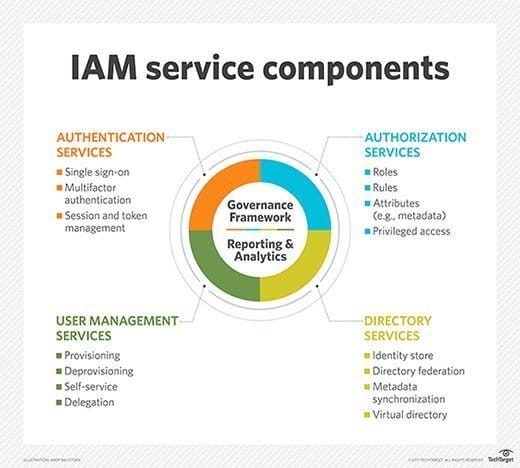
What Are The Components Of IAM?
The IAM framework is essential for maintaining organizational efficiency and securit. Here are some components that it's made up of.
Authentication: This is where users prove their identity to access resources. It involves unique identifiers like usernames, passwords, fingerprints, or even smart cards. Multifactor authentication (MFA) adds extra layers of security, ensuring a robust login process.
- Authorization: Once a user is authenticated, authorization sets the boundaries. It determines what a user can access based on their role. Think of it as the bouncer at the door, only letting approved users in.
- Administration: This manages user accounts, permissions, and password policies. Administration is the foundation for authentication and authorization. It ensures accounts are secure, and it's where user roles and groups are handled.
- Auditing and Reporting (A&R): A&R keeps track of users' actions. It examines and records access logs and activities to detect unauthorized or suspicious actions.
10 IAM Best Practices For 2023
By implementing these best practices and tips, you'll establish a strong foundation for identity and access management, ensuring the security of your systems, data, and users.
1. Implement a Zero-Trust Approach to Security
Zero trust is a security model that rejects the notion of implicit trust within networks and requires continuous verification of users and devices. This approach is crucial because it minimizes the risk of unauthorized access, especially in a dynamic threat landscape. To implement Zero Trust, start by segmenting your network, requiring MFA for all access, and enforcing strict access controls based on user roles. You could also implement contextual policies, such as only allowing certain types of access from certain locations or devices, for an extra layer of security.
2. Use Multi-Factor Authentication (MFA)
Multi-factor authentication mandates users to provide several forms of identification before accessing systems. It's a vital step, as passwords alone remain susceptible to vulnerabilities. Implement MFA by integrating it into your authentication process, using options like hardware tokens or biometric data as secondary authentication factors. Time-based one-time passwords (TOTP) can be an effective alternative to SMS-based codes, and strategies like this won't cause alert fatigue or burden the user excessively.
3. Adopt the Principle of Least Privilege
The principle of least privilege is core to a zero-trust approach, as it restricts user access to the minimum permissions necessary for their roles. To apply this principle, regularly review user permissions and adjust them based on job requirements (otherwise known as role-based access control), ensuring that users have access only to what's needed for their tasks. Pair this with automated monitoring solutions that continuously scrutinize access rights and flag anomalies, and fine-grained permissions that let you customize access down to specific tasks or projects.
4. Perform Mandatory Awareness Training
Recent research from Stanford University suggests that up to 88% of data breaches could be caused by human error -- ouch. In-person and computer-based security awareness training educates staff on the principles of secure password management, helping them recognize phishing attempts and understand the implications of access control policies. If you run the training regularly and get everyone involved, you can create a security-conscious culture and help break the cycle of compromised credentials.
5. Adhere to Regulatory Compliances
Following regulatory compliance checklists like CCPA and GDPR ensures data protection and privacy, which is vital for maintaining a culture of trust amongst your business and customers. You can stay informed about the latest regulations and ensure your IAM policies and processes align with them. Other essential best practices include staying audit-ready with automated compliance reporting (e.g., using an IAM platform) and User Access Review templates.
6. Go Passwordless
8 out of 10 users find password management difficult. Passwordless authentication reduces the risk of credentials-related breaches, and it usually involves integrating biometric authentication or email-based login with unique codes. But should you get rid of them entirely? The choice is yours. You could alternatively implement a strong password policy by setting requirements for complexity, length, and rotation, and you can utilize advanced password management tools to help you do this.
7. Run Penetration Tests
Efficiency, effectiveness, and productivity are the golden trio of a successful IAM strategy, and automated and non-automated penetration tests are indispensable tools for evaluating these three pillars of your IAM framework. Automated pentesting tools rapidly scan for well-known vulnerabilities and provide quick insights into potential security gaps, helping alleviate some workload and support ongoing vulnerability management. Non-automated (or manual) testing enables experts to catch complex, context-sensitive threats, especially after significant system updates or access control changes.
8. Centralize Log Collection
Centralized log collection simplifies monitoring and auditing for quick incident response and compliance. Utilize cloud-based or on-premises log storage solutions that aggregate logs from various data sources in real-time. This best practice will also help your compliance efforts too, as you will gain advanced analytics and alerting capabilities on suspicious activities.
9. Choose the Right IAM Security Platform
Selecting the right IAM platform is critical for effective security management. You'll need to choose one that offers end-to-end coverage and visibility across your entire access journey to your business assets. Otherwise, you only get a fraction of the story. Deployment is also a factor -- when it comes to access control, you can't afford any downtime or mistakes, so choosing a solution with fast and flexible deployment and integration options is a good idea. The whole point of an IAM security platform is to offer automated risk monitoring and remediation, or you'll just create more work for your internal team. With that in mind, make sure the solution does what it says on the tin.
10. Implement Time-based access control
Time-based access control is a strategy where user access permissions are restricted based on time constraints. This can help you effectively improve security by ensuring that users can only access resources (systems, applications, and data) when appropriate. Time-based access control helps to reduce risks by reducing the attack surface, increasing operational efficiencies, and, in some cases, is a requirement of compliance standards.
Embrace IAM And Secure Access To Sensitive Information
IAM's complexity is offset by its security advantages, and the need to stay vigilant against threats can't be overstated. When you have tens or even hundreds of employees and thousands of machine identities accessing a vast variety of systems, applications, and assets multiple times a day, IAM can become overbearing for both the users and the administrators.
With Rezonate's identity-centric platform, IAM is radically simple. It offers end-to-end coverage and visibility of all access, from the creation time to the last active session and activity performed. Rezonate helps you see the complete picture of your IAM map, understand the context, and prioritize critical risks such as weak password policies, identity logging through SAML or SSO, Identity compliance checks, and overprivileged identities.
With Rezonate you can easily adhere to IAM security best practices and track your identity maturity program continuously in real time. Get a free demo of Rezonate today.